Which two capabilities can an administrator use to ensure availability within Docker Containers? (Select two.)
Where is the sysoffline trigger executed if a node goes into a jeopardy state or leaves the cluster?
As part of the consolidation efforts in a data center, the administrator decides to merge two two-node Veritas Cluster Server (VCS) clusters into a four-node VCS cluster. The source and target clusters are on the same networks for LLT communication. The administrator performs the following tasks as preparation for the merge while both clusters are still running:
modifies /etc/llttab files on the source cluster systems so the cluster ID is changed to the cluster ID of the target cluster
modifies /etc/llthosts files on all systems to include the four nodes
modifies /etc/gabtab files on all systems to require the four systems to seed
ensures the source cluster systems can see the fencing disks used by the target cluster
copies the fencing configuration files from the target cluster systems to the source cluster systems
adds the source cluster systems to the target cluster configuration using the hasys –add command
After the preparation is complete, the administrator stops the source cluster leaving the applications running, then stops the whole communication stack and restarts it in the correct order. When the administrator attempts to start the cluster again on the source cluster systems, they fail to join the four-node cluster.
Which preparation step that the administrator failed to perform is preventing the source cluster systems from joining the four-node cluster?
An installed cluster has been licensed with the keyless licensing option. The administrator has yet to configure the cluster to be managed by Veritas InfoScale Operations Manager (VIOM). What will happen when 60 days have passed since installation?
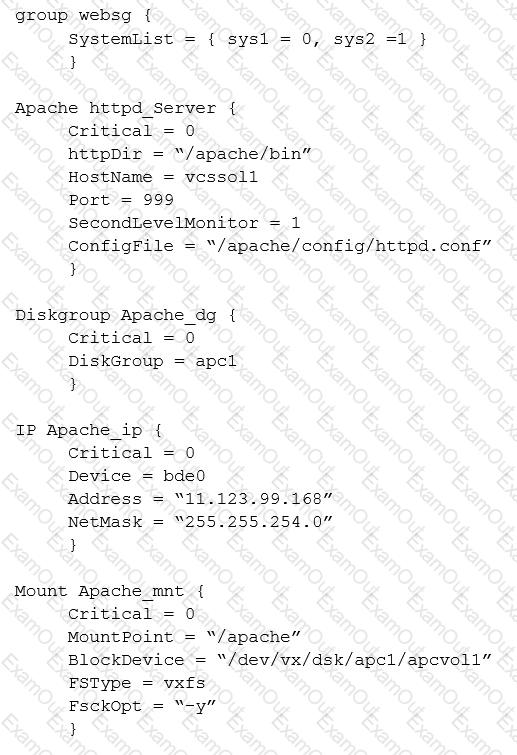
What are two effects of a failed resource in the service group configuration below? (Select two.)
The administrator of a four-node Veritas cluster has configured notifications as highly available for all notification methods. How many notification manager resources are running when all nodes are considered?
An administrator needs to create a new two-node cluster.
Which configuration allows the administrator to firm a cluster using Veritas InfoScale Availability?
Which agent is used to automatically refresh fencing keys if they are missing on fencing servers or disks?
Which two meters can the administrator use for the system capacity calculation when the FailOverPolicy of a service group is set to BiggestAvailable? (Select two.)
An administrator is adding a node to a running cluster. The administrator has successfully installed Veritas InfoScale Availability 7.1 and has configured and started LLT.
Which command will allow the new node to communicate with the cluster?

