An administrator needs to add an Application Exception. When the administrator accesses the Application Exception dialog window, applications fail to appear.
What is the likely problem?
You have executed the vxdg -g diskgroup adddisk disk_name= command.
Which switch needs to be added to force VxVM to take the disk media name of the failed disk and assign it to the new replacement disk?
Which action does the Shared Insight Cache (SIC) server take when the whitelist reaches maximum capacity?
An administrator uses the search criteria displayed in the image below.
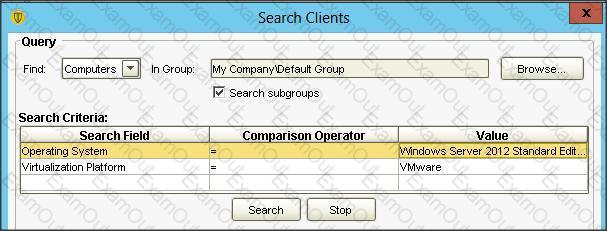
Which results are returned from the query?
In addition to performance improvements, which two benefits does Insight provide? (Select two.)
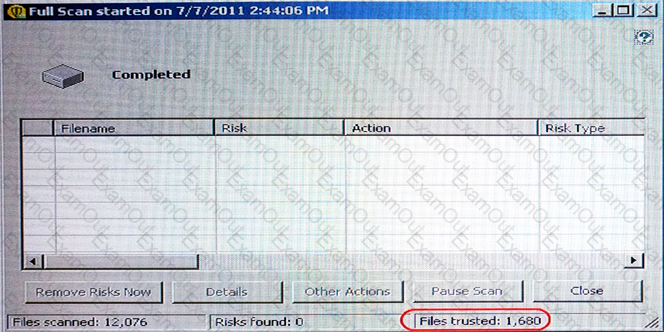
Which settings can impact the Files trusted count?
A company has an application that requires network traffic in both directions to multiple systems at a specific external domain. A firewall rule was created to allow traffic to and from the external domain, but the rule is blocking incoming traffic.
What should an administrator enable in the firewall policy to allow this traffic?
What optional Symantec Endpoint Protection component could an administrator utilize if an organization requires custom reports and queries?
A company allows users to create firewall rules. During the course of business, users are accidentally adding rules that block a custom internal application.
Which steps should the Symantec Endpoint Protection administrator take to prevent users from blocking the custom application?
A threat was detected by Auto-Protect on a client system.
Which command can an administrator run to determine whether additional threats exist?

