An engineer is designing a new distributed deployment for Cisco ISE in the network and is considering failover options for the admin nodes. There is a need to ensure that an admin node is available for configuration of policies at all times. What is the requirement to enable this feature?
An engineer is migrating users from MAB to 802.1X on the network. This must be done during normal business hours with minimal impact to users. Which CoA method should be used?
An administrator must deploy the Cisco Secure Client posture agent to employee endpoints that access a wireless network by using URL redirection in Cisco ISE. The compliance module must be downloaded from Cisco and uploaded to the Cisco ISE client provisioning resource. What must be used to upload the compliance module?
There is a need within an organization for a new policy to be created in Cisco ISE. It must validate that a specific anti-virus application is not only installed, but running on a machine before it is allowed access to the network. Which posture condition should the administrator configure in order for this policy to work?
Wireless network users authenticate to Cisco ISE using 802.1X through a Cisco Catalyst switch. An engineer must create an updated configuration to assign a security group tag to the user's traffic using inline tagging to prevent unauthenticated users from accessing a restricted server. The configurations were performed:
• configured Cisco ISE as a Cisco TrustSec AAA server
• configured the switch as a RADIUS device in Cisco ISE
• configured the wireless LAN controller as a TrustSec device in Cisco ISE
• created a security group tog for the wireless users
• created a certificate authentication profile
■ created an identity source sequence
• assigned an appropriate security group tag to the wireless users
• defined security group access control lists to specify an egress policy
• enforced the access control lists on the TrustSec policy matrix in Cisco ISE
• configured TrustSec on the switch
• configured TrustSec on the wireless LAN controller
Which two actions must be taken to complete the configuration? (Choose two.)
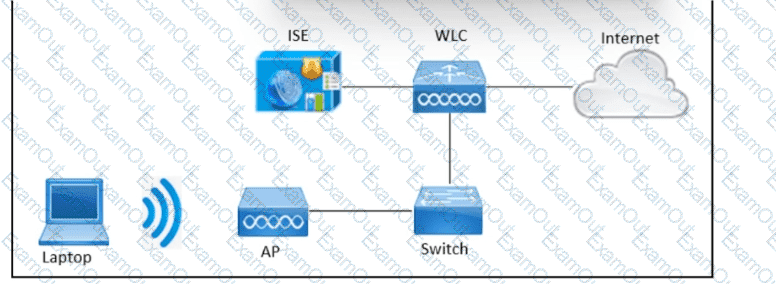
Refer to the exhibit. An engineer needs to configure central web authentication on the Cisco Wireless LAN Controller to use Cisco ISE for all guests connected to the wireless network. The components are configured already:
• Cisco Wireless LAN Controller is fully configured
• authorization profile on the Cisco ISE
• authentication policy on the Cisco ISE
Which component would be configured next on Cisco ISE?
What are two differences between the RADIUS and TACACS+ protocols'? (Choose two.)
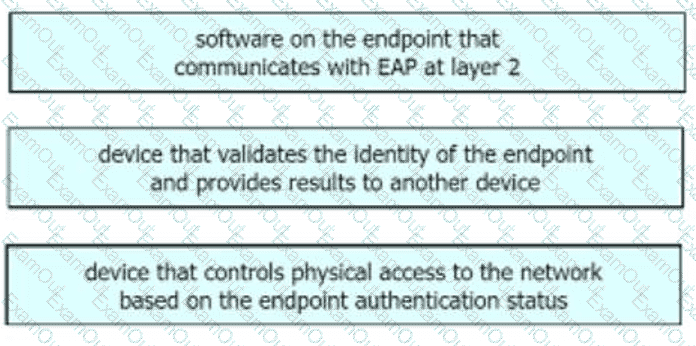
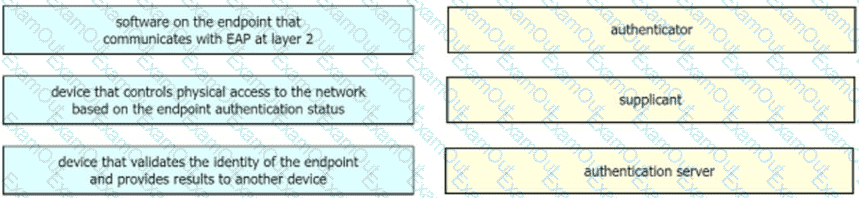
Drag the descriptions on the left onto the components of 802.1X on the right.
Which advanced option within a WLAN must be enabled to trigger Central Web Authentication for Wireless users on AireOS controller?
An engineer is configuring TACACS+ within Cisco ISE for use with a non-Cisco network device. They need to send special attributes in the Access-Accept response to ensure that the users are given the appropriate access. What must be configured to accomplish this'?