Which attack is the network vulnerable to when a stream cipher like RC4 is used twice with the same key?
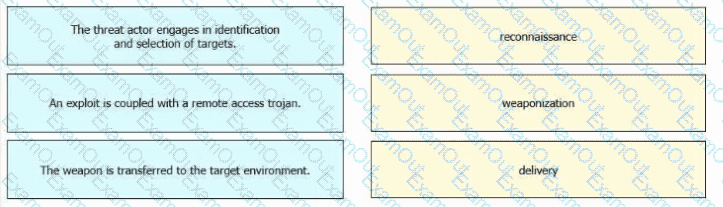
Drag and drop the definitions from the left onto the phases on the right to classify intrusion events according to the Cyber Kill Chain model.
Which attack is the network vulnerable to when a stream cipher like RC4 is used twice with the same key?
Drag and drop the definitions from the left onto the phases on the right to classify intrusion events according to the Cyber Kill Chain model.
