An administrator wants to restrict file uploads to Facebook using the AVC feature.
Under which two actions must the administrator apply this restriction to an access policy? (Choose two.)
Which method is used by AMP against zero-day and targeted file-based attacks?
A network administrator noticed that all traffic that is redirected to the Cisco WSA from the Cisco ASA firewall cannot get to the Internet in a Transparent proxy environment using WCCP.
Which troubleshooting action must be taken on the CLI to make sure that WCCP communication is not failing?
What is a benefit of integrating Cisco WSA with TrustSec in ISE?
By default, which two pieces of information does the Cisco WSA access log contain? (Choose two.)
Which statement about the SOCKS proxy is true?
Which two features on the Cisco WSA help prevent outbound data loss for HTTP or FTP traffic? (Choose two.)
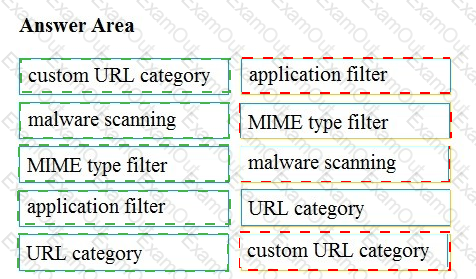
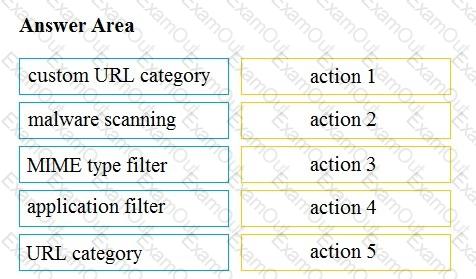
Drag and drop the Cisco WSA access policy elements from the left into the order in which they are processed on the right.
Which configuration mode does the Cisco WSA use to create an Active Directory realm for Kerberos authentication?
Refer to the exhibit.

Which statement about the transaction log is true?