An engineer needs to create a new user in the local user database on Cisco UCS Fabric Interconnect. The user needs permissions to change the following configuration inside UCS Manager version 3.1:
• vNIC and vHBA profiles
• Fan speed and power redundancy profile of UCS Manager
Which two roles must be assigned to a user to achieve this goal? (Choose two.)
A Cisco Unified Computing System environment must be configured for a server that requites access to VLAN 30 for data and VLAN 40 for management The server must have failover capabilities The upstream connectivity will be provided by using a Cisco Nexus 9000 Series Switch. Which action must be taken to meet these requirements?
A company must security harden its Cisco UCS C-Series servers. The security policy requires all out-of-band management to meet these requirements
It must encrypt all traffic
It must use nondefault ports
It must provide private administrative sessions
Which Cisco IMC corrflguraton meets the requirements?

Cisco Nexus 9000 Series Switches are configured with LACP protocol and default aging timers. What is the impact on the LACP peer during an ISSU upgrade?
Service degradation is reported on a VM that is deployed on a Cisco UCS blade server. The traffic from the vNIC is required to SPAN in both directions to a packet analyzer that is connected to UCS-A slot 2 port 12. Which two commands are needed to complete the configuration? (Choose two.)
Refer to the exhibit.
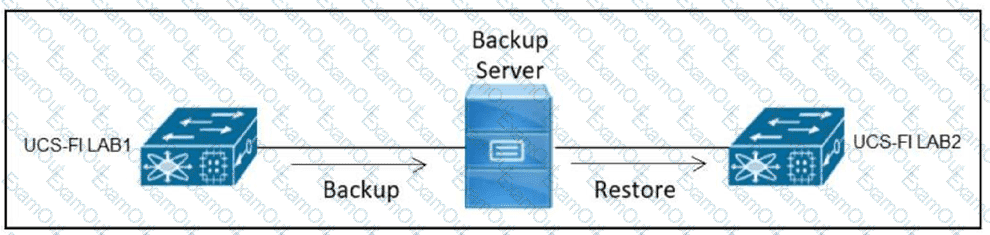
An engineer must replace the Fabric Interconnect called UCS-FI LAB1 with the Fabric Interconnect called UCS-Fl LAB2. The new Fabric Interconnect must be restored with the latest configuration of UCS-Fl LAB1. Which backup type must be used to meet this requirement?
A company provides applications and database hosting services to multiple customers using isolated infrastructure-as-a-service services within the same data center environment. The environment is based on Cisco MDS 9000 Series Switches. The requirement is to manage the environment by using Fibre Channel Security Protocol and to enable user authentication when the centralized AAA server is unreachable. All communication between the MDS switches and the remote servers must be encrypted. Which command set must be used to meet these requirements?
An engineer must integrate Cisco ACI with VMware vCenter The visualization team configured the necessary port groups and assigned them to virtual machines through VMware vCenter The final port group configuration must be protected from being changed by Cisco APIC Which action accomplishes these goals'?
An engineer must back up the Cisco UCS Manager configuration to a remote server. The backup job must meet these requirements:
The backup must use the TCP protocol and be secure.
Client identification does not need to be verified before data is transmitted
The backup must contain the system configuration, including usernames, roles, and locales.
The operations team requires that the backup file is in a human-readable format.
Which set of configurations should the engineer use?
An engineer must integrate Cisco ACI with a VMware vSphere environment The requirement is to use a VMware Distributed Virtual Switch and to assign the encapsulation VLAN of the EPG from the VLAN pool Which configuration set accomplishes this goa?

