The Intrusion Prevention Protection Module is enabled and a Recommendation Scan is run to identify vulnerabilities on a Windows Server 2016 computer. How can you insure that the list of recommendations is always kept up to date?
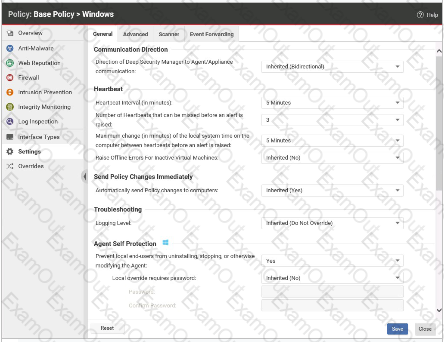
Which of the following statements is correct regarding the policy settings displayed in the exihibit?
Which of the following statements is true regarding the use of the Firewall Protection Module in Deep Security?
Which Deep Security Protection Modules can be used to provide runtime protection for the Kubernetes and Docker platforms? Select all that apply.
A Recommendation Scan is run to determine which Intrusion Prevention rules are appropriate for a Server. The scan is configured to apply the suggested rules automatically and ongoing scans are enabled. Some time later, an operating system patch is applied. How can you de-termine which Intrusion Prevention rules are no longer needed on this Server?
Which of the following are valid methods for forwarding Event information from Deep Secu-rity? Select all that apply.
Which of the following Protection Modules does not benefit from Recommendation Scans?
Which of the following Firewall rule actions will allow data packets to pass through the Firewall Protection Module without being subjected to analysis by the Intrusion Prevention Protection Module?
The maximum disk space limit for the Identified Files folder is reached. What is the expected Deep Security Agent behavior in this scenario?
Which of the following statements is true regarding Intrusion Prevention rules?

