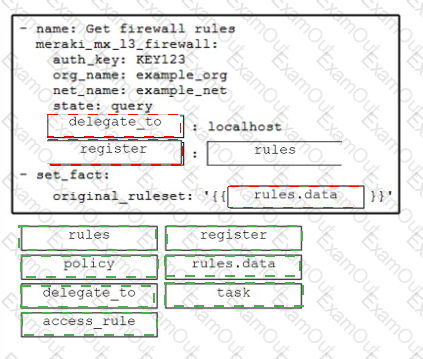
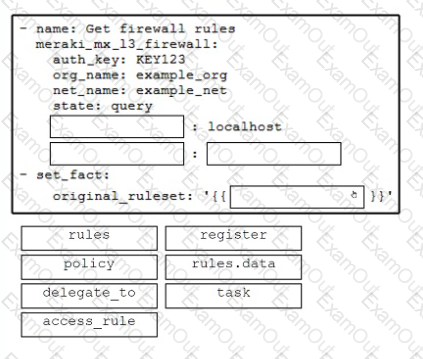
Drag and drop the code from the bottom onto the box where the code is missing in the Ansible script to get the existing firewall rules from Cisco Meraki and store the results to a new variable. Not all options are used.
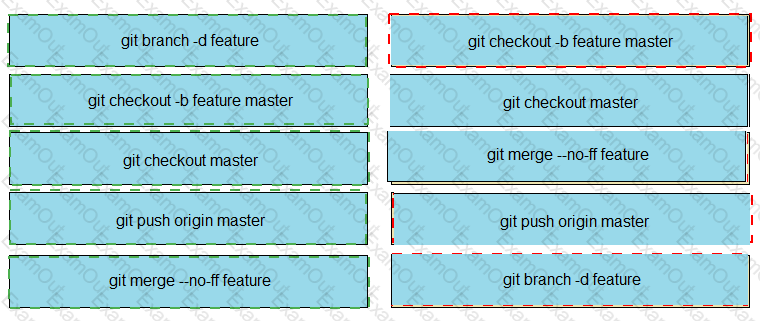
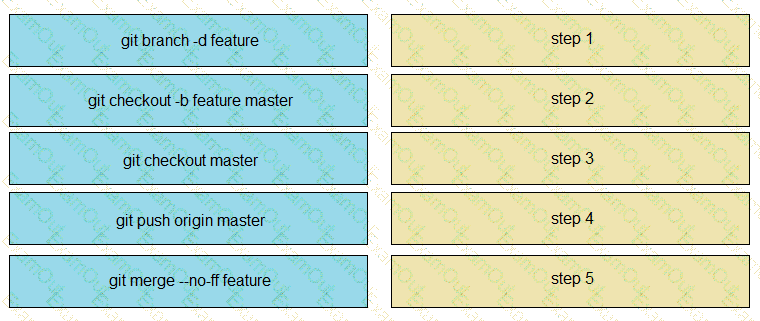
Drag and drop the git commands from the left into the correct order on the right to create a feature branch from the master and then incorporate that feature branch into the master.
A local data center deployment using Cisco NX-OS switches is scaling and requires automatic configuration at scale Configuration management must be set up for a Cisco NX-OS switch by using Ansible. The Ansible control server is currently located on a different subnet than the switch The solution has these requirements
• The transport protocol used must be encrypted
• The connections must originate from a server m the same local network
• Enable mode must be supported
Which connectivity method must be used?
Refer to the exhibit.
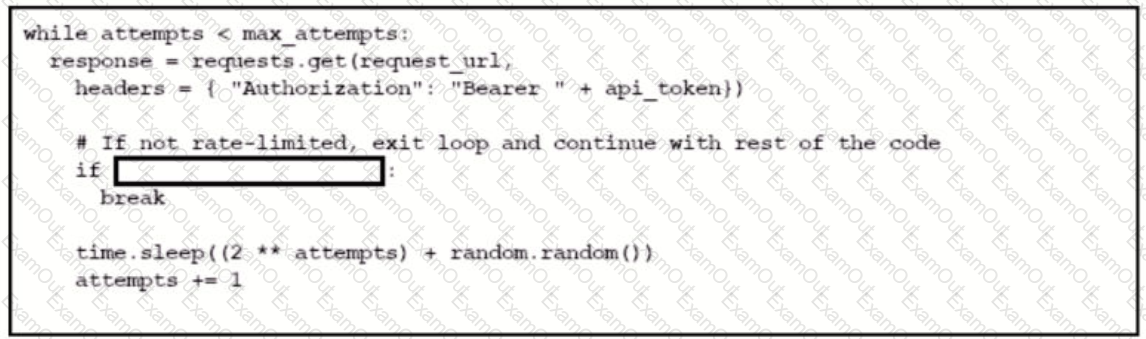
Which code snippet completes this code to handle API rate-limit?
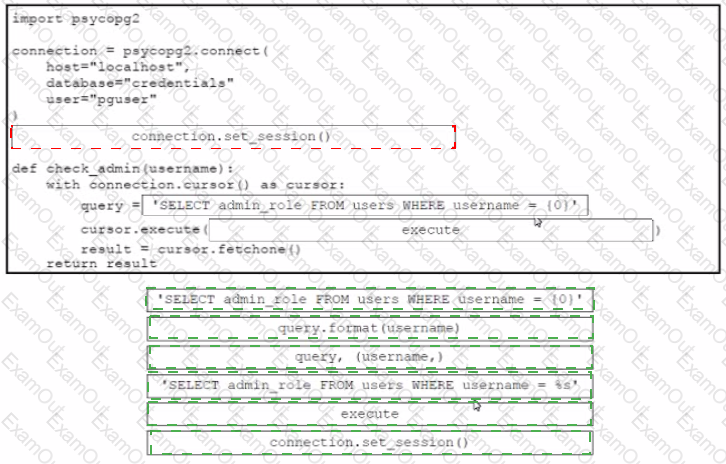
Drag and drop the code from the bottom onto the box where the code is missing in the Python code to query for user permissions while mitigating against SQL Injection Not all options are used.

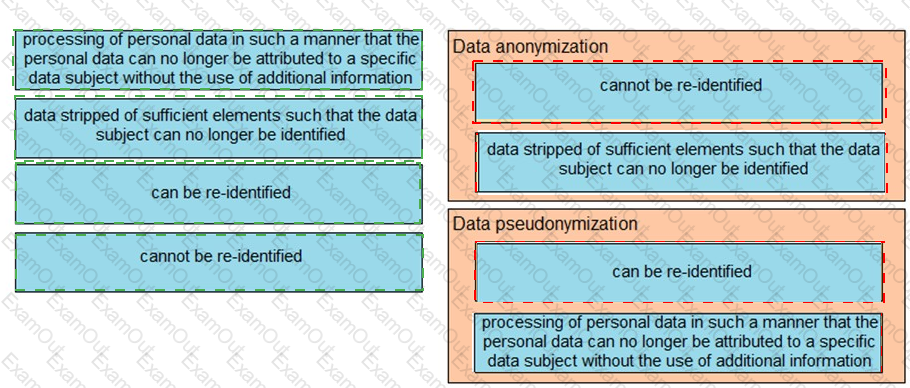
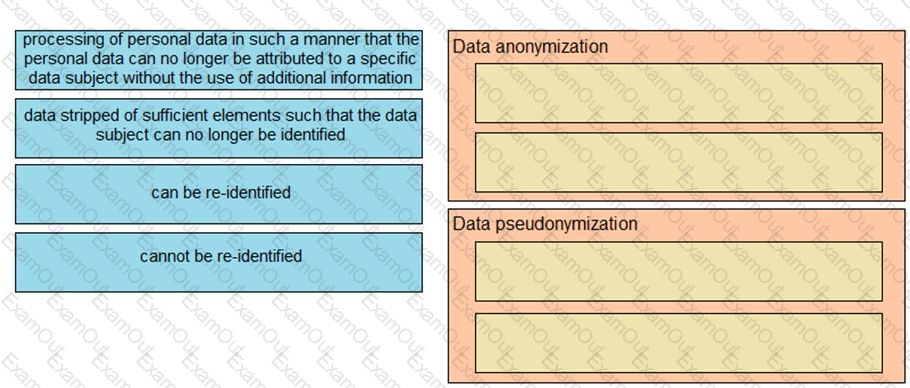
Drag and drop the characteristics from the left onto the correct data processing techniques on the right, in the context of GDPR.
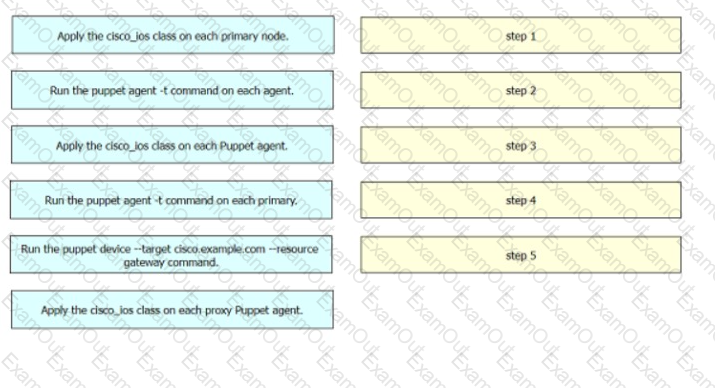
Drag and drop the steps from the left into the order on the right to create the workflow to retrieve the gateway information from a set of Cisco IOS devices. Not all options are used.
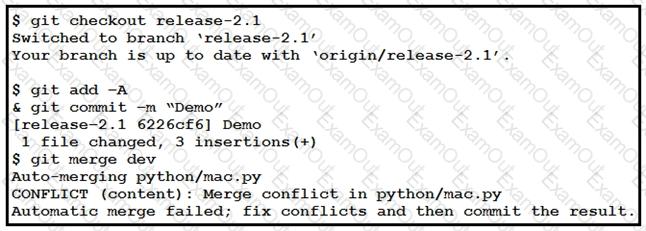
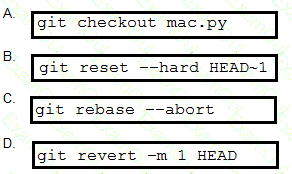
Refer to the exhibit. Which command resolves the merge conflict by removing the previous commit from the commit history?
When end-to-end encryption is implemented, which area is most vulnerable to exploitation?
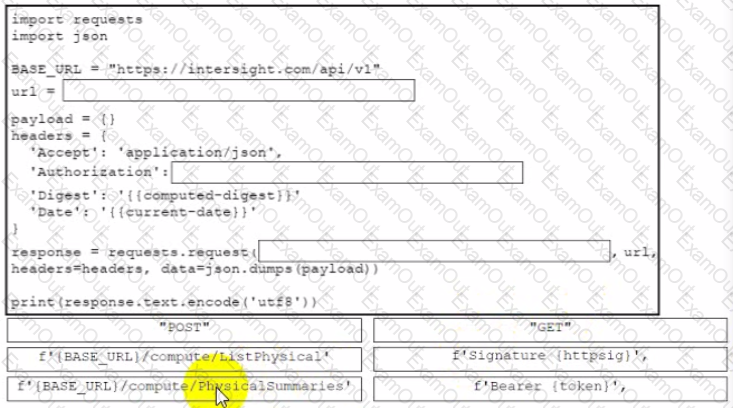
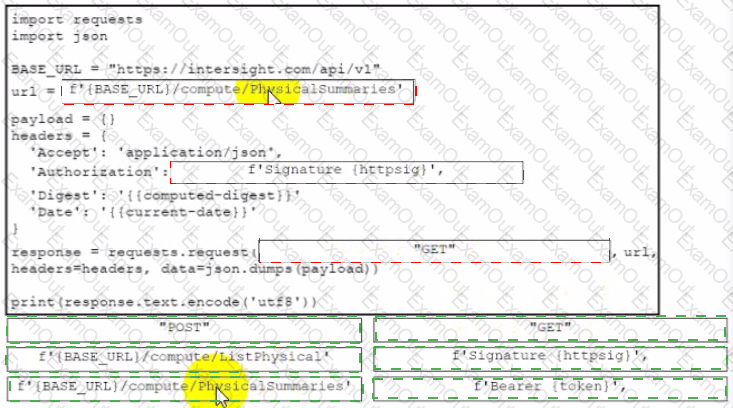
Drag and drop the code from the bottom onto the box where the code is missing to retrieve a summary of physical compute resources. The collected information about the compute resources will be presented in a dashboard to be developed for device monitoring purposes. Not all snippets are used.