What is an advantage of using BFD?
Which command displays the IP routing table information that is associated with VRF-Lite?
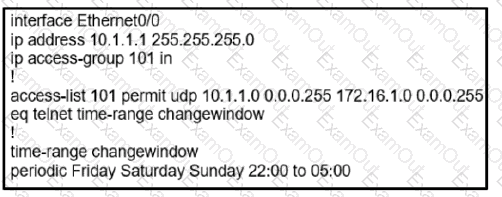
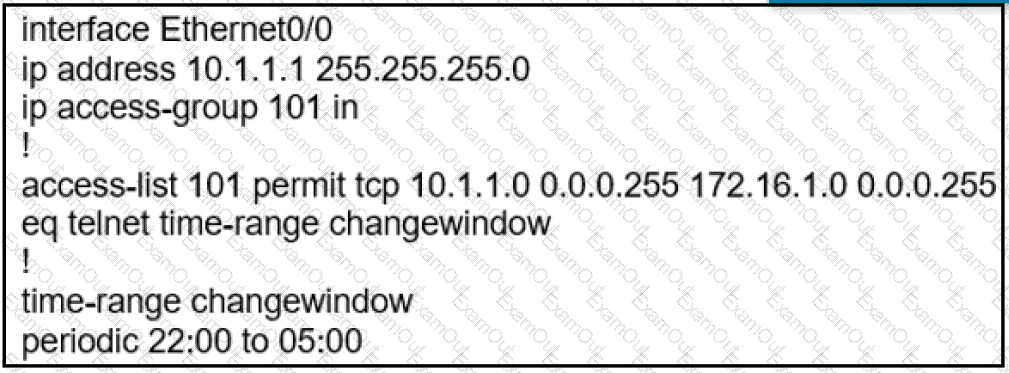
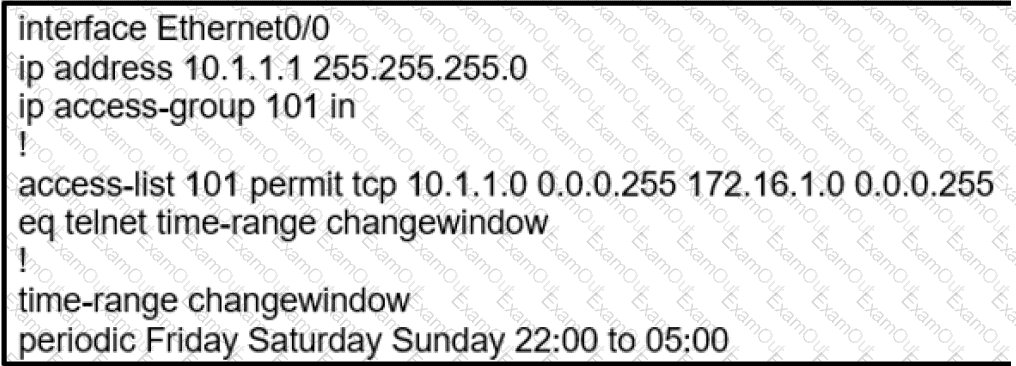
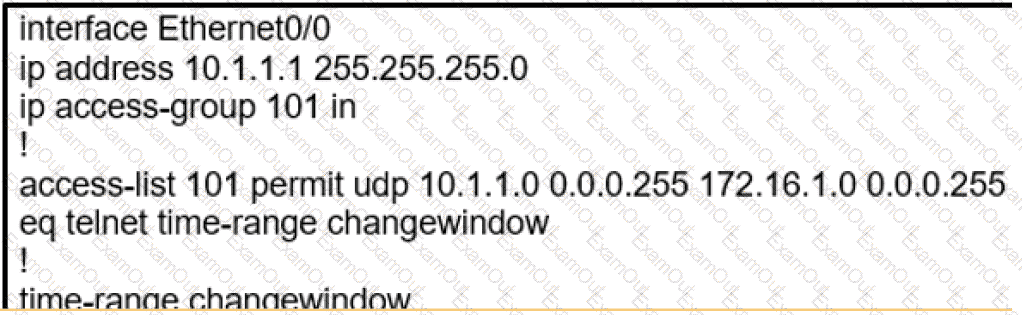
During the maintenance window an administrator accidentally deleted the Telnet-related
configuration that permits a Telnet connection from the inside network (Eth0/0) to the outside of the networking between Friday – Sunday night hours only. Which configuration resolves the issue?
A)
B)
C)
D)
Which statement about MPLS LDP router ID is true?
Refer to the exhibit.
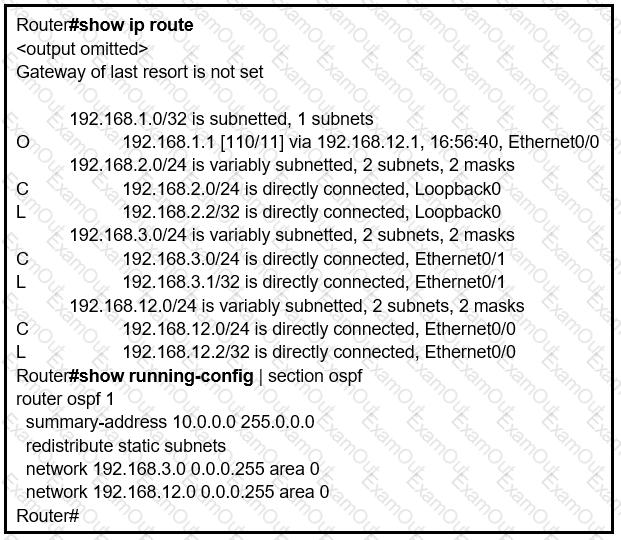
An engineer is trying to generate a summary route in OSPF for network 10.0.0.0/8, but the
summary route does not show up in the routing table. Why is the summary route missing?
What is a prerequisite for configuring BFD?
Which option is the best for protecting CPU utilization on a device?
Which command is used to check IP SLA when an interface is suspected to receive lots of traffic with options?
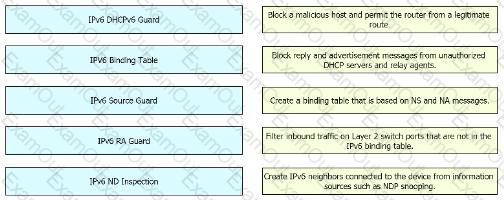
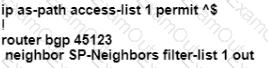
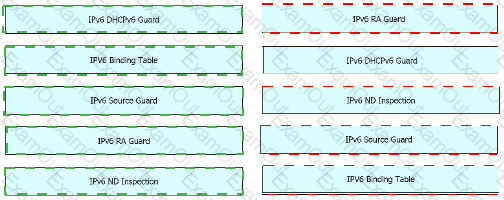
Drag and Drop the IPv6 First-Hop Security features from the left onto the definitions on the right.
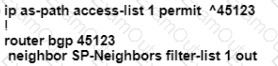
After some changes in the routing policy, it is noticed that the router in AS 45123 is being used as a transit AS router for several service provides. Which configuration ensures that the branch router in AS 45123 advertises only the local networks to all SP neighbors?
A)
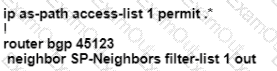
B)
C)
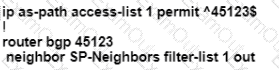
D)
Which label operations are performed by a label edge router?
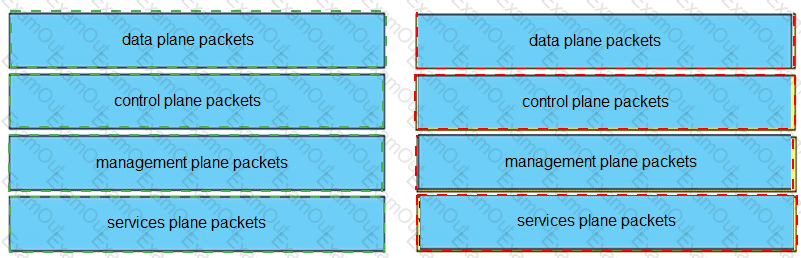
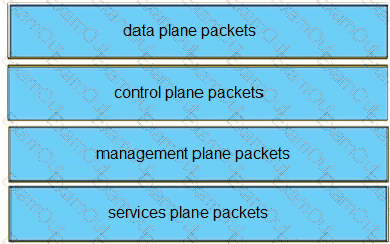
Drag and drop the packet types from the left onto the correct descriptions on the right.
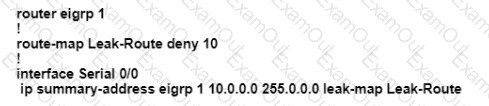
An engineer configured a leak-map command to summarize EIGRP routes and advertise specifically loopback 0 with an IP of 10.1.1.1.255.255.255.252 along with the summary route. After finishing configuration, the customer complained not receiving summary route with specific loopback address. Which two configurations will fix it? (Choose two.)
What is a limitation of IPv6 RA Guard?
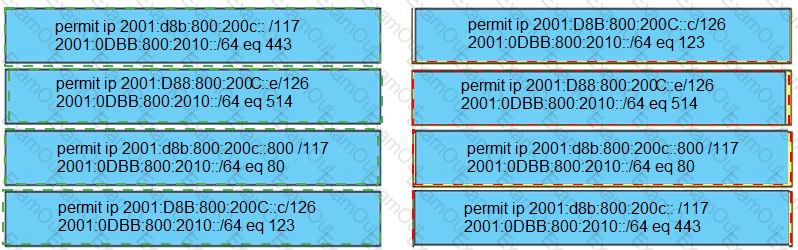
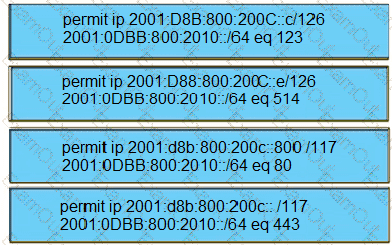
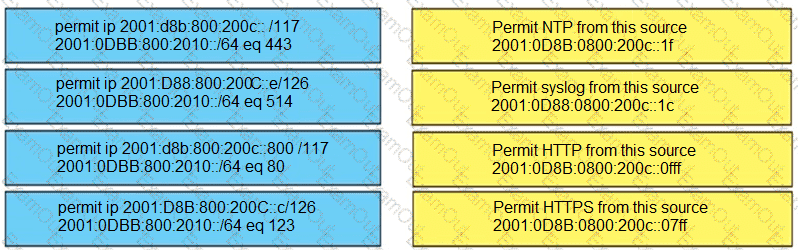
Drag and drop the addresses from the left onto the correct IPv6 filter purposes on the right.

 Graphical user interface, chart Description automatically generated
Graphical user interface, chart Description automatically generated