Which smart contract auditing strategy involves graphing how the code executes and looks for anomalies?
Sidechains can benefit the mainchain in what ways? Select all that apply
The List hack demonstrated that biockchains using short addresses are exploitable
The decentralization of the blockchain makes it immune to traditional Denial of Service attacks
Which of the following attacks is designed to bypass the protections provided by digital signatures?
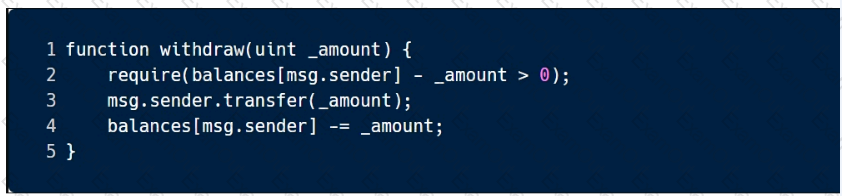
This sample code is vulnerable to which of the following attacks? Select all that apply.
All smart contracts are audited for correctness and checked for malicious code before being uploaded to the blockchain.
This sample code is vulnerable to which of the following attacks? Select all that apply
Which of the following blockchains separates transaction validation and ordering of transactions in blocks into separate steps?
Which types of network attacks focus on partitioning the blockchain network? Select all that apply

