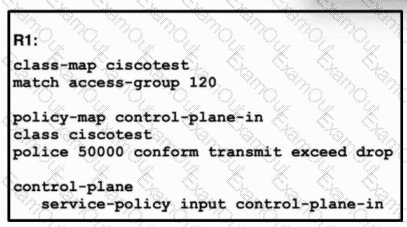
Refer to the exhibit. A network engineer installed router R1 as the new core router and must secure the control plane. The configuration has been applied, and now the engineer is creating ACL 120. Only hosts 192.168.1.1 and 192.168.2.2 should be allowed to access the router using Telnet. All other hosts should be rate-limited, with excess traffic dropped. Which configuration accomplishes this goal?
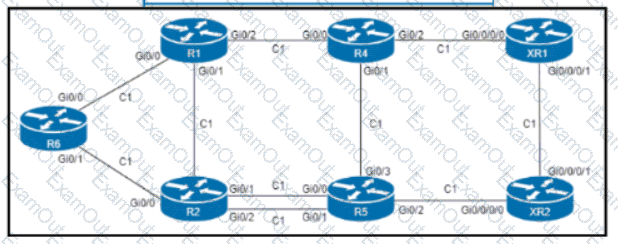
Refer to the exhibit. An engineer configured R6 as the headend LSR of an RSVP-TE LSP to router XR2, with the dynamic path signaled as R6-R2-R5-XR2. and set the OSPF cost of all links to 1. MPLS autotunnel backup Is enabled on all routers to protect the LSP. Which two NNHOP backup tunnels should the engineer use to complete the implementation? (Choose two.)
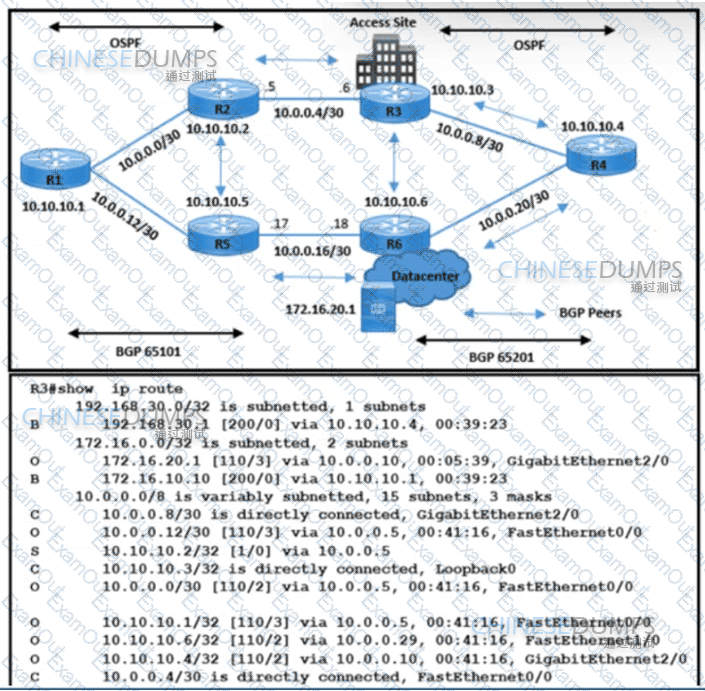
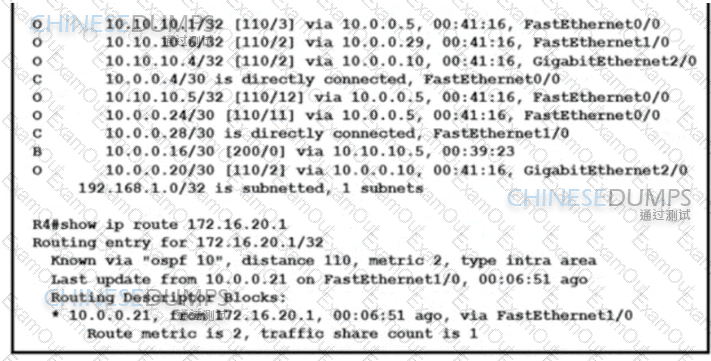
Refer to the exhibit. The network operations team reported that the access site that is connected to R3 is not connecting to the application server in the data center and that all packets that are sent from the application server to the access site are dropped. The team verified that OSPF and BGP peerings are up in BGP AS 65101 and BGP AS 65201. R4 is expected to receive traffic from the application server route via OSPF. Which action resolves this issue?
Refer to the exhibit:
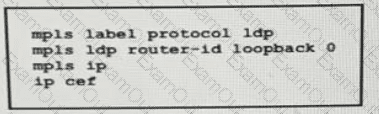
A network operator working for service provider with an employee id 3715 15:021 applied this configuration to a router.
Which additional step should the engineer use to enable LDP?

Refer to the exhibit. A multinational corporation with a Cisco-based network wants to leverage Cisco security features to enhance the security of their LAN and protect against eavesdropping and man-in-the-middle attacks. The solution must comply with the IEEE 802.1AE standard. A network engineer must implement the new security configurations on a pair of interconnected Cisco switches. The engineer already completed the configuration to enable AAA new-model and set up a basic AAA configuration for user authentication. Management VLAN 10 is in place for network administration. Which action must the engineer take to meet the requirements?
Which three OSPF parameters must match before two devices can establish an OSPF adjacency? (Choose three.)
What must a network engineer consider when designing a Cisco MPLS TE solution with OSPF?
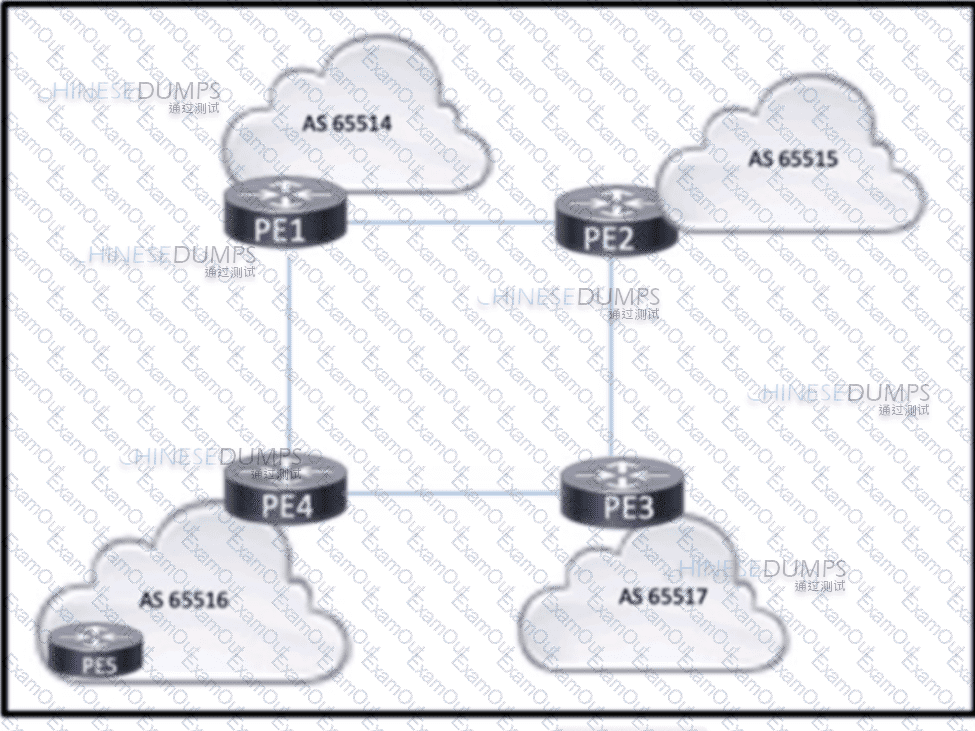
Refer to the exhibit. Four midsize service providers provide access to different customers that use Layer 3 VPN services to enable communication across geographic regions. The service providers are connected as shown in the exhibit, and the PEs have established eBGP relationships. PE4 has an IBGP relationship with PE5. The routes that PE4 learns from PE5 must reach the other PE routers, but they are absent from the routing tables on the other PES. Which action should the engineers take to correct the problem?
Which characteristic describes prefix segment identifier?

Refer to the exhibit. A network engineer must configure XR-PE1 for uninterruptible failover from active RP to the standby RP Neither peer devices CGW1 nor the network of ASN 64512 support restart extensions Which configuration must the engineer apply to XR PEI to complete tasks?
A)

B)
C)

D)

A customer of an ISP requests support to setup a BGP routing policy. Which BGP attribute should be configured to choose specific BGP speakers as preferred exit
points for the customer AS?
Refer to the exhibit.

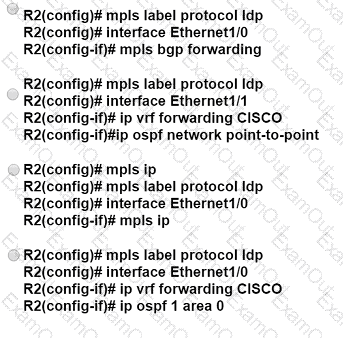
An engineer is configuring two routers to support MPLS LDP sessions between them. The R1 configuration is complete, and work has started on R2 as shown. Which additional configuration must the engineer apply to R2 to complete the task?
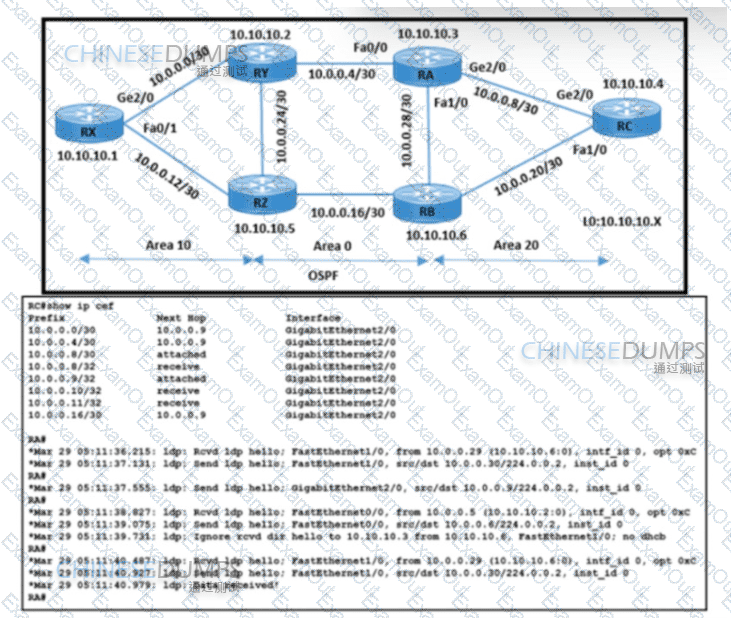
Refer to the exhibit. The operations team is implementing an LDP-based configuration in the service-provider core network with these requirements:
RC must establish LDP peering with the loopback IP address as its Router ID
RA must establish LDP peering with RB. RC, and RY.
How must the team update the network configuration to successfully enable LDP peering between RA and RC?
Refer to the exhibit.
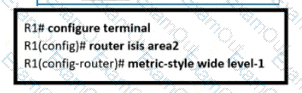
An engineer is configuring multitopology IS-IS for IPv6 on router R1. Which additional configuration must be applied to the router to complete the task?
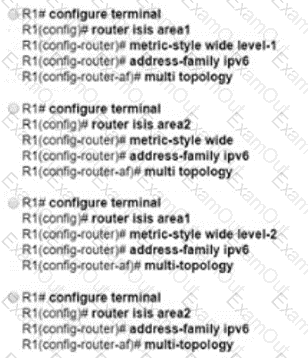
Refer to the exhibit. A large enterprise is migrating its network to use MPLS VPNs between different business divisions. Within the core, routes are shared between the routers using OSPF, and each connected link maintains an MPLS neighbor relationship.
Which action must the migration team take so that LDP neighbor relationships are maintained if a directly-connected link goes down?

