What is the easiest way to steal cryptocurrency from a user?
Which of the following is designed to allow someone to prove they know a secret without revealing it?
Spinning up a large number of temporary mining servers is likely part of what type of attack?
Which of the following attacks takes advantage of the fact that transaction information is posted on the blockchain to infer sensitive information?
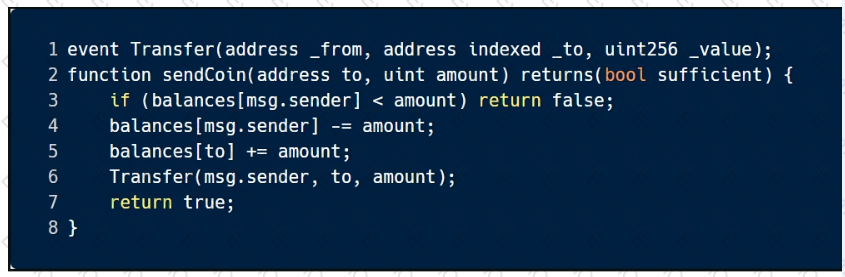
This sample code is vulnerable to which of the following attacks? Select all that apply.
Determining if a transaction is part of the distributed ledger is less computationally intensive in DAG-based solutions than in blockchain
Data subject to deletion procedures should be stored encrypted on-chain.
Scanning against a list of common vulnerabilities is an important component of smart contract auditing.
Which of the following blockchains does NOT use broadcast communications?
Which smart contract vulnerability allows an attacker to make a profit off a smart contract cryptocurrency exchange like Bancor?

