Which type of cyberattack does Cisco Umbrella DNS-layer security effectively help mitigate?
Which command must be run on a Cisco IOS device to configure six parallel iBGP and eBGP routes that can be installed into a routing table?
An engineer must design a pay-as-you-go solution for their partners. The solution must allow for rapid deployments, be flexible, and scale resources up or down in a hybrid workplace. What must be used?
An engineer must enable the highest level of logging when troubleshooting Cisco NFVIS. Which command must be run?
What is a valid connection method between carrier-neutral facilities within the same metro area?
What is a capability of a Cisco NFVIS SNMP trap?
How does SR-IOV move data directly to and from the network adapter?
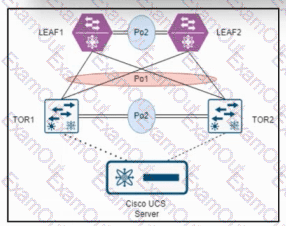
Refer to the exhibit. An engineer must connect switch TOR1 and switch TOR2 to switch LEAF1 and switch LEAF2 by using double-sided vPCs. LEAF1 and LEAF2 are already configured as vPC peers. Which action must be taken next to complete the configuration?
An engineer must configure NTP servers in Cisco Enterprise NFVIS. The primary NTP server has an IP address of 192.168.1.1 and the backup NTP server has an IP address of 192.168.2.1. Which two commands must be run to complete the configuration? (Choose two.)
What is a valid connection method between carrier-neutral facilities within the same metro area?

