Which security approach should be used for developing a REST API?
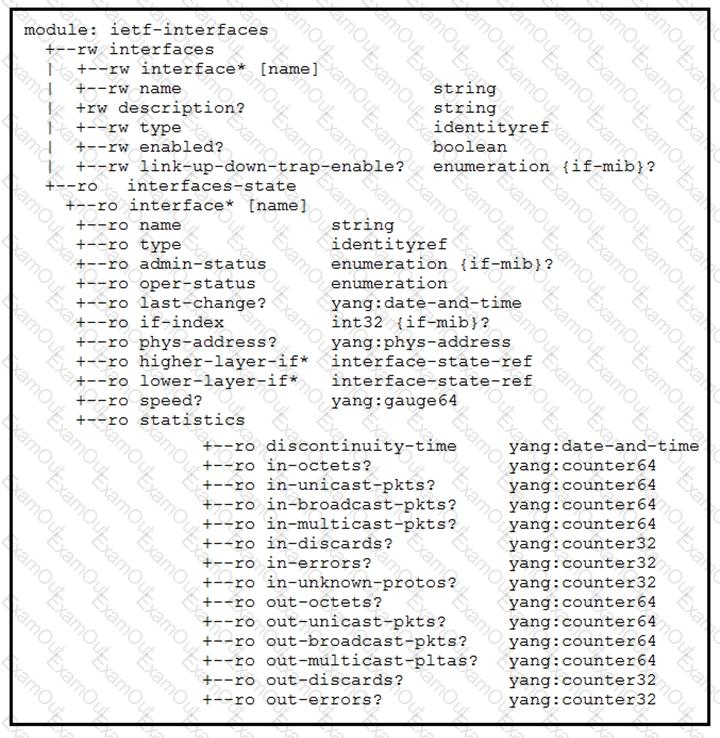
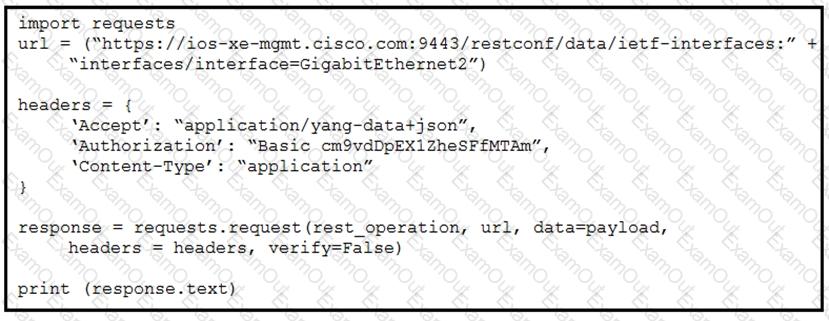
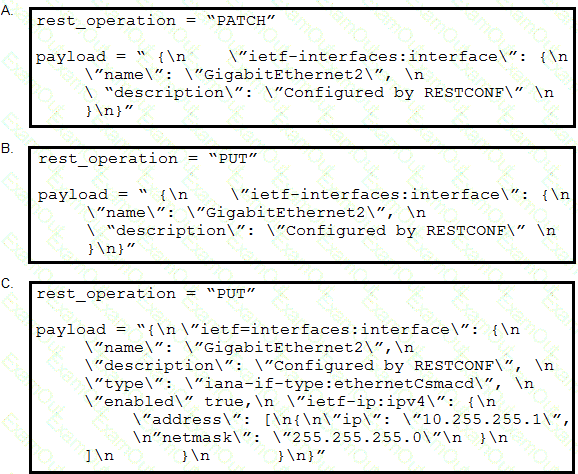
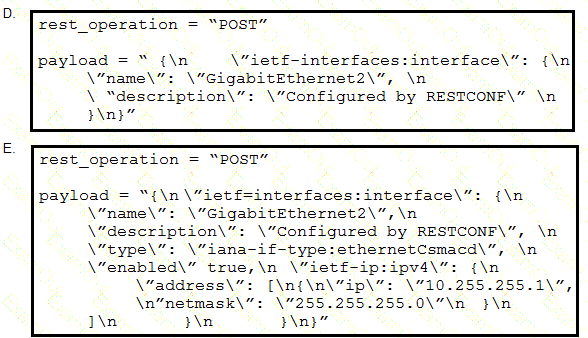
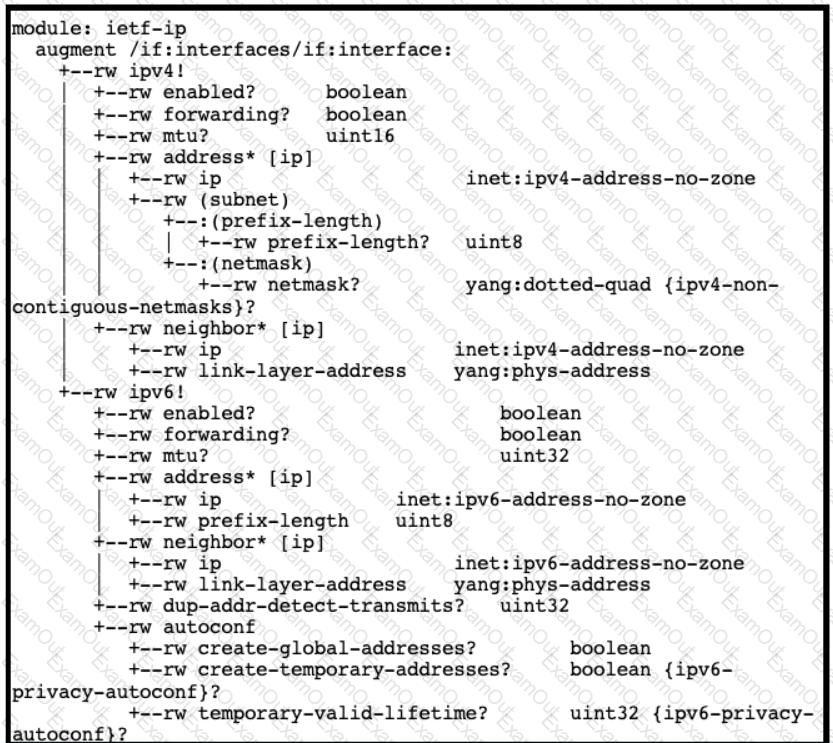
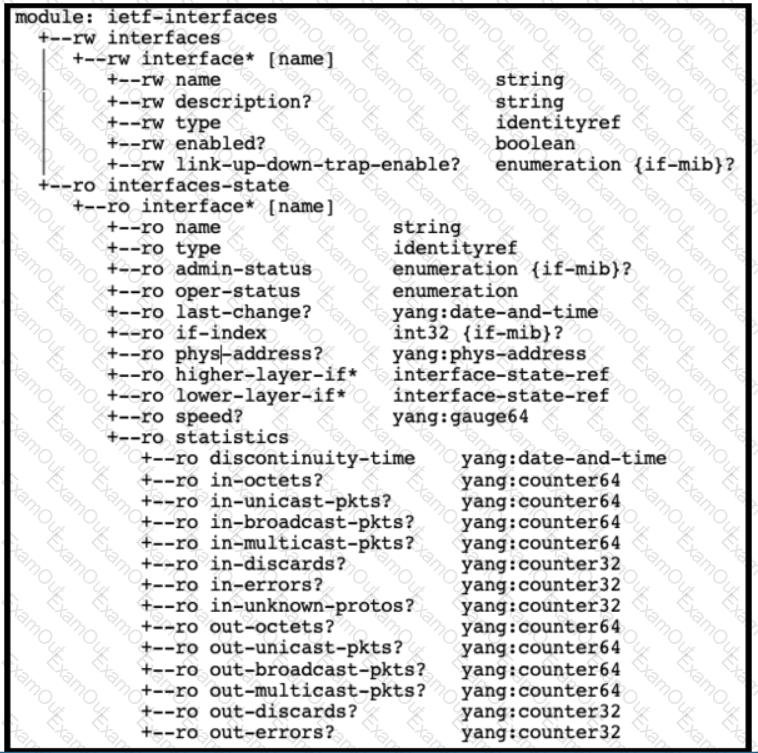
Refer to the exhibits. An interface named “GigabitEthernet2” has been configured on a Cisco IOS XE device. Using RESTCONF APIs as defined by the ietf-interfaces@2014-05-08.yang model, which two combinations of “rest_operation” and “payload” must be added to the Python script to set the “description” to “Configured by RESTCONF”? (Choose two.)
Refer to the exhibit Pipenv is used to manage dependencies The test funs successfully on a local environment. What is the reason for the error when running the test on a CI'CD pipeline?
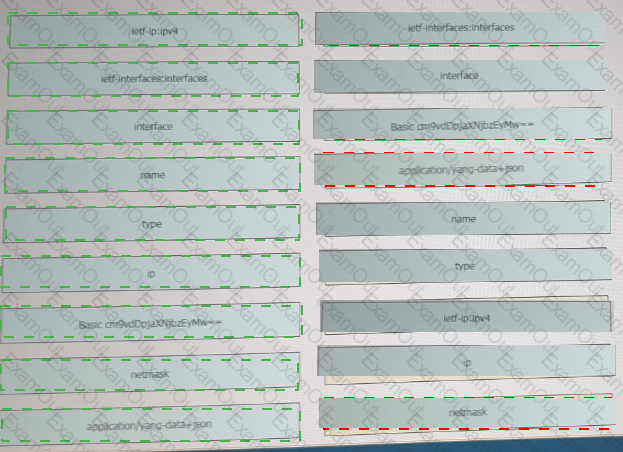
Drag and drop the code from the bottom onto the box where the code is missing to construct a contact tracking application that dynamically returns all the Bluetooth clients on a given Meraki network. Not all options are used.

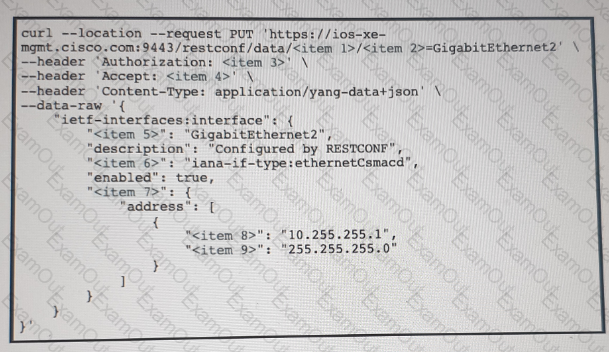
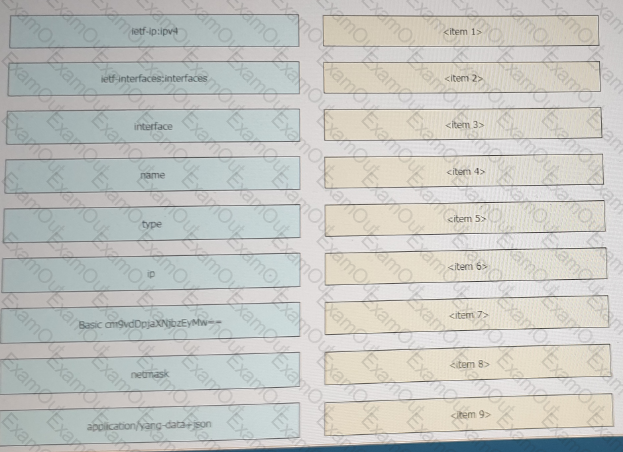
Refer to the exhibit above and click on the resource tabs in the top left corner to view resources to help with this question. Drag and drop the correct code snippets from the left onto the item numbers on the right that match the missing sections in the exhibit to complete the cURL script that will use RESTCONF to update an interface on a CISCO IOS XE device.
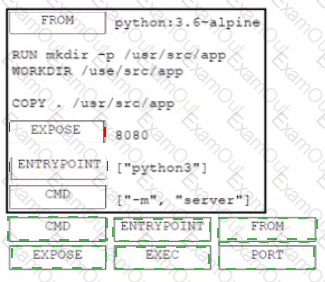
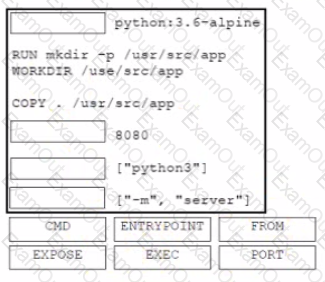
A developer must containerize a Python application to integrate into a prebuilt CD environment by creating a Docker image. It will be hosted as a web application to enable end users from accessing it remotely. Drag and drop the code from the bottom onto the box where the code is missing in the Docker file Not all options are used.
Refer to the exhibit.

A developer must review an intern's code for a script they wrote to automate backups to the storage server. The script must connect to the network device and copy the running-config to the server. When considering maintainability, which two changes must be made to the code? (Choose two.)
The Meraki API URL https://api.meraki.com/api/v0/networks/123456789/ssids/2 has been stored in the environment variable meraki_url and the API key has been stored in meraki_api_key. Which snippet presents the API call to configure, secure and enable an SSID using the Meraki API?
A)
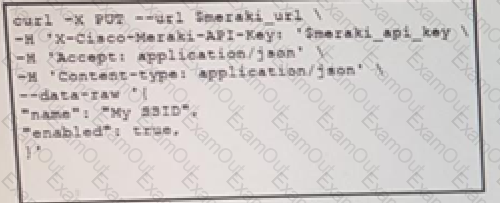
B)

C)

D)

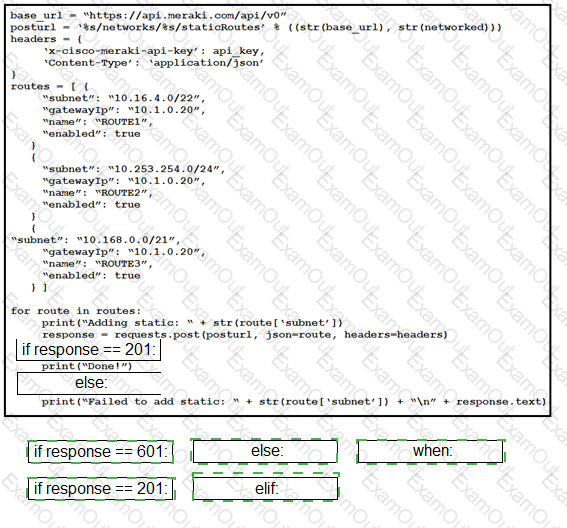
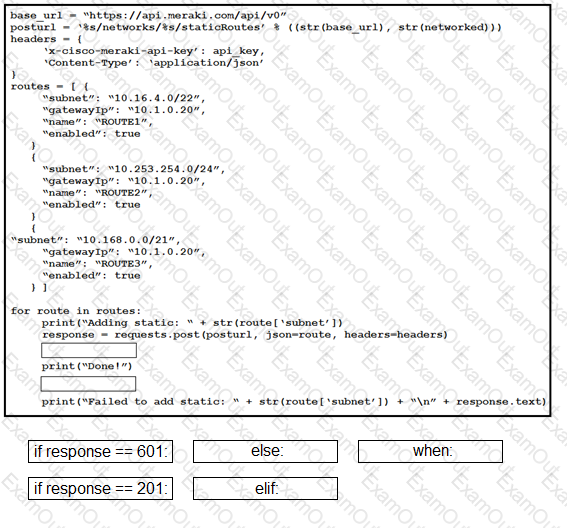
Drag and drop the expressions from below onto the code to implement error handling. Not all options are used.
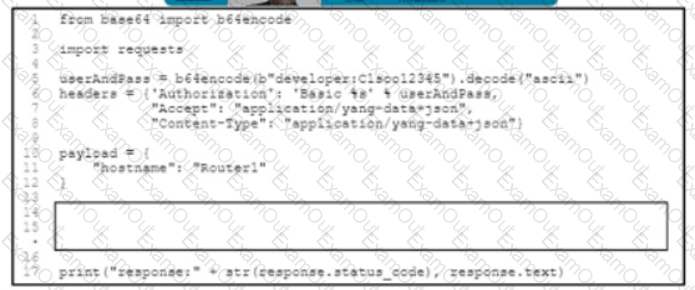
Refer to me exhibit The Python code manages a Cisco CSR 1000V router Which code snippet must be placed in the blank m the code to update the current configuration of the targeted resource?
A)

B)

C)
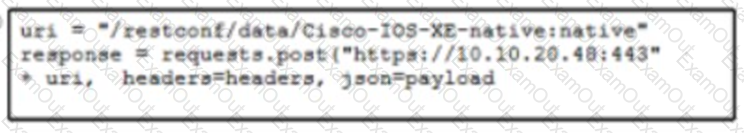
D)