A customer wants to allow employees to easily onboard their personal devices to the wireless network. The visitors also must be able to connect to the same network without the need to engage with anyone from the reception desk. Which process must be configured on Cisco ISE to support this requirement?
A FlexConnect remote office deployment is using five 2702i APs indoors and two 1532i APs outdoors. When a code upgrade is performed and FlexConnect Smart AP Image Upgrade is leveraged, but no FlexConnect Master AP has been configured, how many image transfers between the WLC and APs will occur?
An engineer must track guest traffic flow using the WLAN infrastructure. Which Cisco CMX feature must be configured and used to accomplish this tracking?
An IT department receives a report of a stolen laptop and has information on the MAC address of the laptop. Which two settings must be set on the wireless infrastructure to determine its location? (Choose two.)
WPA2 Enterprise with 802.1X is being used for clients to authenticate to a wireless network through a Cisco ISE server. For security reasons, the network engineer wants to ensure that only PEAP authentication is used. The engineer sent instructions to clients on how to configure the supplicants, but the ISE logs still show users authenticating using EAP-FAST. Which action ensures that access to the network is restricted for these users unless the correct authentication mechanism is configured?
An engineer is configuring multicast for wireless for an all-company video meeting on a network using EIGRP and BGP within a single domain from a single source. Which type of multicast routing should be implemented?
Refer to the exhibit.
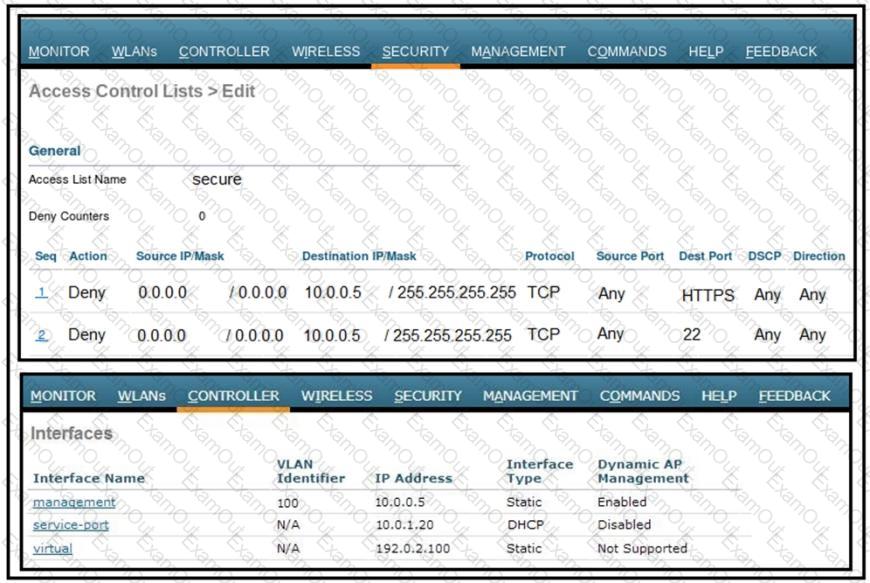
An engineer implemented the CPU ACL on your Cisco 5520 Series Wireless LAN Controller, and the controller is no longer manageable via the network. What must be changes on this CPU ACL to enable it to manage the controller again?
Refer to the exhibit.
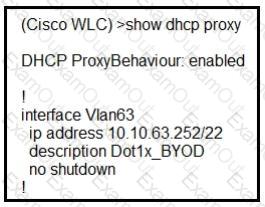
A network administrator deploys the DHCP profiler service in two ISE servers: 10.3.10.101 and 10.3.10.102. All BYOD devices connecting to WLAN on VLAN63 have been incorrectly profiled and are assigned as unknown profiled endpoints. Which action efficiently rectifies the issue according to Cisco recommendations?
Which devices can be tracked with the Cisco Context Aware Services?
A corporation is spread across different countries and uses MPLS to connect the offices. The senior management wants to utilize the wireless network for all the employees. To ensure strong connectivity and minimize delays, an engineer needs to control the amount of traffic that is traversing between the APs and the central WLC. Which configuration should be used to accomplish this goal?

