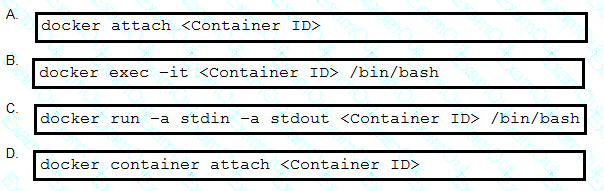
A local Docker container with a Container ID of 391441516e7a is running a Python application. Which
command is used to connect to a bash shell in the running container?
While developing an application following the 12-factor app methodology, which approach should be used in the application for logging?
Users report that they are no longer able to process transactions with the online ordering application, and the logging dashboard is
displaying these messages:
Fri Jan 10 19:37:31.123 ESI 2020 [FRONTEND] [NFO: Incoming request to add item to cart from user 45834534858
Fri Jan 10 19:37:31.247 EST 2020 [BACKEND] INFO: Attempting to add item to cart
Fri Jan 10 19:37:31.250 EST 2020 [BACKEND] ERROR: Failed to add item: MYSQLDB ERROR: Connection refused
What is causing the problem seen in these log messages?
How is an OAulh2 three-legged authentication flow initiated?
An application is developed in order to communicate with Cisco Webex. For reporting, the application must retrieve all the messages sent to a Cisco Webex room on a monthly basis.
Which action calls /v1/messages directly?
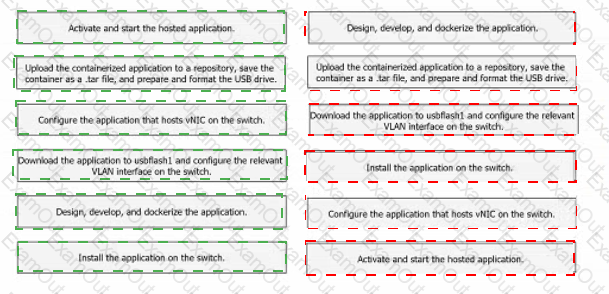
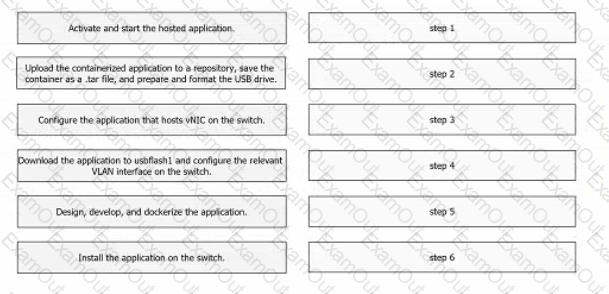
Drag and drop the steps from the left into the order on the right to host a Docker-contained application on a Cisco Catalyst 9000 Series Switch.
Refer to the exhibit.
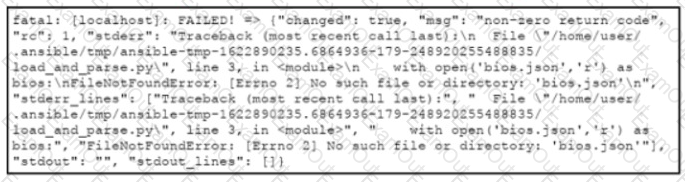
An engineer creates an application that leverages the Ansible framework to provision CPE endpoints that have configuration changes. The application contains an Ansible playbook named provision_cpes.yml that uses the ansible.builtin.script Ansible module to execute these two Python scripts:
•gather and_create.py. which creates a JSON file named bios.json that contains the CPE models and their respective IOS file information
•load and parse.py. which loads the file data and parses it for later consumption
After several successful runs, the application fails. During a review of the Ansible execution logs, the engineer discovers an error output that indicates that one of the stages failed. What is the cause of this issue?
A developer is deploying an application to automate the configuration and management of Osco network files and routers The application must use REST API interface lo achieve programmability. The security team mandates that the network must be protected against DDoS attacks What mitigates the attacks without impacting genuine requests?
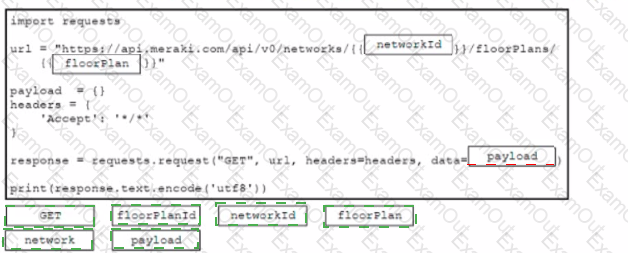
Refer to the exhibit.
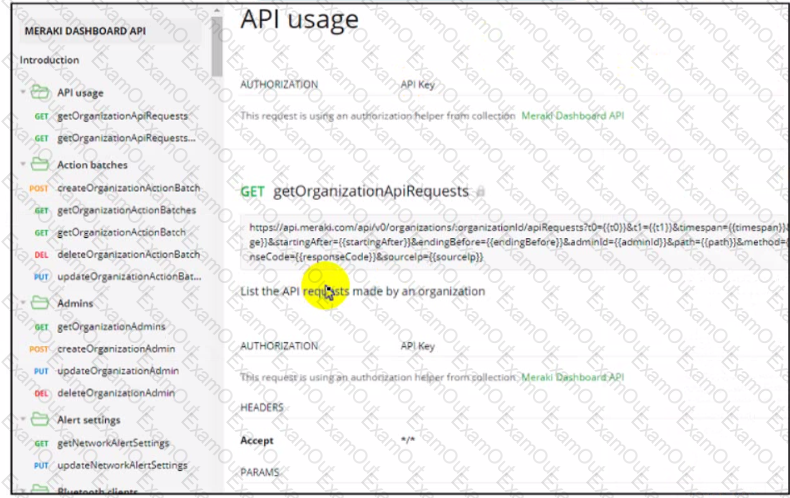
Drag and drop the code from the bottom onto the box where the code is missing to construct a Python script that will retrieve location data Not all options are used.

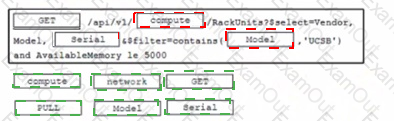
Click on the resource lab in the top left comer to view resources to help with this question An engineer is managing a data center with 6000 Cisco UCS servers installed and running The engineer is asked to identify all resources where the model is in the UCSB family and the available memory is less than or equal to 5 GB Drag and drop the code from the bottom onto the blanks in the code snippet to construct a REST API call to accomplish this task Not all options are used.