An architect receives a request to apply distributed firewall in a customer environment without making changes to the network and vSphere environment. The architect decides to use Distributed Firewall on VDS.
Which two of the following requirements must be met in the environment? (Choose two.)
Which CLI command shows syslog on NSX Manager?
Which of the two following characteristics about NAT64 are true? (Choose two.)
Refer to the exhibits.
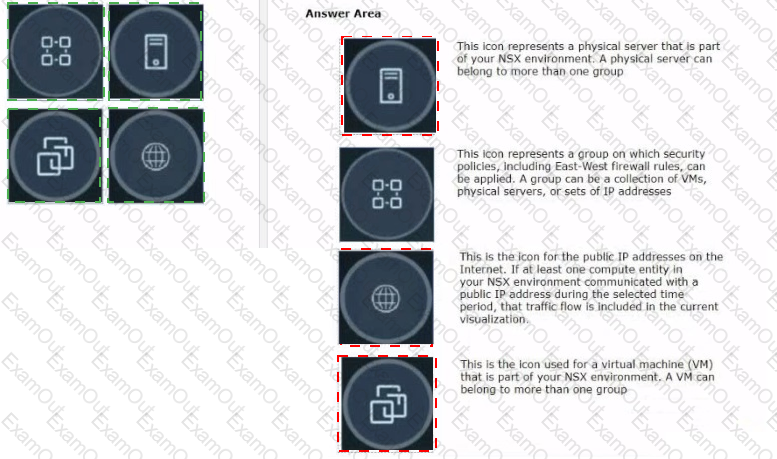
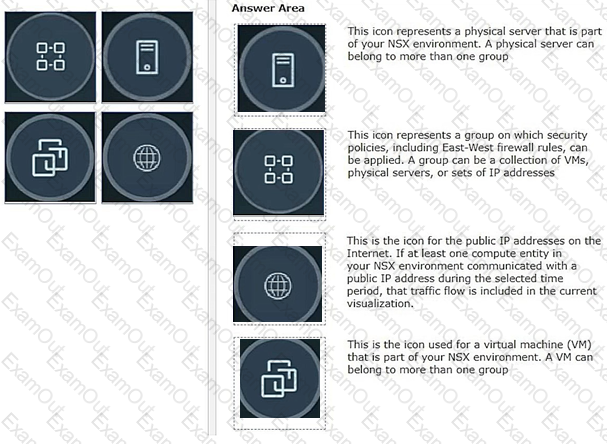
Drag and drop the NSX graphic element icons on the left found in an NSX Intelligence visualization graph to Its correct description on the right.

An administrator has deployed 10 Edge Transport Nodes in their NSX Environment, but has forgotten to specify an NTP server during the deployment.
What is the efficient way to add an NTP server to all 10 Edge Transport Nodes?
Which three DHCP Services are supported by NSX? (Choose three.)
Which statement is true about an alarm in a Suppressed state?
Which two choices are use cases for Distributed Intrusion Detection? (Choose two.)
Which troubleshooting step will resolve an error with code 1001 during the configuration of a time-based firewall rule?
What are the four types of role-based access control (RBAC) permissions? (Choose four.)