What ports can be queried to perform a DNS zone transfer?
53/TCP
53/UDP
Both 1 and 2
None of the above
The Answer Is:
AExplanation:
A DNS zone transfer involves replicating the DNS zone data (e.g., all records for a domain) from a primary to a secondary DNS server, requiring a reliable transport mechanism.
Why A is correct:DNS zone transfers use TCP port 53 because TCP ensures reliable,ordered delivery of data, which is critical for transferring large zone files. CNSP notes that TCP is the standard protocol for zone transfers (e.g., AXFR requests), as specified in RFC 5936.
Why other options are incorrect:
B. 53/UDP:UDP port 53 is used for standard DNS queries and responses due to its speed and lower overhead, but it is not suitable for zone transfers, which require reliability over speed.
C. Both 1 and 2:This is incorrect because zone transfers are exclusively TCP-based, not UDP-based.
D. None of the above:Incorrect, as 53/TCP is the correct port for DNS zone transfers.
References:CNSP "DNS Security Practices" (Section on Zone Transfers) specifies TCP port 53 as the protocol for secure and reliable zone transfer operations.
Which SMB (Server Message Block) network protocol version introduced support for encrypting SMB traffic?
SMBv1
SMBv2
SMBv3
None of the above
The Answer Is:
CExplanation:
The SMB protocol, used for file and printer sharing, has evolved across versions, with significant security enhancements in later iterations.
Why C is correct:SMBv3, introduced with Windows 8 and Server 2012, added native support for encrypting SMB traffic. This feature uses AES-CCM encryption to protect data in transit, addressing vulnerabilities in earlier versions. CNSP notes SMBv3’s encryption as a critical security improvement.
Why other options are incorrect:
A. SMBv1:Lacks encryption support and is considered insecure, often disabled due to vulnerabilities like WannaCry exploitation.
B. SMBv2:Introduces performance improvements but does not support encryption natively.
D. None of the above:Incorrect, as SMBv3 is the version that introduced encryption.
References:CNSP "File Sharing Protocols" (Section on SMB Versions) details SMBv3’s encryption feature, contrasting it with the limitations of SMBv1 and SMBv2.
Which of the following is a valid DNS record type?
NAPTR record
SRV record
TXT record
All of the above
The Answer Is:
DExplanation:
DNS (Domain Name System) records define how domain names are mapped to various types of data, each serving a specific purpose in network operations. The question asks for valid DNS record types, and all listed options are recognized.
Why D is correct:
A. NAPTR record:The Naming Authority Pointer (NAPTR) record is used for service discovery and mapping domain names to services, protocols, and ports (e.g., in SIP or ENUM systems).
B. SRV record:The Service (SRV) record specifies the hostname and port for specific services (e.g., LDAP, XMPP), aiding in service location.
C. TXT record:The Text (TXT) record stores arbitrary text data, often for SPF, DKIM, or domain verification.All are valid DNS record types per RFC standards and CNSP documentation, making "All of the above" the correct answer.
Why other options are incomplete:A, B, or C alone exclude other valid types listed, so D is the most comprehensive response.
References:CNSP "DNS Configuration and Security" (Section on Record Types) lists NAPTR, SRV, and TXT as valid DNS records, detailing their uses in network services.
According to the screenshot below, which of the following statements are correct?
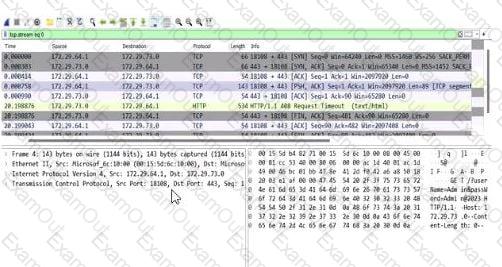
The application is running on port 443 and the HTTPS protocol.
The credentials have been submitted over the HTTP protocol.
The credentials have been submitted over the HTTPS protocol.
The application is running on port 80 and the HTTP protocol.
The Answer Is:
AExplanation:
The screenshot is from Wireshark, a network protocol analyzer, displaying captured network traffic. The relevant columns include the source and destination IP addresses, ports, protocol, and additional information about the packets. Let’s break down the details:
Destination Port Analysis:The screenshot shows multiple packets with a destination port of 443 (e.g., in the "Destination" column, entries like "172.72.61.9:443"). Port 443 is the default port for HTTPS (HTTP Secure), which is HTTP traffic encrypted using SSL/TLS. This indicates that the application is communicating over HTTPS.
Protocol Analysis:The "Protocol" column lists "TLSv1.2" for most packets (e.g., frame numbers 2000084, 2000086). TLS (Transport Layer Security) is the cryptographic protocol used by HTTPS to secure HTTP communications. This confirms that the traffic is HTTPS, not plain HTTP.
Packet Details:The "Info" column provides additional context, such as "Application Data" for TLS packets, indicating encrypted application-layer data (typical of HTTPS). There are also HTTP packets (e.g., frame 2000088), but these are likely part of the HTTPS session (e.g., HTTP/2 over TLS, as noted by "HTTP2").
Now, let’s evaluate the options:
Option A: "The application is running on port 443 and the HTTPS protocol."This is correct. The destination port 443 and the use of TLSv1.2 confirm that the application is using HTTPS. HTTPS is the standard protocol for secure web communication, and port 443 is its designated port. CNSP documentation emphasizes that HTTPS traffic on port 443 indicates a secure application-layer protocol, often used for web applications handling sensitive data.
Option B: "The credentials have been submitted over the HTTP protocol."This is incorrect. HTTP typically uses port 80, but the screenshot shows traffic on port 443 with TLS, indicating HTTPS. Credentials submitted over this connection would be encrypted via HTTPS, not sent in plaintext over HTTP. CNSP highlights the security risks of HTTP for credential submission due to lack of encryption, which isn’t the case here.
Option C: "The credentials have been submitted over the HTTPS protocol."While this statement could be true (since HTTPS is in use, any credentials would likely be submitted securely), the question asks for the "correct" statement based on the screenshot. The screenshot doesn’t explicitly show credential submission (e.g., a POST request withform data); it only shows the protocol and port. Option A is more directly supported by the screenshot as it focuses on the application’s protocol and port, not the specific action of credential submission. CNSP notes that HTTPS ensures confidentiality, but this option requires more specific evidence of credentials.
Option D: "The application is running on port 80 and the HTTP protocol."This is incorrect. Port 80 is the default for HTTP, but the screenshot clearly shows port 443 and TLS, indicating HTTPS. CNSP documentation contrasts HTTP (port 80, unencrypted) with HTTPS (port 443, encrypted), making this option invalid.
Conclusion:Option A is the most accurate and comprehensive statement directly supported by the screenshot, confirming the application’s use of port 443 and HTTPS. While Option C might be true in a broader context, it’s less definitive without explicit evidence of credential submission in the captured packets.
References:CNSP "Network Traffic Analysis" (Section on Protocol Identification) explains that port 443 with TLS indicates HTTPS, and contrasts it with HTTP on port 80. The "Wireshark Analysis" section further details how to interpret destination ports and protocol fields for identifying application-layer protocols.
How many octets are there in an IPv6 address?
16
32
64
128
The Answer Is:
AExplanation:
An IPv6 address, defined in RFC 4291, is a 128-bit address designed to replace IPv4’s 32-bit scheme, vastly expanding address space (2^128 vs. 2^32). Anoctetis 8 bits (1 byte). To calculate octets in IPv6:
128 bits ÷ 8 bits/octet =16 octets.
Representation:
IPv6 is written as eight 16-bit hexadecimal blocks (e.g., 2001:0db8:85a3:0000:0000:8a2e:0370:7334), separated by colons.
Each block is 16 bits (2 bytes), so 8 blocks = 16 octets.
Contrast with IPv4 (e.g., 192.168.0.1), which has 4 octets (32 bits).
Technical Note:Your original input flagged this question’s phrasing as potentially misleading, suggesting "octets" is an IPv4 term, while IPv6 uses "16-bit groups" or "hextets." While technically accurate (RFC 4291 uses "16-bit blocks"), "octets" remains a common, if informal, term in security contexts for byte-wise analysis (e.g., packet crafting). CNSP might use "octets" to test byte-level understanding, though "groups" is more precise for IPv6. Here, 16 octets (128 bits) is correct either way.
Security Implications:IPv6’s larger address space complicates scanning (e.g., Nmap struggles with 2^128 possibilities) but introduces risks like misconfigured Neighbor Discovery Protocol (NDP). Understanding its structure aids in firewall rules and IDS signatures.
Why other options are incorrect:
B. 32:Implies 256 bits (32 × 8), far exceeding IPv6’s 128-bit design.
C. 64:Suggests 512 bits (64 × 8), unrelated to IPv6 or any IP standard.
D. 128:Misinterprets octets as bits; 128 bits = 16 octets, not 128 octets.
Real-World Context:IPv6 packet analysis (e.g., Wireshark) breaks addresses into 16 octets for raw data inspection.References:CNSP Official Documentation (IPv6 Networking); RFC 4291 (IP Version 6 Addressing Architecture).
Which of the following is not a DDoS attack?
SYN Flood
NTP Amplification
UDP Flood
Brute Force
The Answer Is:
DExplanation:
DDoS (Distributed Denial of Service) attacks aim to overwhelm a target’s resources with excessive traffic, disrupting availability, whereas other attack types target different goals.
Why D is correct:Brute force attacks focus on guessing credentials (e.g., passwords) to gain unauthorized access, not on denying service. CNSP classifies it as an authentication attack, not a DDoS method.
Why other options are incorrect:
A:SYN Flood exhausts TCP connection resources, a classic DDoS attack.
B:NTP Amplification leverages amplified responses to flood targets, a DDoS technique.
C:UDP Flood overwhelms a system with UDP packets, another DDoS method.
References:CNSP "DDoS Attack Types" (Section on Attack Classification) excludes brute force from DDoS categories, listing SYN, NTP, and UDP floods as examples.
What ports does an MSSQL server typically use?
1433/TCP, 2433/UDP, and 3433/TCP
1433/TCP, 1434/UDP, and 1434/TCP
1433/TCP, 2433/UDP, and 1434/TCP
1533/TCP, 1434/UDP, and 2434/TCP
The Answer Is:
BExplanation:
Microsoft SQL Server (MSSQL) relies on specific ports for its core services, as defined by Microsoft and registered with IANA:
1433/TCP:The default port for the SQL Server Database Engine. Clients connect here for querying databases (e.g., via ODBC or JDBC). It’s a well-known port, making it a frequent target for attacks if exposed.
1434/UDP:Used by theSQL Server Browser Service, which listens for incoming requests and redirects clients to the correct port/instance (especially for named instances). It’s critical for discovering dynamic ports when 1433 isn’t used.
1434/TCP:Less commonly highlighted but used in some configurations, such as dedicated admin connections (DAC) or when the Browser Service responds over TCP for specific instances. While 1433/TCP is the primary engine port, 1434/TCP can be involved in multi-instance setups.
Technical Details:
Ports can be customized (e.g., via SQL Server Configuration Manager), but these are defaults.
Named instances often use dynamic ports (allocated from the ephemeral range), with the Browser Service (1434/UDP) guiding clients to them.
Firewalls must allow these ports for MSSQL to function externally, posing risks if not secured (e.g., brute-force attacks on 1433/TCP).
Security Implications:CNSP likely covers MSSQL port security, as vulnerabilities like SQL Slammer (2003) exploited 1434/UDP misconfigurations. Hardening includes restricting access, changing defaults, and monitoring traffic.
Why other options are incorrect:
A. 1433/TCP, 2433/UDP, 3433/TCP:2433/UDP and 3433/TCP are not MSSQL standards; they’re likely typos or unrelated ports.
C. 1433/TCP, 2433/UDP, 1434/TCP:2433/UDP is incorrect; 1434/UDP is the Browser Service port.
D. 1533/TCP, 1434/UDP, 2434/TCP:1533/TCP and 2434/TCP aren’t associated with MSSQL; they deviate from documented defaults.
Real-World Context:Tools like netstat -an | find "1433" on Windows confirm MSSQL’s port usage during audits.References:CNSP Official Documentation (Database Security and Ports); Microsoft SQL Server Documentation, IANA Port Registry.
In a Linux-based architecture, what does the /mnt directory contain?
Temporary-mounted filesystems
System configuration files and initialization scripts
Loadable driver modules needed to boot the system
System files which represent the current state of the kernel
The Answer Is:
AExplanation:
The LinuxFilesystem Hierarchy Standard (FHS), per FHS 3.0, defines directory purposes:
/mnt:Designated fortemporarily mounted filesystems, typically by system administrators.
Use: Mount points for removable media (e.g., USB drives: mount /dev/sdb1 /mnt/usb) or network shares (e.g., NFS).
Nature: Transient, user-managed, not persistent across reboots (unlike /etc/fstab mounts).
Contrast:
/media:Auto-mounts removable devices (e.g., by desktop environments like GNOME).
/mnt vs. /media:/mnt is manual, /media is system-driven.
Technical Details:
Empty by default; subdirectories (e.g., /mnt/usb) are created as needed.
Permissions: Typically root-owned (0755), requiring sudo for mounts.
Security Implications:Misconfigured /mnt mounts (e.g., world-writable) risk unauthorized access. CNSP likely covers mount security (e.g., nosuid option).
Why other options are incorrect:
B. System config/init scripts:Found in /etc (e.g., /etc/passwd, /etc/init.d).
C. Driver modules:Located in /lib/modules/
D. Kernel state:Resides in /proc (e.g., /proc/cpuinfo).
Real-World Context:Admins mount ISOs at /mnt during server provisioning (e.g., mount -o loop image.iso /mnt).References:CNSP Official Study Guide (Linux Filesystems); FHS 3.0 Documentation.
What is the response from a closed TCP port which is not behind a firewall?
ICMP message showing Port Unreachable
A FIN and an ACK packet
A RST and an ACK packet
A SYN and an ACK packet
The Answer Is:
CExplanation:
TCP uses a structured handshake, and its response to a connection attempt on a closed port follows a specific protocol when unobstructed by a firewall.
Why C is correct:A closed TCP port responds with a RST (Reset) and ACK (Acknowledgment) packet to terminate the connection attempt immediately. CNSP highlights this as a key scanning indicator.
Why other options are incorrect:
A:ICMP Port Unreachable is for UDP, not TCP.
B:FIN/ACK is for closing active connections, not rejecting new ones.
D:SYN/ACK indicates an open port during the TCP handshake.
References:CNSP "TCP Scanning" (Section on Port Responses) details RST/ACK as the standard closed-port response.
What is the response from a closed TCP port which is behind a firewall?
A FIN and an ACK packet
RST and an ACK packet
A SYN and an ACK packet
No response
The Answer Is:
DExplanation:
TCP (Transmission Control Protocol) uses a three-way handshake (SYN, SYN-ACK, ACK) toestablish connections, as per RFC 793. When a client sends a SYN packet to a port:
Open Port:The server responds with SYN-ACK.
Closed Port (no firewall):The server sends an RST (Reset) packet, often with ACK, to terminate the attempt immediately.
However, when afirewallis present, its configuration dictates the response. Modern firewalls typically operate instealth mode, using a "drop" rule for closed ports rather than a "reject" rule:
Drop:Silently discards the packet without replying, resulting inno response. The client experiences a timeout (e.g., 30 seconds), as no feedback is provided.
Reject:Sends an RST or ICMP "Port Unreachable," but this is less common for security reasons, as it confirms the firewall’s presence.
For a closed TCP port behind a firewall, "no response" (drop) is the standard behavior in secure configurations, minimizing information leakage to attackers. This aligns with CNSP’s focus on firewall best practices to obscure network topology during port scanning (e.g., with Nmap).
Why other options are incorrect:
A. A FIN and an ACK packet:FIN-ACK is used to close anestablishedTCP connection gracefully (e.g., after data transfer), not to respond to an initial SYN on a closed port.
B. RST and an ACK packet:RST-ACK is the host’s response to a closed port without a firewall. A firewall’s drop rule overrides this by silently discarding the packet.
C. A SYN and an ACK packet:SYN-ACK indicates an open port accepting a connection, the opposite of a closed port scenario.
Real-World Context:Tools like Nmap interpret "no response" as "filtered" (firewall likely present) vs. "closed" (RST received), aiding in firewall detection.References:CNSP Official Study Guide (Firewall Operations and TCP/IP); RFC 793 (TCP).

