You want to search for two words within five words of each other. Which search request
would accomplish this function?
You are converting one image file format to another using FTK Imager. Why are the hash
values of the original image and the resulting new image the same?
In FTK, which two formats can be used to export an E-mail message? (Choose two.)
Using the FTK Report Wizard, which two options are available in the Bookmarks - A
window? (Choose two.)
Which statement is true about Processes to Perform in FTK?
Click the Exhibit button.
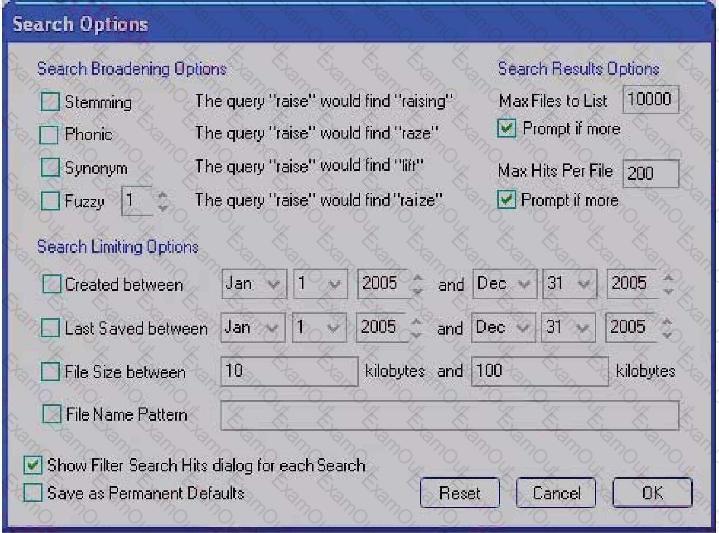
You need to search for specific data that are located in a Microsoft Word document. You do not know the exact spelling of this datA. Using the Index Search Options as displayed in the exhibit, which changes do you make in the Broadening Options and Search Limiting Options containers?
While analyzing unallocated space, you locate what appears to be a 64-bit Windows date and
time. Which FTK Imager feature allows you display the information as a date and time?
Which type of evidence can be added to FTK Imager?
What is the most effective method to facilitate successful password recovery?
Click the Exhibit button.
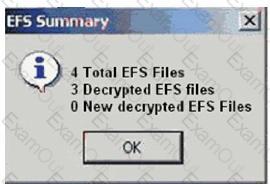
When decrypting EFS files in a case, you receive the result shown in the exhibit. What is the most plausible explanation for this result?

