A network architect is troubleshooting the L2TPv3 tunneling security due to the untrusted nature of the underlaying network. Which two L2TPv3 features does the architect deploy to address the ongoing issues? (Choose two.)
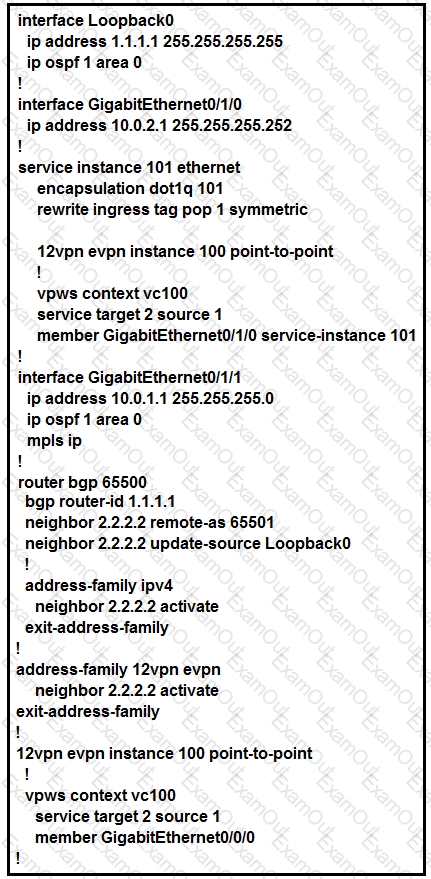
An engineer is trying to configure an EVPN VWPS. What is the issue with this configuration?
How does Layer 3 VPN traffic traverse an ISP network?
What is a requirement to share VRF reachability information to all members of a VPN when using IPv6?
The network engineering group of a large ISP needs to harden the management plane of its Cisco 9000
Series ASRs. While addressing IPv6 ICMP issues, they realized they have to limit the rate at which IPv6 ICMP error messages are sent out on the network. Which command do they need to apply?
Refer to the exhibit.

An organization is running H-VPLS on a network comprising four routers in a hub-and-spoke topology with R1 as the hub An engineer added a new spoke with multiple VCs to the network, and now traffic cannot flow properly How should the engineer update the configuration on R1 to correct the problem?
Refer to the exhibit.
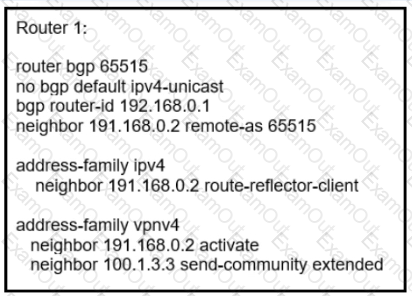
Router 1 is a route reflector client within a service provider core PE1 cannot see VPNv4 routes received from the ASBR PE1 only has an iBGP relationship with Router 1. Which action resolves this issue?
Refer to the exhibit.
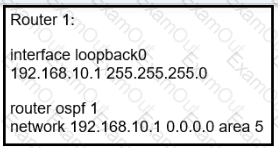
Refer to the exhibit Router 1 is a P router in the ISP MPLS core A connected P router cannot generate an MPLS label for the router 1 loopback0 interface Which action resolves this issue?
Refer to the exhibit.
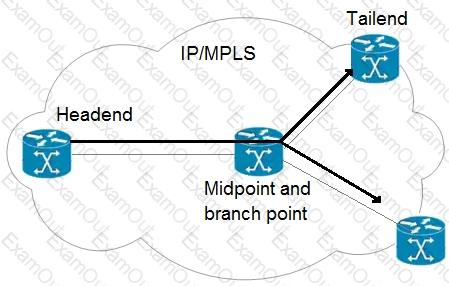
An engineer is implementing an MPLS P2MP TE solution. Which type of router can serve as the midpoint router and the tailend router in this P2MP TE network implementation?
An ISP provides a major client MPLS VPN for managed services. The MPLS engineering team needs to use the advanced VPN feature of selective VRF import so that only specific prefixes are present in the required VPNs.
Which aspect of this feature must the team consider?

