Which of the following statements BEST describes how test cases are derived from a use case?
During which stage of the fundamental test process is the testability of requirements evaluated?
Which of the following is a key difference between black box and white box test design techniques?
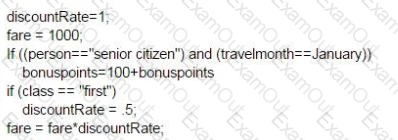
For the code fragment given below, which answer correctly represents minimum tests required for statement and branch coverage respectively?
Which of the following would you NOT expect to see on an incident report from test execution?
Which one of the following statements about techniques for estimating test effort is correct?
Which one of the following statements about testing techniques is TRUE?
What does the term Pesticide paradox' refer to?
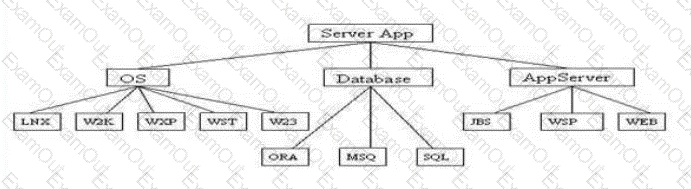
The following diagram lists various types of operating systems, databases and application servers supported by the application under test. For complete coverage of all combinations, how many combinations of the above are to be tested?
Which of the following is NOT an example of a typical risk-based testing activity?

