An engineer is configuring multifactor authentication using Duo. The implementation must use Duo Authentication Proxy and the Active Directory as an identity source. The company uses Azure and a local Active Directory. Which configuration is needed to meet the requirement?
How does Cisco XDR perform threat prioritization by using its visibility across multiple platforms?
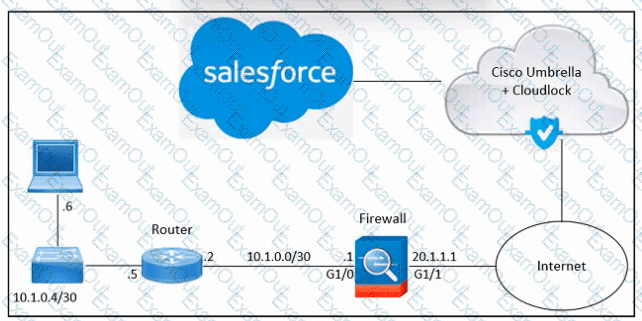
Refer to the exhibit. An engineer must enable access to Salesforce using Cisco Umbrella and Cisco Cloudlock. These actions were performed:
From Salesforce, add the Cloudlock IP address to the allow list
From Cloudlock, authorize Salesforce
However, Salesforce access via Cloudlock is still unauthorized. What should be done to meet the requirements?
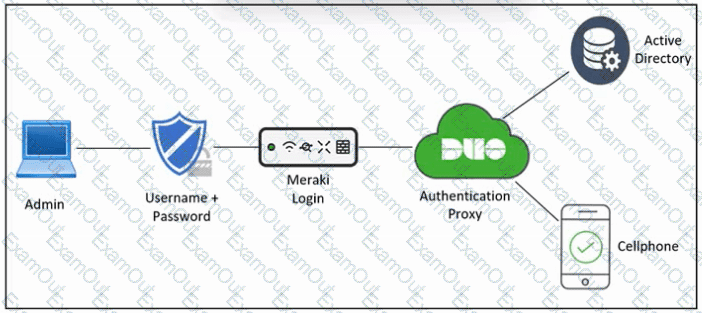
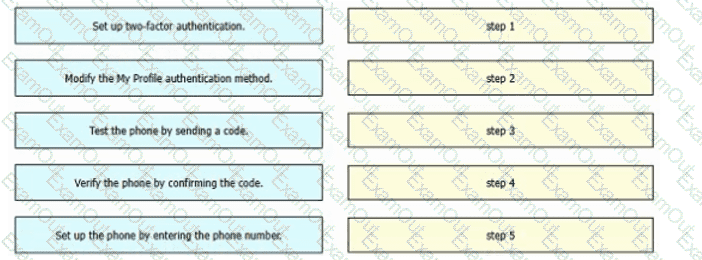
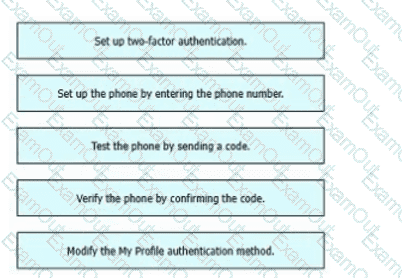
Refer to the exhibit. An engineer must configure multifactor authentication using the Duo Mobile app to provide admin access to a Cisco Meraki switch. The engineer already configured Duo Mobile and received an activation code. Drag and drop the steps from left to right to complete the configuration.
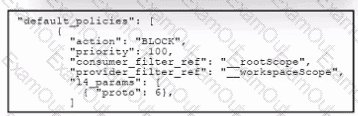
Refer to the exhibit. An engineer configured a default segmentation policy in Cisco Secure Workload to block SMTP traffic. During testing, it is observed that the SMTP traffic is still allowed. Which action must the engineer take to complete the configuration?
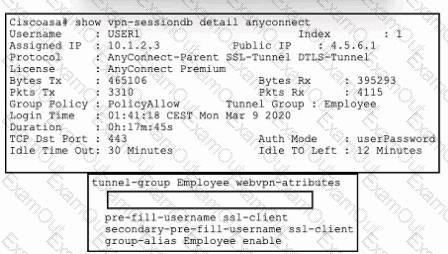
Refer to the exhibit. An engineer must implement a remote access VPN solution that provides user and device verification. The company uses Active Directory for user authentication and ID certificates for device identity. Users are currently able to connect using only a valid username and password, even if their computer is missing the required certificate.
Which command from the Cisco ASA tunnel-group completes the requirement of verifying device identity in addition to user identity?
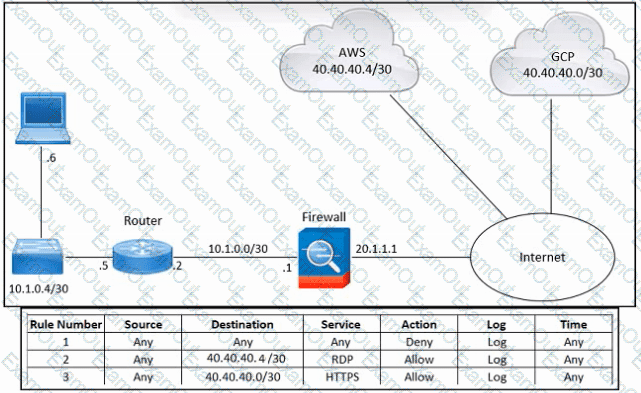
Refer to the exhibit. An engineer must provide RDP access to the AWS virtual machines and HTTPS access to the Google Cloud Platform virtual machines. All other connectivity must be blocked. The indicated rules were applied to the firewall; however, none of the virtual machines in AWS and Google Cloud Platform are accessible. What should be done to meet the requirement?
What does the Cisco Telemetry Broker provide for telemetry data?
In the zero-trust network access model, which criteria is used for continuous verification to modify trust levels?
Which SAFE component logically arranges the security capabilities into blueprints?

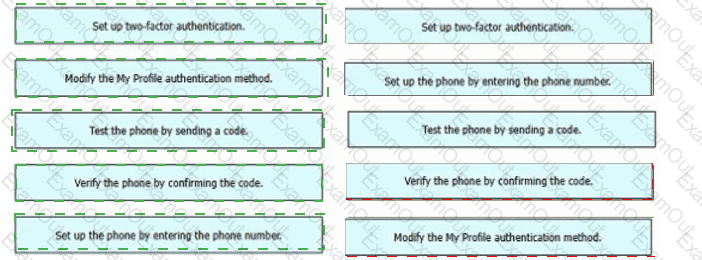
 A screenshot of a phone number
AI-generated content may be incorrect.
A screenshot of a phone number
AI-generated content may be incorrect.