Exhibit.
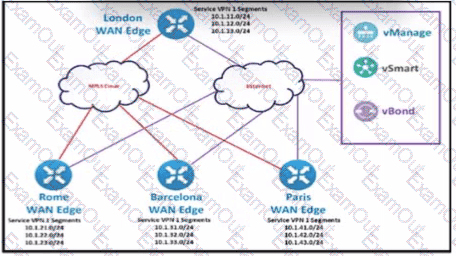
The SD-WAN network is configured with a default full-mash topology. An engineer wants Barcelona and Paris to communicate to each other through the London site using a control Which control policy configuration accomplishes the task?
A)

B)

C)
D)
An engineer must configure a centralized policy on a site in which all HTTP traffic should use the Public Internet circuit if the loss on this circuit is below 10%. otherwise MPLS should be used Which configuration wizard fulfils this requirement?
Which configuration changes the packet loss priority from low to highly?
A)
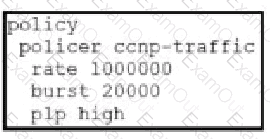
B)

C)
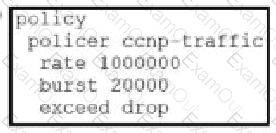
D)
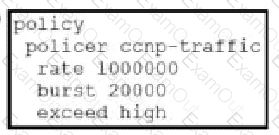
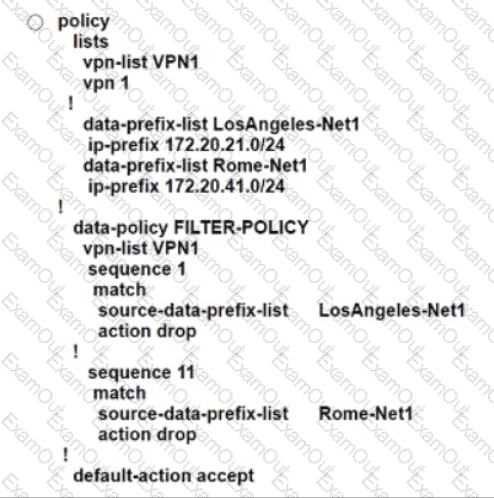
An engineer creates a data policy to prevent communication from the 172.20.21.0/24 network to the 172.20.41.0/24 network. Which configuration accomplishes this task?
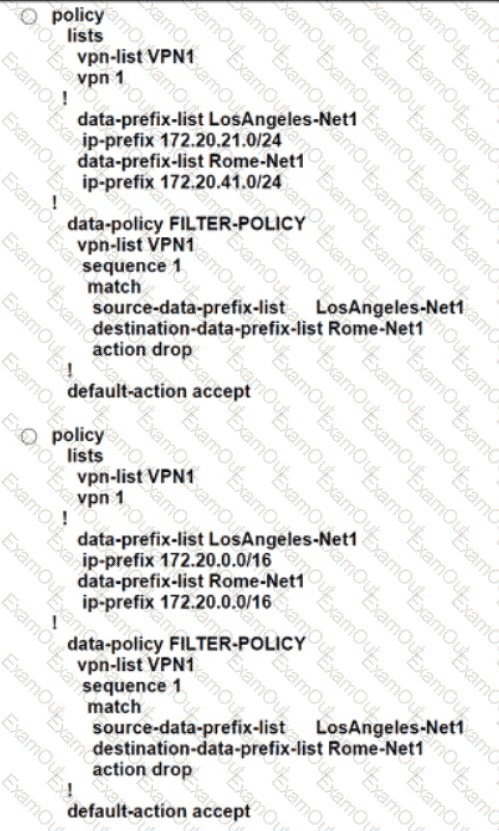
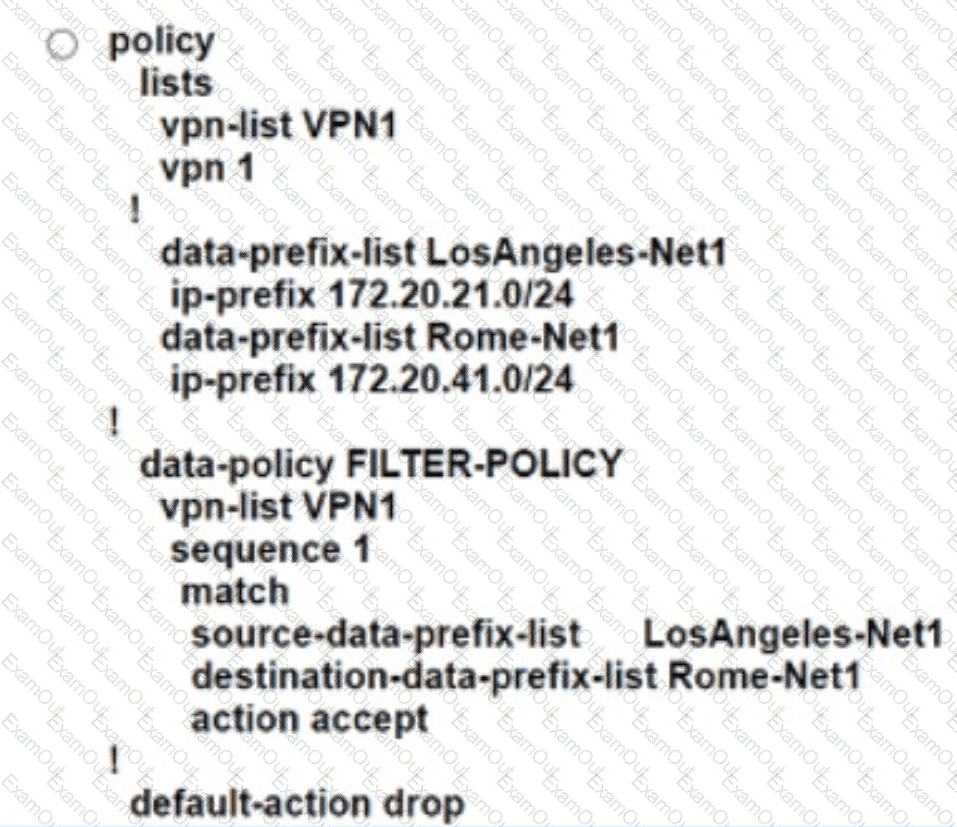
An engineer must configure local redundancy on a site. Which configuration accomplish this task?
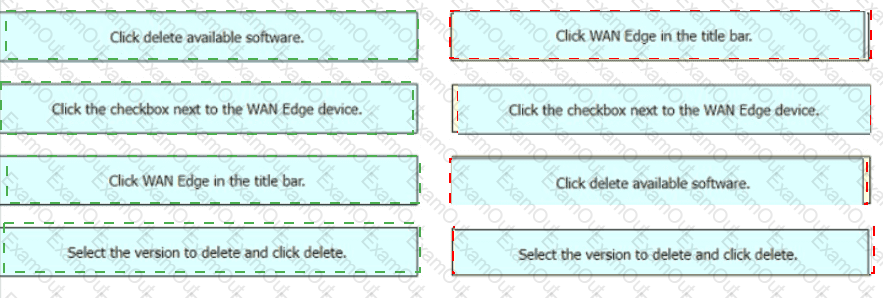
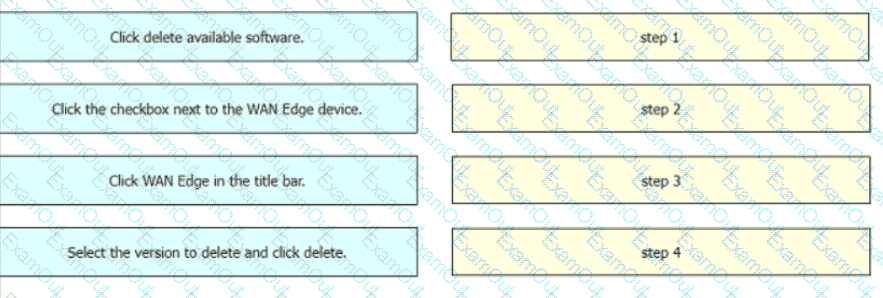
Drag and drop the steps from the left Into the order on the right to delete a software image for a WAN Edge router starting with Maintenance > Software Upgrade > Device list on vManage.
In Cisco SD-WAN, what protocol is used for control connections between SD-WAN devices?
Which type of lists are used to group related items via an application-aware routing policy under the policy lists command hierarchy on vSmart controllers?
Which storage format Is used when vManage Is deployed as a virtual machine on a KVM hypervisor?
What problem happens on a device with two serial numbers, a unique device identifier (UDI), and secure unique device identifier (SUDI) when an engineer provisions ISR 4000 by PnP using only a UDI?