What happens to voice packets from a Cisco 8845 IP phone in the QoS trust boundary?
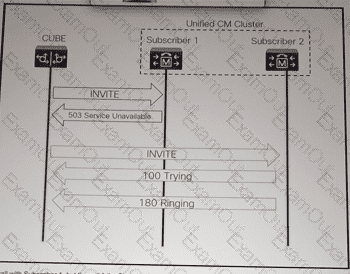
Refer to the exhibit. Cisco Unified element is attempting to establish a call with Subcribers1, but the call fails. Cisco Unified Border Element then retries the same call with Subcribers2, and the call proceeds normally.
Which action resolves the issue?
Which mark is used when the Attendant Console Client application and the Cisco TSP send their traffic?
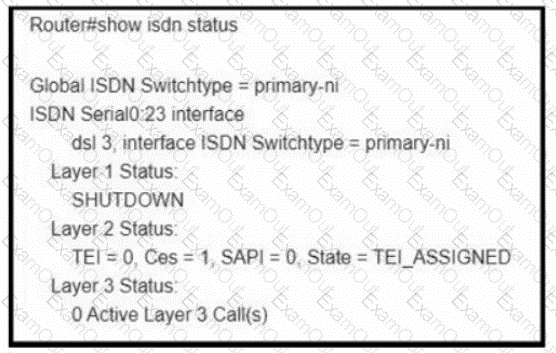
Refer to the exhibit. Users at a company located In New York cannot place calls. The New York gateway is configured with a T1 ISDN PRI card with 24 channels. The engineer runs the show isdn status command and receives output. Which action must the engineer take to resolve the issue?
What are two access management mechanisms in Cisco Webex Control Hub? (Choose two.)
To provide high-quality voice and take advantage of the full voice feature set, which two access layer switches provide support?
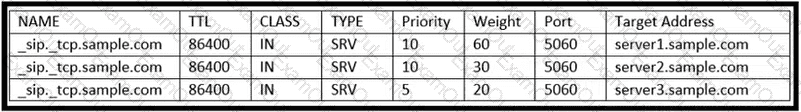
Refer to the exhibit. An administrator must fix the SRV records to ensure that server1. sample.com is always contacted first from the three servers. Which solution should the engineer apply to resolve this issue?
Which endpoint feature is supported using Mobile and Remote Access through Cisco Expressway?
Which command in the MGCP gateway configuration defines the secondary Cisco UCM server?
What are two features of Cisco Expressway that the customer gets if Expressway-C and Expressway-E are deployed?(Choose two.)

