Which of the following statements regarding Blue Prism Login Agent are true? (Select all that apply.)
Which of the following statements is true regarding the automation of Java applications? (Choose two.)
A business requirement exists to be able to distinguish between cases that have failed due to ‘not being an adult’ and cases that have failed due to ‘invalid ID’ based on the exception detail Blue Prism has captured. The following Process configuration has been built as a solution.
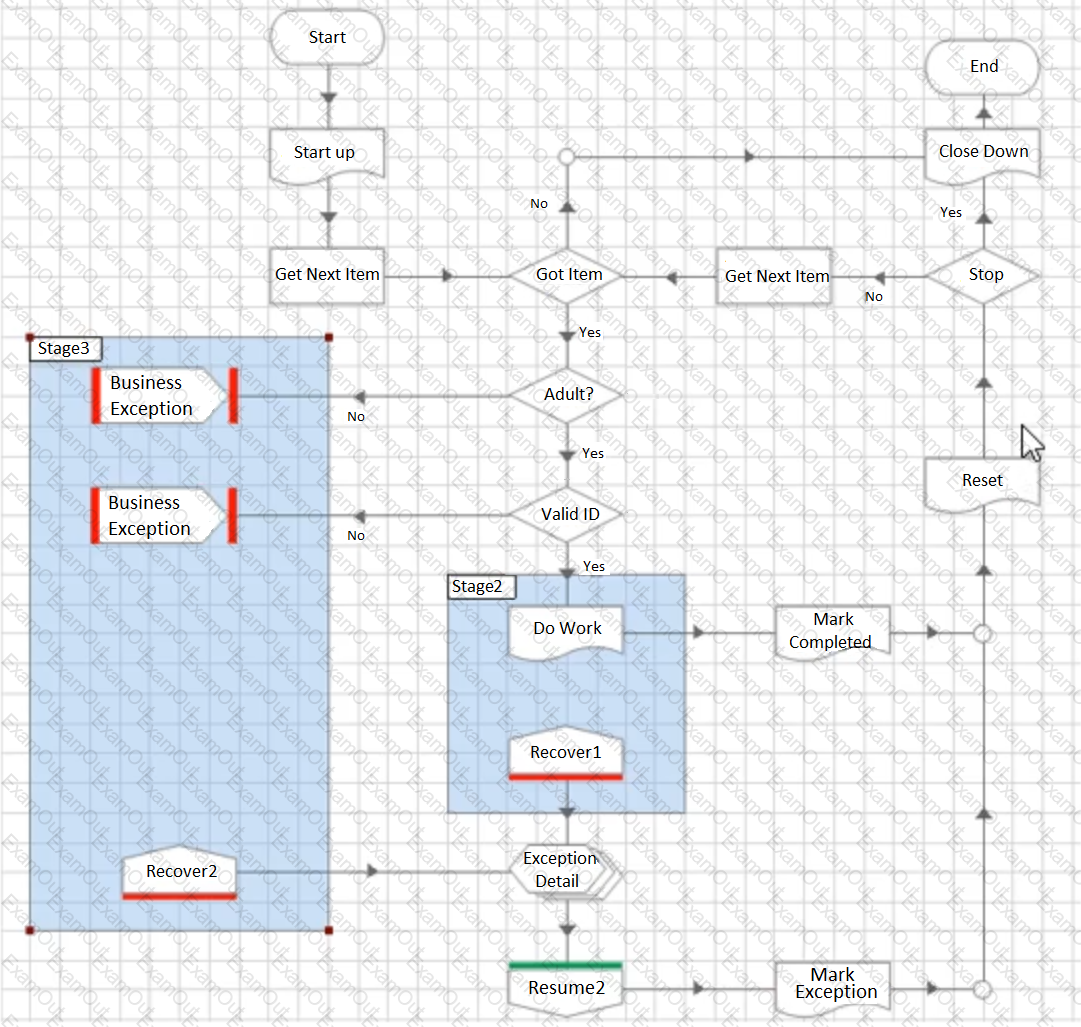
Which of the following statements are correct?
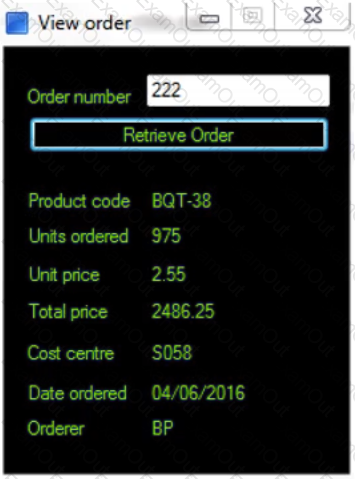
The following screen displays order details in a client’s order system application. An order is entered into the Order number field and the details for that order are displayed. There is a requirement to read the Product code value from the resulting display. The Product code will vary between orders.
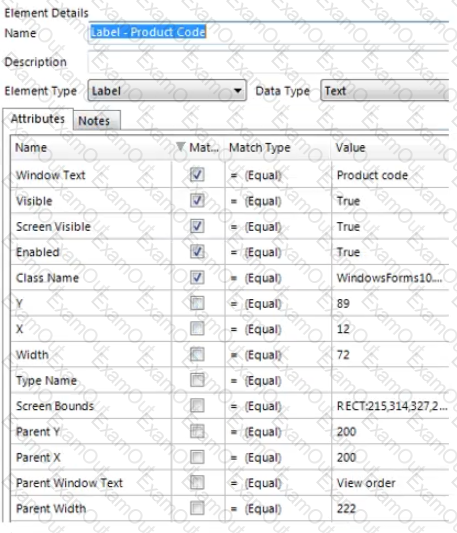
The Product Code label has been successfully spied and the following attributes have been returned:
The Product Code value field has been spied and the following attribute set has been selected:
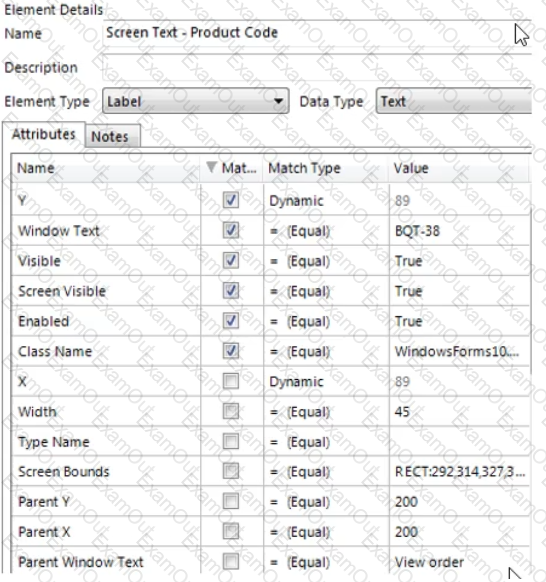
In order to ensure a consistent match for the Screen Text – Product Code element, which of the following statements must be considered:
1. The Dynamic value of the Y attribute for the Screen Text – Product Code element must be derived from the Y attribute of the Label –Product Code element
2. The Y attribute of the Label –Product Code element cannot be derived as it is not checked
3. The Y attribute for the Screen Text – Product Code element must be set to a Match Type of ‘Equal’
4. The Window Text attribute for the Screen Text – Product Code element must be set to a Match Type of ‘Wildcard’
5. The Window Text attribute for the Screen Text – Product Code element must be un-checked
Which of the following techniques is most suitable for extracting text from a PDF Document which originated as a Microsoft Word Document and was saved as a read only PDF?

