You are taking your package from the source environment and importing it into the target environment.
Review the errors encountered during inspection:
What is the first action you should take to Investigate the issue?
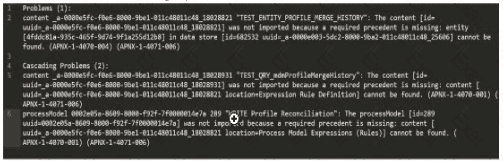
Check whether the object (UUID ending in 18028821) is included in this package
Check whether the object (UUD ending in 7t00000i4e7a) is included in this package
Check whether the object (UUID ending in 25606) is included in this package
Check whether the object (UUID ending in 18028931) is included in this package
The Answer Is:
BExplanation:
The error log provided indicates issues during the package import into the target environment, with multiple objects failing to import due to missing precedents. The key error messages highlight specific UUIDs associated with objects that cannot be resolved. The first error listed states:
"‘TEST_ENTITY_PROFILE_MERGE_HISTORY’: The content [id=uuid-a-0000m5fc-f0e6-8000-9b01-011c48011c48, 18028821] was not imported because a required precedent is missing: entity [uuid=a-0000m5fc-f0e6-8000-9b01-011c48011c48, 18028821] cannot be found..."
According to Appian’s Package Deployment Best Practices, when importing a package, the first step in troubleshooting is to identify the root cause of the failure. The initial error in the log points to an entity object with a UUID ending in 18028821, which failed to import due to a missing precedent. This suggests that the object itself or one of its dependencies (e.g., a data store or related entity) is either missing from the package or not present in the target environment.
Option A (Check whether the object (UUID ending in 18028821) is included in this package): This is the correct first action. Since the first error references this UUID, verifying its inclusion in the package is the logical starting point. If it’s missing, the package export from the source environment was incomplete. If it’s included but still fails, the precedent issue (e.g., a missing data store) needs further investigation.
Option B (Check whether the object (UUID ending in 7t00000i4e7a) is included in this package): This appears to be a typo or corrupted UUID (likely intended as something like "7t000014e7a" or similar), and it’s not referenced in the primary error. It’s mentioned later in the log but is not the first issue to address.
Option C (Check whether the object (UUID ending in 25606) is included in this package): This UUID is associated with a data store error later in the log, but it’s not the first reported issue.
Option D (Check whether the object (UUID ending in 18028931) is included in this package): This UUID is mentioned in a subsequent error related to a process model or expression rule, but it’s not the initial failure point.
Appian recommends addressing errors in the order they appear in the log to systematically resolve dependencies. Thus, starting with the object ending in 18028821 is the priority.
While working on an application, you have identified oddities and breaks in some of your components. How can you guarantee that this mistake does not happen again in the future?
Design and communicate a best practice that dictates designers only work within the confines of their own application.
Ensure that the application administrator group only has designers from that application’s team.
Create a best practice that enforces a peer review of the deletion of any components within the application.
Provide Appian developers with the “Designer” permissions role within Appian. Ensure that they have only basic user rights and assign them the permissions to administer their application.
The Answer Is:
CExplanation:
Comprehensive and Detailed In-Depth Explanation:
As an Appian Lead Developer, preventing recurring “oddities and breaks” in application components requires addressing root causes—likely tied to human error, lack of oversight, or uncontrolled changes—while leveraging Appian’s governance and collaboration features. The question implies a past mistake (e.g., accidental deletions or modifications) and seeks a proactive, sustainable solution. Let’s evaluate each option based on Appian’s official documentation and best practices:
A. Design and communicate a best practice that dictates designers only work within the confines of their own application:This suggests restricting designers to their assigned applications via a policy. While Appian supports application-level security (e.g., Designer role scoped to specific applications), this approach relies on voluntary compliance rather than enforcement. It doesn’t directly address “oddities and breaks”—e.g., a designer could still mistakenly alter components within their own application. Appian’s documentation emphasizes technical controls and process rigor over broad guidelines, making this insufficient as a guarantee.
B. Ensure that the application administrator group only has designers from that application’s team:This involves configuring security so only team-specific designers have Administrator rights to the application (via Appian’s Security settings). While this limits external interference, it doesn’t prevent internal mistakes (e.g., a team designer deleting a critical component). Appian’s security model already restricts access by default, and the issue isn’t about unauthorized access but rather component integrity. This step is a hygiene factor, not a direct solution to the problem, and fails to “guarantee” prevention.
C. Create a best practice that enforces a peer review of the deletion of any components within the application:This is the best choice. A peer review process for deletions (e.g., process models, interfaces, or records) introduces a checkpoint to catch errors before they impact the application. In Appian, deletions are permanent and can cascade (e.g., breaking dependencies), aligning with the “oddities and breaks” described. While Appian doesn’t natively enforce peer reviews, this can be implemented via team workflows—e.g., using Appian’s collaboration tools (like Comments or Tasks) or integrating with version control practices during deployment. Appian Lead Developer training emphasizes change management and peer validation to maintain application stability, making this a robust, preventive measure that directly addresses the root cause.
D. Provide Appian developers with the “Designer” permissions role within Appian. Ensure that they have only basic user rights and assign them the permissions to administer their application:This option is confusingly worded but seems to suggest granting Designer system role permissions (a high-level privilege) while limiting developers to Viewer rights system-wide, with Administrator rights only for their application. In Appian, the “Designer” system role grants broad platform access (e.g., creating applications), which contradicts “basic user rights” (Viewer role). Regardless, adjusting permissions doesn’t prevent mistakes—it only controls who can make them. The issue isn’t about access but about error prevention, so this option misses the mark and is impractical due to its contradictory setup.
Conclusion: Creating a best practice that enforces a peer review of the deletion of any components (C) is the strongest solution. It directly mitigates the risk of “oddities and breaks” by adding oversight to destructive actions, leveraging team collaboration, and aligning with Appian’s recommended governance practices. Implementation could involve documenting the process, training the team, and using Appian’s monitoring tools (e.g., Application Properties history) to track changes—ensuring mistakes are caught before deployment. This provides the closest guarantee to preventing recurrence.
You need to design a complex Appian integration to call a RESTful API. The RESTful API will be used to update a case in a customer’s legacy system.
What are three prerequisites for designing the integration?
Define the HTTP method that the integration will use.
Understand the content of the expected body, including each field type and their limits.
Understand whether this integration will be used in an interface or in a process model.
Understand the different error codes managed by the API and the process of error handling in Appian.
Understand the business rules to be applied to ensure the business logic of the data.
The Answer Is:
A, B, DExplanation:
Comprehensive and Detailed In-Depth Explanation:
As an Appian Lead Developer, designing a complex integration to a RESTful API for updating a case in a legacy system requires a structured approach to ensure reliability, performance, and alignment with business needs. The integration involves sending a JSON payload (implied by the context) and handling responses, so the focus is on technical and functional prerequisites. Let’s evaluate each option:
A. Define the HTTP method that the integration will use:This is a primary prerequisite. RESTful APIs use HTTP methods (e.g., POST, PUT, GET) to define the operation—here, updating a case likely requires PUT or POST. Appian’s Connected System and Integration objects require specifying the method to configure the HTTP request correctly. Understanding the API’s method ensures the integration aligns with its design, making this essential for design. Appian’s documentation emphasizes choosing the correct HTTP method as a foundational step.
B. Understand the content of the expected body, including each field type and their limits:This is also critical. The JSON payload for updating a case includes fields (e.g., text, dates, numbers), and the API expects a specific structure with field types (e.g., string, integer) and limits (e.g., max length, size constraints). In Appian, the Integration object requires a dictionary or CDT to construct the body, and mismatches (e.g., wrong types, exceeding limits) cause errors (e.g., 400 Bad Request). Appian’s best practices mandate understanding the API schema to ensure data compatibility, making this a key prerequisite.
C. Understand whether this integration will be used in an interface or in a process model:While knowing the context (interface vs. process model) is useful for design (e.g., synchronous vs. asynchronous calls), it’s not a prerequisite for the integration itself—it’s a usage consideration. Appian supports integrations in both contexts, and the integration’s design (e.g., HTTP method, body) remains the same. This is secondary to technical API details, so it’s not among the top three prerequisites.
D. Understand the different error codes managed by the API and the process of error handling in Appian:This is essential. RESTful APIs return HTTP status codes (e.g., 200 OK, 400 Bad Request, 500 Internal Server Error), and the customer’s API likely documents these for failure scenarios (e.g., invalid data, server issues). Appian’s Integration objects can handle errors via error mappings or process models, and understanding these codes ensures robust error handling (e.g., retry logic, user notifications). Appian’s documentation stresses error handling as a core design element for reliable integrations, making this a primary prerequisite.
E. Understand the business rules to be applied to ensure the business logic of the data:While business rules (e.g., validating case data before sending) are important for the overall application, they aren’t a prerequisite for designing the integration itself—they’re part of the application logic (e.g., process model or interface). The integration focuses on technical interaction with the API, not business validation, which can be handled separately in Appian. This is a secondary concern, not a core design requirement for the integration.
Conclusion: The three prerequisites are A (define the HTTP method), B (understand the body content and limits), and D (understand error codes and handling). These ensure the integration is technically sound, compatible with the API, and resilient to errors—critical for a complex RESTful API integration in Appian.

