Which type of attack is prevented by configuring file reputation filtering and file analysis features?
Which two action types are performed by Cisco ESA message filters? (Choose two.)
The company security policy requires that the finance department have an easy way to apply encryption to their outbound messages that contain sensitive data Users must be able to flag the messages that require encryption versus a Cisco Secure Email Gateway appliance scanning all messages and automatically encrypting via detection Which action enables this capability?
What are the two different phases in the process of Cisco Secure Email Gateway performing S/MIME encryption? (Choose two.)
An organization wants to use its existing Cisco ESA to host a new domain and enforce a separate corporate policy for that domain.
What should be done on the Cisco ESA to achieve this?
The CEO added a sender to a safelist but does not receive an important message expected from the trusted sender. An engineer evaluates message tracking on the Cisco Secure Email Gateway appliance and determines that the message was dropped by the antivirus engine. What is the reason for this behavior?
An organization wants to prevent proprietary patent documents from being shared externally via email. The network administrator reviewed the DLP policies on the Cisco Secure Email Gateway and could not find an existing policy with the appropriate matching patterns. Which type of DLP policy template must be used to create a policy that meets this requirement?
Refer to the exhibit.
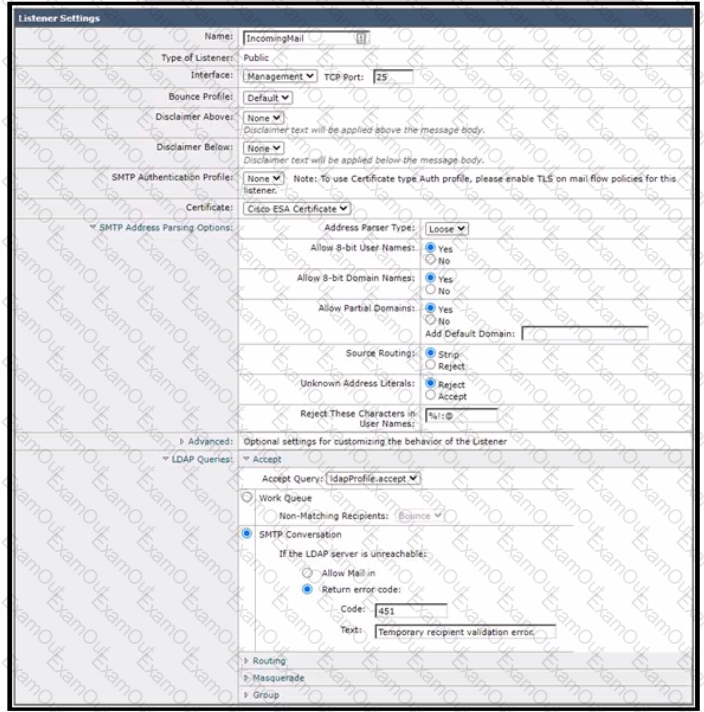
Which additional configuration action must be taken to protect against Directory Harvest Attacks?
A company has deployed a new mandate that requires all emails sent externally from the Sales Department to be scanned by DLP for PCI-DSS compliance. A new DLP policy has been created on the Cisco ESA and needs to be assigned to a mail policy named ‘Sales’ that has yet to be created.
Which mail policy should be created to accomplish this task?
Email encryption is configured on a Cisco ESA that uses CRES.
Which action is taken on a message when CRES is unavailable?

