You need a software solution that performs the following tasks:
Compiles network data
Logs information from many sources
Provides orchestration in the form of case management
Automates incident response workflows
What product should you use?
Your supervisor suspects that someone is attempting to gain access to a Windows computer by guessing user account IDs and passwords. The supervisor asks you to use the Windows Event Viewer security logs to verify the attempts.
Which two audit policy events provide information to determine whether someone is using invalid credentials to attempt to log in to the computer?(Choose 2.)
Note: You will receive partial credit for each correct selection.
Which macOS security feature encrypts the entire macOS volume?
How do threat actors launch ransomware attacks on organizations?
You work for a hospital that stores electronic protected health information (ePHI) in an online portal. Authorized employees can use their mobile devices to access patient ePHI.
You need to ensure that employees’ mobile devices comply with HIPAA regulations.
Which safeguard should you develop and implement?
Which security assessment of IT systems verifies that PII data is available, accurate, confidential, and accessible only by authorized users?
Move each worm mitigation step from the list on the left to the correct description on the right.
Note: You will receive partial credit for each correct answer.

Your manager asks you to review the output of some vulnerability scans and report anything that may require escalation.
Which two findings should you report for further investigation as potential security vulnerabilities?(Choose 2.)
For each statement, selectTrueif it is a common motivation to commit cyber attacks orFalseif it is not.
Note: You will receive partial credit for each correct selection.

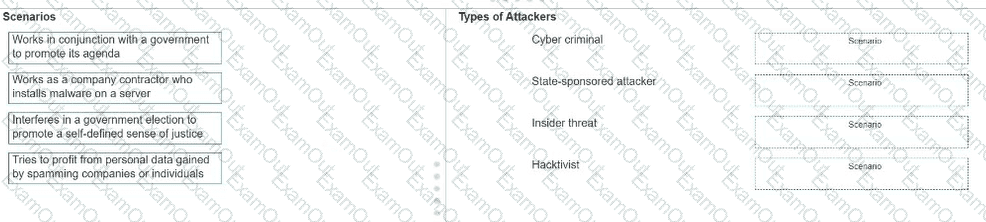
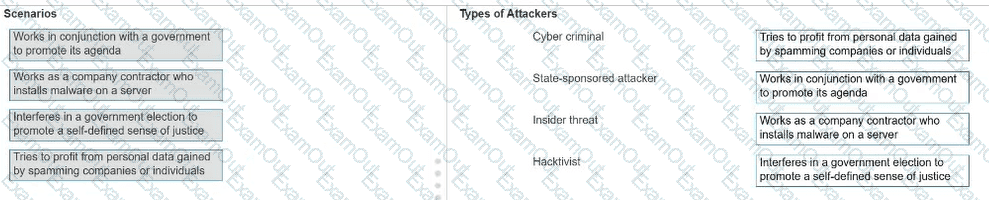
Move each scenario from the list on the left to the correct type of attacker on the right.
Note: You will receive partial credit for each correct answer.