Refer to the exhibit.

An application is being developed as an information repository. The application will be used to store details about television shows, including the scenario, year, and category. Which database type must used for high performance for the data structure?
Refer to the exhibit.
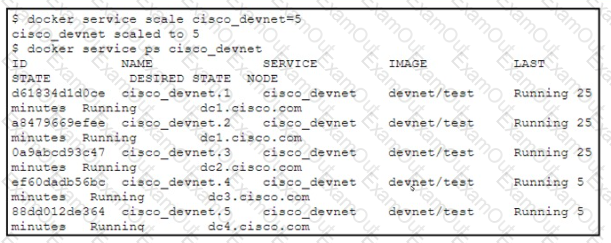
A developer runs the docker service scale command to increase the number of replicas for the cisco_devnet service. The swarm cluster is using a private IP address subnet. The service has these design requirements:
It must be hosted behind a virtual IP address that is reachable from the Internet.
For security reasons, the Docker swarm cluster subnet must not be reachable from the Internet.
Which design approach is used to fulfill the requirements?
A developer needs to configure an environment to orchestrate and configure. Which two tools should be used for each task? (Choose two.)
Refer to the exhibit.
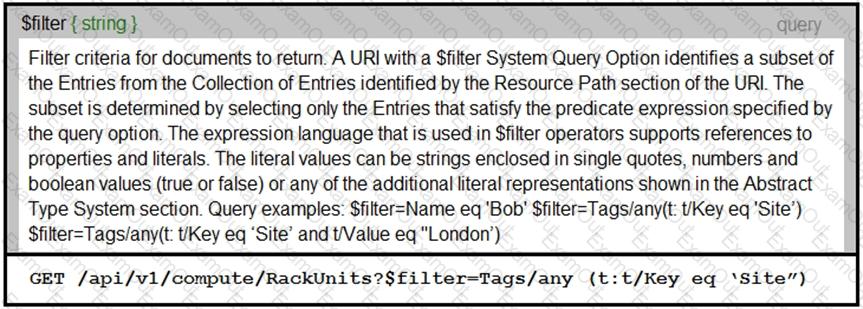
An Intersight API is being used to query RackUnit resources that have a tag keyword set to “Site”. What is the expected output of this command?
A developer has just completed the configuration of an API that connects sensitive internal systems. Based on company policies, the security of the data is a high priority.
Which approach must be taken to secure API keys and passwords?
Refer to the exhibit.

A developer created a Python script to retrieve interface information for the devices in a MeraKi network environment. A security analyst has reviewed the code and observed poor secret storage practices. What is the appropriate password storage approach?
A developer is designing a modem, distributed microservice enterprise application. The application will be integrating with other systems and focus on a large deployment, so control of API calls is necessary. What is the best practice to reduce application response latency and protect the application from excessive use?
Refer to the exhibit.
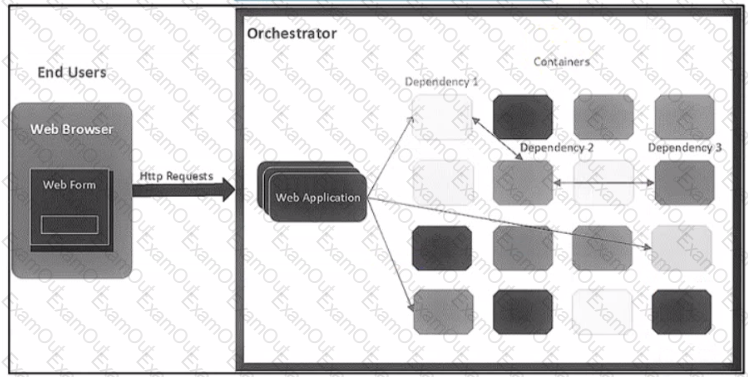
The application follows a containerized microservices architecture that has one container per microservice. The microservices communicate with each other by using REST APIs The double-headed arrows m the diagram display chains of synchronous HTTP calls needed for a single use/request Which action ensures the resilience of the application in the scope of a single user request?
Refer to the exhibit.
An application is created to serve an enterprise Based on use and department requirements, changes are requested quarterly Which application design change improves code maintainability?
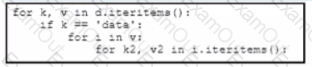
Refer to the exhibit.

Which type of python dependency file is shown?

