Which of the following is a recommend tip for dealing with problems when launching and attaching to Browser Applications?
A Process Definition Document, for a new process to open ISA accounts, specifies that the value “2008 Cash ISA” is to be entered into the Product Selection field of the following screen:
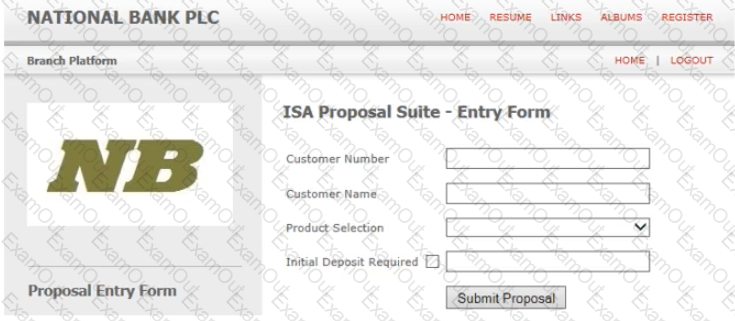
The Product Selection field is a drop down menu with the following options available:
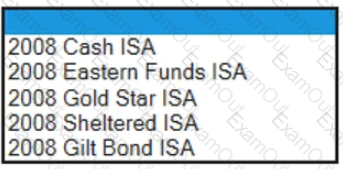
According to Best Practice, which of the following design options are correct for populating the Product Selection field with the value 2008 Cash ISA:
A PDD has been created which includes a requirement to log in to an application called CDS. The CDS application only allows a user account to be logged into the application on one machine at a time. The client wishes to hold the credentials for logging into CDS in the Blue Prism Credential store.
It has been calculated that the automated solution will require 3 resource PC's to enable the case volume to be worked within SLA’s.
Which is the most appropriate design decision to accommodate the above requirements?
A Process is fed cases to work from a spreadsheet held in a shared drive. The location of the shared drive is different between Development and Production environments. How should this be managed?
Which of the following accurately describes best practice when work is sourced from an application's workflow system?
Study the process flow below:
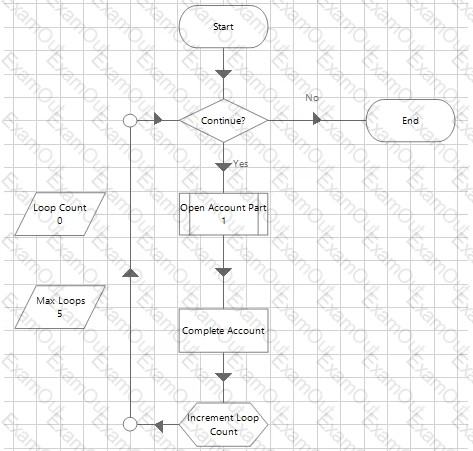
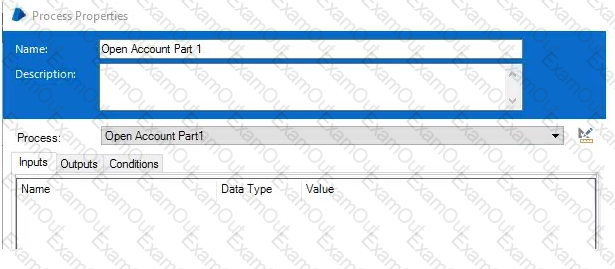


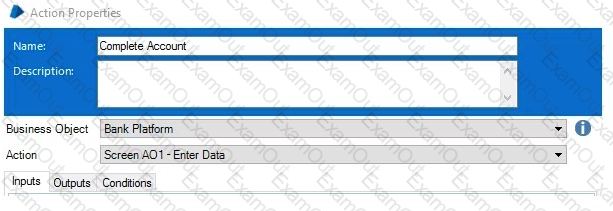
The initial values for the Loop Count and Max Loop data items are 0 and 5 respectively.
How many times will the Business Objects Action ‘Screen AO1 – Enter Data’ be read into memory during the execution of the Process?
A retail bank has promoted 5 Blue Prism processes to production:
Email Poller
Customer Onboarding
Amend Contact Details
Direct Debit Cancellations
Onboarding Reporting
One instance of the email Poller process will run 24/7 feeding work queues for the other two processes.
Two concurrent instances of the Customer Onboarding process will run between 6am and 11pm each day on the same VM.
Two concurrent instances of the Amend Contact Details process will run between 8am and 8pm each day on two VMs.
One instance of the Direct Debit Cancellations process will run between 6am and 4pm each day on the same VM as the Email Poller process. The scheduler that starts the Direct Debit Cancellations process is configured to run the Onboarding Reporting process when the Direct Debit Cancellations process has successfully completed.
How many robot licenses are required?
Which of the following statements, about interfacing with browser applications are true? (Choose three.)
Which of the following are correct? (Choose three.)
Which of the following does the Blue Prism Login Agent functionality support? (Choose three.)

