Refer to the exhibit.
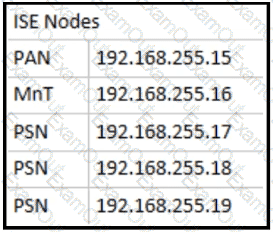
Which two configurations are needed on a catalyst switch for it to be added as a network access device in a Cisco ISE that is being used for 802 1X authentications? (Choose two )
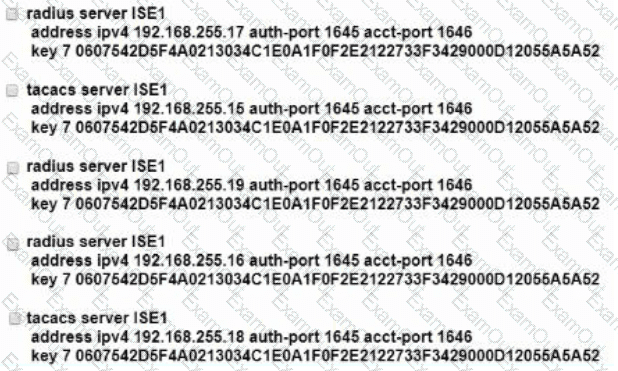
A network administrator is configuring a new access switch to use with Cisco ISE for network access control. There is a need to use a centralized server for the reauthentication timers. What must be configured in order to accomplish this task?
There are several devices on a network that are considered critical and need to be placed into the ISE database and a policy used for them. The organization does not want to use profiling. What must be done to accomplish this goal?
An engineer deploys Cisco ISE and must configure Active Directory to then use information from Active Directory in an authorization policy. Which two components must be configured, in addition to Active Directory groups, to achieve this goat? (Choose two )
What must be configured on the Cisco ISE authentication policy for unknown MAC addresses/identities for successful authentication?
Which two task types are included in the Cisco ISE common tasks support for TACACS+ profiles?
(Choose two.)
An engineer is configuring ISE for network device administration and has devices that support both protocols. What are two benefits of choosing TACACS+ over RADUs for these devices? (Choose two.)
A network engineer must configure a policy rule to check the endpoint. The policy must ensure disk encryption is enabled and the appropriate antivirus software version is installed. Which configuration must the engineer apply to the rule?
An administrator is editing a csv list of endpoints and wants to reprofile some of the devices indefinitely before importing the list into Cisco ISE. Which field and Boolean value must be changed for the devices before the list is reimported?
An administrator is configuring RADIUS on a Cisco switch with a key set to Cisc403012128 but is receiving the error “Authentication failed: 22040 Wrong password or invalid shared secret. “what must be done to address this issue?

