Refer to the exhibit.
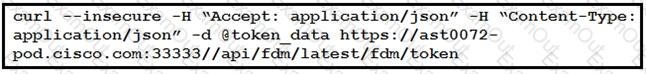
The cURL POST request creates an OAuth access token for authentication with FDM API requests. What is the purpose of the file “@token_data” that cURL is handling?
A client is written that uses a REST API to interact with a server. Using HTTPS as the transport, an HTTP request is sent and received an HTTP response. The response contains the HTTP response status code: 503 Service Unavailable.
Which action is the appropriate response?
What securely stores and encrypts the API keys and tokens that are used for an application deployment?
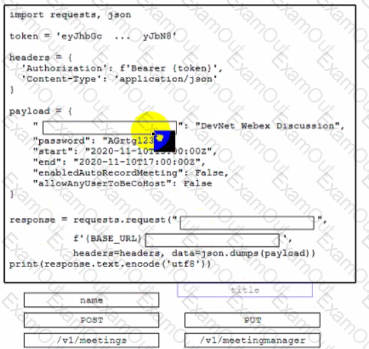
Drag and drop the code snippets from the bottom onto.the boxes where the code is missing to create a Cisco Webex meeting by using the Webex API. Not all options are used.
Refer to the exhibit.
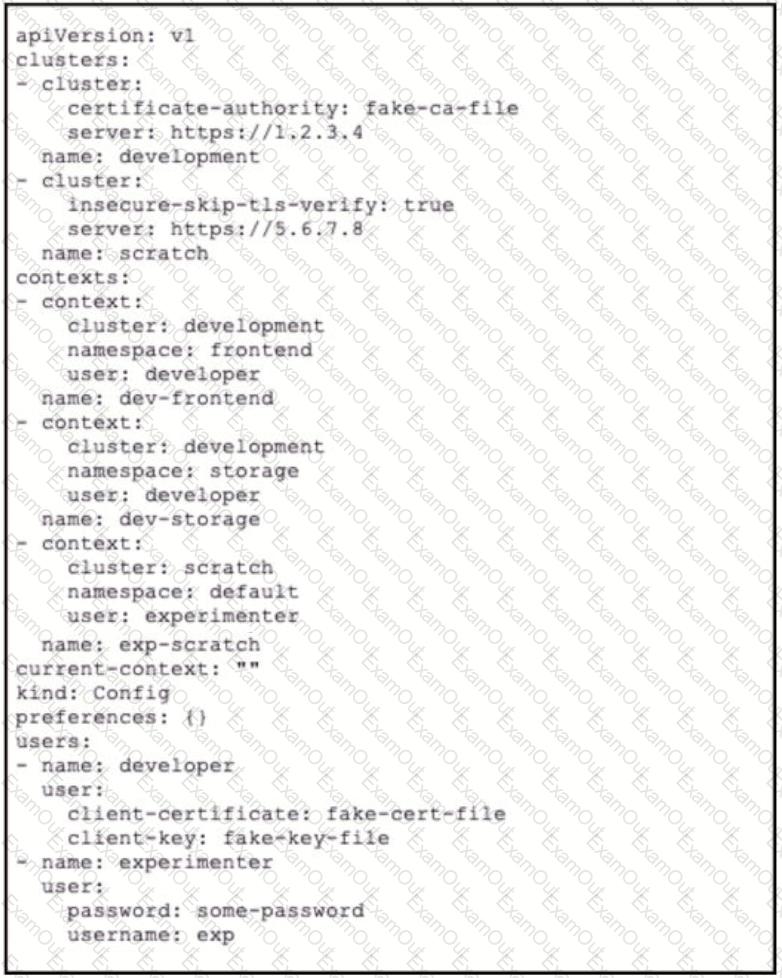
A kubeconfig file to manage access to Kubernetes clusters is shown. How many Kubernetes clusters are defined in the
file, and which cluster FS accessed using username/password authentication rather than using a certificate?
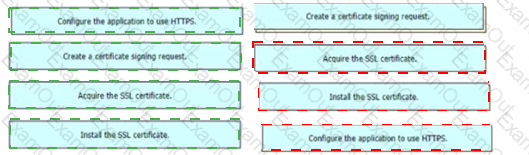
An engineer is developing a web-based application that will be used as a central repository for the HR department The application needs to authenticate user access and encrypt communication. Drag and drop the steps from the left into the order on the right to install an application-specific SSL certificate.
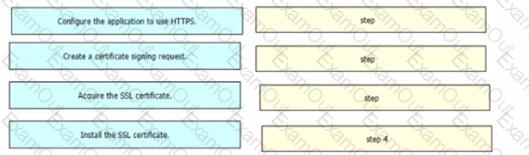
Which type of file is created from issued intermediate, root, and primary certificates for SSL installation on a server?
Refer to the exhibit.
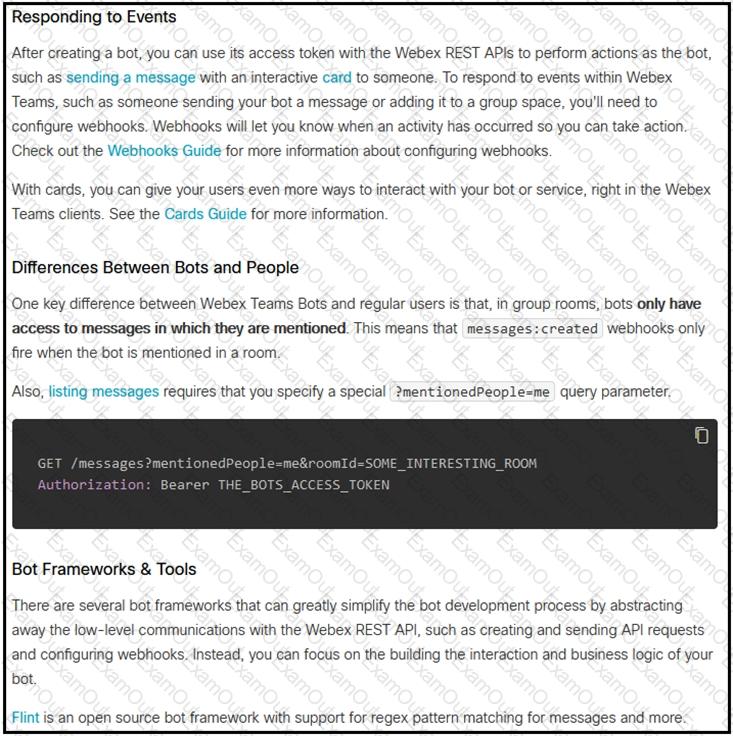
Which set of API requests must be executed by a Webex Teams bot after receiving a webhook callback to process messages in a room and reply with a new message back to the same room?
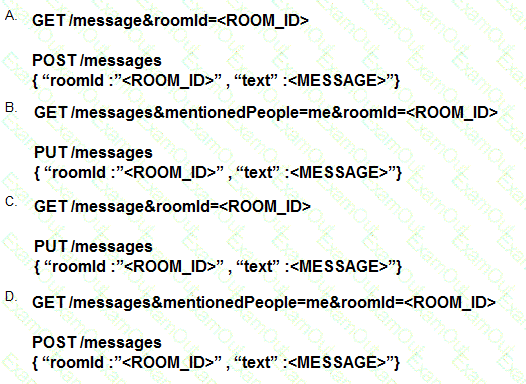
What is a consideration for using gRPC as the model-driven telemetry protocol on a Cisco IOS XE device?
What is a benefit of running multiple instances of a back-end service and using load balancing to distribute the communication between the front-end and back-end services?