Using the outsourcing agent diagram. Which components must be placed in a secure zone? (Choose all that apply.)

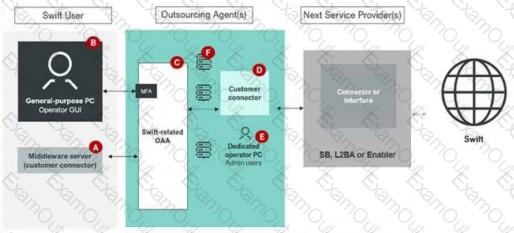
Component A
Component B
Component C
Component D
The Answer Is:
A, C, DExplanation:
The diagram provided represents a Swift user environment with an outsourcing agent, showing various components involved in the Swift workflow. The Swift Customer Security Programme (CSP) mandates specific security controls to protect critical components, particularly those handling Swift-related data or connectivity. Let’s analyze the diagram and determine which components must be placed in asecure zoneas per theCSCF v2024.
Step 1: Understand the Secure Zone Requirement
Asecure zonein the Swift CSP context refers to a segregated, protected environment where critical Swift-related components are isolated from general-purpose systems to minimize risks. This is outlined inControl 1.1: Swift Environment Protectionof theCSCF v2024, which mandates that Swift infrastructure (e.g., messaging interfaces, connectors, and related systems) must be logically and physically separated from non-Swift systems. The secure zone ensures that only authorized systems and users can interact with Swift components.
Step 2: Analyze the Diagram and Identify Components
The diagram includes the following components:
A. Middleware server (customer connector): Labeled as Component A, this server facilitates connectivity between the Swift user’s systems and the outsourcing agent’s infrastructure.
B. General-purpose PC Operator GUI: This is a general-purpose system used by an operator to interact with the Swift environment.
C. Swift-related OAA (Operational Application Architecture): Labeled as Component C, this represents the Swift messaging interface (e.g., Alliance Access/Entry) managed by the outsourcing agent.
D. Customer connector: This component, within the outsourcing agent’s environment, interfaces directly with the Swift connector or interface.
E. Dedicated PC Admin users: This represents administrative systems used to manage the Swift environment.Additionally, there’s aConnector or Interface(SB, L2BA, or Enabler) connecting to the Swift network.
Step 3: Determine Which Components Belong in a Secure Zone
A. Middleware server (customer connector):This component facilitates connectivity between the Swift user and the outsourcing agent’s Swift-related systems. According toControl 1.1: Swift Environment Protection, any system that directly interacts with the Swift messaging infrastructure (e.g., as a connector) must reside in a secure zone to prevent unauthorized access or tampering. Since this middleware server is part of the Swift data flow, it must be in a secure zone.Conclusion: Component A must be in a secure zone.
B. General-purpose PC Operator GUI:This is a general-purpose system used by operators, not a core Swift component. TheCSCF v2024underControl 1.2: Logical Access Controlrecommends that operator systems (e.g., GUIclients) should not reside in the same secure zone as critical Swift infrastructure to avoid introducing vulnerabilities from general-purpose systems. These systems typically connect to the secure zone via controlled interfaces (e.g., VPN or jump servers) but are not part of it.Conclusion: Component B does not need to be in a secure zone.
C. Swift-related OAA:This represents the Swift messaging interface (e.g., Alliance Access/Entry), which is a core component of the Swift environment.Control 1.1explicitly requires that messaging interfaces be placed in a secure zone to protect them from external threats and ensure segregation from non-Swift systems. Since this component is directly involved in Swift message processing, it must be in a secure zone.Conclusion: Component C must be in a secure zone.
D. Customer connector:This connector interfaces directly with the Swift connector or interface (SB, L2BA, or Enabler) to facilitate communication with the Swift network. As perControl 1.1, any component that directly connects to the Swift network or handles Swift traffic must be in a secure zone to ensure end-to-end security of the communication chain. This applies to the customer connector within the outsourcing agent’s environment.Conclusion: Component D must be in a secure zone.
E. Dedicated PC Admin users:Administrative systems used to manage the Swift environment are typically not placed in the same secure zone as the operational Swift components. According toControl 1.2: Logical Access Control, administrative access should be tightly controlled and segregated, often using jump servers or bastion hosts to access the secure zone. While these systems need secure access, they are not part of the secure zone itself.Conclusion: Component E does not need to be in a secure zone.
Step 4: Conclusion and Verification
Based on theCSCF v2024requirements, the components that must be placed in a secure zone are those directly involved in Swift message processing or connectivity to the Swift network. These are:
A. Middleware server (customer connector)
C. Swift-related OAA
D. Customer connectorComponent B (general-purpose PC) and Component E (admin PC) are not required to be in the secure zone, as they are operator or administrative systems that should be segregated from the Swift operational environment.
References
Swift Customer Security Controls Framework (CSCF) v2024, Control 1.1: Swift Environment Protection.
Swift Customer Security Programme – Security Best Practices, Section: Secure Zone Configuration.
CSCF v2024, Control 1.2: Logical Access Control.
The cluster of VPN boxes is also called managed-customer premises equipment (M-CPE).

TRUE
FALSE
The Answer Is:
BExplanation:
This question addresses the terminology related to VPN boxes in the Swift environment and their association with managed-customer premises equipment (M-CPE). Let’s verify this based on Swift CSP documentation.
Step 1: Understand VPN Boxes and M-CPE in Swift Context
In the Swift ecosystem, VPN boxes are typically part of the connectivity infrastructure used to establish secure tunnels (e.g., Network Transport Layer Security - NTLS) for communication with the Swift network. The term "managed-customer premises equipment (M-CPE)" generally refers to hardware or devices managed by a service provider or third party on the customer’s premises, often in telecommunications or IT contexts. TheSwift Customer Security Controls Framework (CSCF) v2024and related technical documentation provide insights into Swift’s infrastructure terminology.
Step 2: Analyze the Statement
The statement claims that the "cluster of VPN boxes is also called managed-customer premises equipment (M-CPE)." We need to determine if this is an official or recognized designation within the Swift CSP.
Step 3: Evaluate Against Swift CSP Guidelines
TheSwift Alliance Gateway Technical DocumentationandSwift Security Best Practicesdescribe VPN boxes (or similar connectivity devices) as part of the SwiftNet Link (SNL) infrastructure, often deployed at the user’s premises to secure communications. These devices are typically managed by the Swift user or a designated service provider, depending on the architecture (e.g., A2 or A4).
The term "M-CPE" is not specifically defined or used in Swift CSP documentation (e.g.,CSCF v2024,Swift User Handbook, orSwift Network Security Guidelines). Instead, Swift refers to such equipment as part of the "customer premises equipment (CPE)" when managed by the user, or as "managed services" when outsourced to a provider. However, "M-CPE" as a specific term for a cluster of VPN boxes is not corroborated.
In some IT contexts outside Swift, M-CPE might imply managed equipment, but Swift’s documentation does not adopt this terminology for VPN clusters, which are considered part of the broader connectivity infrastructure.
Step 4: Conclusion and Verification
The statement isFALSEbecause theCSCF v2024and related Swift documentation do not use "managed-customer premises equipment (M-CPE)" as a term for a cluster of VPN boxes. The correct terminology aligns with "customer premises equipment" or "managed connectivity devices," depending on the setup, but not specifically M-CPE.
References
Swift Customer Security Controls Framework (CSCF) v2024, Control 1.1: Swift Environment Protection.
Swift Alliance Gateway Technical Documentation, Section: Connectivity Infrastructure.
Swift Security Best Practices, Section: Network Security Devices.
In an entity having a small infrastructure and only 2 operators, the HR manager explains in a short interview how the security training is implemented providing one example. Would it be acceptable?

Yes. it's a risk based testing approach this can be enough in this case
No. more evidence are required
The Answer Is:
BExplanation:
This question assesses whether a short interview with the HR manager providing one example of security training implementation is acceptable for a small infrastructure with only two operators, under the Swift Customer Security Programme (CSP).
Step 1: Understand Security Training Requirements
TheSwift Customer Security Controls Framework (CSCF) v2024, underControl 5.1: Security Training and Awareness, mandates that all personnel with access to Swift-related systems (including operators) receive regular, documented security training. This includes awareness of security policies, procedures, and incident response. The control applies regardless of the size of the infrastructure.
Step 2: Analyze the Scenario
The entity has a small infrastructure with two operators, and the HR manager provides a short interview with one example of security training implementation.
TheIndependent Assessment Frameworkrequires assessors to validate the effectiveness of controls, including evidence of training completion, content, frequency, and attendance records. A risk-based approach allows flexibility, but minimum evidence standards must still be met.
Step 3: Evaluate Against CSCF Guidelines
Control 5.1specifies that training must be documented, with evidence such as training logs, attendance records, or certification. A single interview with one example does not provide sufficient evidence to demonstrate:
That all operators (both in this case) have been trained.
The frequency and comprehensiveness of the training program.
The effectiveness of the training (e.g., understanding and application).
TheSwift CSP FAQandSecurity Best Practicesnote that even for small entities, assessors must see multiple pieces of evidence (e.g., training schedules, materials, test results) to confirm compliance, especially during an independent assessment.
A risk-based testing approach (mentioned in option A) allows tailoring the depth of evidence based on risk, but it does not exempt small entities from providing more than a single anecdotal example. TheIndependent Assessment Frameworkrequires objective evidence, not just verbal assurances.
Step 4: Conclusion and Verification
The answer isB, as a short interview with one example is insufficient to meet the evidence requirements ofControl 5.1in theCSCF v2024. More evidence (e.g., training records, attendance logs, or test results) is required to validate compliance, even for a small infrastructure.
References
Swift Customer Security Controls Framework (CSCF) v2024, Control 5.1: Security Training and Awareness.
Swift Independent Assessment Framework, Section: Evidence Requirements.
Swift Security Best Practices, Section: Training Documentation.
Swift CSP FAQ, Section: Small Entity Compliance.
What are the conditions required to permit reliance on the compliance conclusion of a control assessed in the previous year? (Choose all that apply.)

The control compliance conclusion must have already been relied on the past two years
The previous assessment was performed on the (correct) CSCF version of the previous year
The control definition has not changed
The control-design and implementation are the same
The Answer Is:
B, C, DExplanation:
This question outlines conditions for relying on a previous year’s control assessment under theCSCF v2024.
Step 1: Understand Reliance on Previous Assessments
TheIndependent Assessment Frameworkallows reliance on prior assessments to reduce redundancy, provided specific conditions are met, as detailed in theCSCF v2024andSwift CSP Compliance Guidelines.
Step 2: Evaluate Each Option
A. The control compliance conclusion must have already been relied on the past two yearsThere is no requirement in theCSCF v2024orIndependent Assessment Frameworkthat reliance must have occurred for two prior years. Reliance is assessed annually based on current conditions.Conclusion: Incorrect.
B. The previous assessment was performed on the (correct) CSCF version of the previous yearThe assessment must align with the CSCF version active at the time, ensuring relevance. This is a condition in theIndependent Assessment Framework.Conclusion: Correct.
C. The control definition has not changedIf the control definition in theCSCF v2024has not been updated, prior conclusions remain valid, per theSwift CSP FAQ.Conclusion: Correct.
D. The control-design and implementation are the sameContinuity in design and implementation is required to ensure the control’s effectiveness has not changed, as specified in theIndependent Assessment Framework.Conclusion: Correct.
Step 3: Conclusion and Verification
The correct answers areB, C, and D, as these conditions ensure the prior assessment’s relevance and accuracy under theCSCF v2024.
References
Swift Customer Security Controls Framework (CSCF) v2024, Section: Assessment Reliance.
Swift Independent Assessment Framework, Section: Reliance Conditions.
Swift CSP FAQ, Section: Assessment Continuity.
Select the correct statement about Alliance Gateway.

It is used to exchange messages over the Swift network
It is used to create messages to send over the Swift network
The Answer Is:
AExplanation:
This question revisits the role of the Swift Alliance Gateway (SAG), similar to Question 6, but with different statements.
Step 1: Recap the Role of Alliance Gateway
The Swift Alliance Gateway (SAG) is a connectivity and security layer that facilitates interaction with the Swift network, as detailed in theSwift Alliance Gateway User Guideand referenced inControl 1.1: Swift Environment Protectionof theCSCF v2024.
Step 2: Evaluate Each Option
A. It is used to exchange messages over the Swift networkThe SAG acts as a gateway to concentrate and securely route SwiftNet traffic, enabling the exchange of messages over the Swift network. It handles connectivity, security (e.g., PKI), and message routing, as confirmed in theSwift Alliance Gateway Technical Documentation. This aligns with its role in the Swift ecosystem.Conclusion: This is correct.
B. It is used to create messages to send over the Swift networkAs noted in Question 6, the SAG does not create messages. Message creation is handled by applications like Alliance Access or Entry. The SAG’s role is to route and secure messages, not generate them, per theSwift Alliance Gateway User Guide.Conclusion: This is incorrect.
Step 3: Conclusion and Verification
The correct statement isA, as the Alliance Gateway’s primary function is to facilitate the secure exchange of messages over the Swift network, consistent with Swift CSP documentation.
References
Swift Alliance Gateway User Guide, Section: Functionality Overview.
Swift Customer Security Controls Framework (CSCF) v2024, Control 1.1: Swift Environment Protection.
Swift Alliance Gateway Technical Documentation, Section: Message Routing.
Which of the following statements best describe valid implementations when implementing control 2.9 Transaction Business Controls? (Choose all that apply.)

Multiple measures must be implemented by the Swift user to validate the flows of transactions are in the bounds of the normal expected business
A customer designed implementation or a combination of different measures are deemed valid if they sufficiently mitigate the control risks
Reliance on a recent business assessment or regulator response confirming the effectiveness of the control (as an example CPMI's_ requirement) is especially poignant to this control
Any solutions is acceptable so long as the CISO approves the implementation
The Answer Is:
A, BExplanation:
This question addresses valid implementations ofControl 2.9: Transaction Business Controlsunder theSwift Customer Security Controls Framework (CSCF) v2024, which focuses on detecting and preventing fraudulent transactions.
Step 1: Understand Control 2.9 Transaction Business Controls
Control 2.9 requires Swift users to implement measures to validate transaction flows against expected business patterns, aiming to detect anomalies that could indicate fraud or error. TheCSCF v2024emphasizes flexibility in implementation, provided the controls mitigate identified risks effectively.
Step 2: Evaluate Each Option
A. Multiple measures must be implemented by the Swift user to validate the flows of transactions are in the bounds of the normal expected businessTheCSCF v2024, underControl 2.9, mandates the use of multiple detection measures (e.g., transaction monitoring, threshold limits, anomaly detection) to ensure transaction flows align with normal business expectations. This multi-layered approach is essential to address diverse fraud risks.Conclusion: This is correct.
B. A customer designed implementation or a combination of different measures are deemed valid if they sufficiently mitigate the control risksTheCSCF v2024allows flexibility in how users implement Control 2.9, permitting custom solutions or combinations of measures (e.g., AI-based monitoring, manual reviews) as long as they effectively mitigate the risks identified in the user’s risk assessment. This is supported by theSwift CSP FAQon control customization.Conclusion: This is correct.
C. Reliance on a recent business assessment or regulator response confirming the effectiveness of the control (as an example CPMI's requirement) is especially poignant to this controlWhile a business assessment or regulator input (e.g., CPMI-IOSCO guidelines) can inform the implementation, Control 2.9 requires the user to implement specific measures, not just rely on external validations. TheCSCF v2024does not allow sole dependence on such assessments; users must demonstrate their own controls.Conclusion: This is incorrect.
D. Any solution is acceptable so long as the CISO approves the implementationTheCSCF v2024requires that implementations meet objective criteria for risk mitigation, not just internal approval by the Chief Information Security Officer (CISO). The independent assessment must validate effectiveness, not just rely on CISO endorsement.Conclusion: This is incorrect.
Step 3: Conclusion and Verification
The verified answers areAandB, as they align with the requirements and flexibility ofControl 2.9 Transaction Business Controlsin theCSCF v2024, ensuring robust and tailored transaction validation.
References
Swift Customer Security Controls Framework (CSCF) v2024, Control 2.9: Transaction Business Controls.
Swift CSP FAQ, Section: Control Implementation Flexibility.
Swift Security Best Practices, Section: Transaction Monitoring.
Select the correct statement(s).

The public and private keys of a Swift certificate are stored on the Hardware Security Module
The certificate stored on the Swift Hardware Security Module is used during the decryption operation of a message
The decryption operation uses the encryption private key of the receiver
To verify the signature the SwiftNetLink uses the signing private key of the receiver
The Answer Is:
A, BExplanation:
This question involves the role of the Hardware Security Module (HSM) and cryptographic operations in the Swift environment. Let’s evaluate each option.
Step 1: Understand HSM and Cryptographic Operations in Swift
The HSM is a secure device used to manage cryptographic keys and perform encryption/decryption operations, as detailed inControl 2.5B: Cryptographic Key Managementof theCSCF v2024. Swift uses public key infrastructure (PKI) for secure messaging, with HSMs storing keys and certificates.
Step 2: Evaluate Each Option
A. The public and private keys of a Swift certificate are stored on the Hardware Security ModuleIn the Swift environment, the HSM stores both the private key (for signing/decryption) and the public key (for verification/encryption) as part of the certificate pair. This is a standard practice for secure key management, as confirmed in theSwift Security Best PracticesandControl 2.5B, which mandates secure storage of cryptographic keys in HSMs.Conclusion: This statement is correct.
B. The certificate stored on the Swift Hardware Security Module is used during the decryption operation of a messageThe HSM uses the private key stored in the certificate to perform decryption of incoming Swift messages. This is part of the secure message handling process, as outlined inControl 2.5Band theSwift Alliance Gateway Technical Documentation.Conclusion: This statement is correct.
C. The decryption operation uses the encryption private key of the receiverDecryption uses theprivate keyof the receiver, not the “encryption private key” (a misnomer). The correct term is the receiver’s private key, which corresponds to the public key used for encryption. This error makes the statement technically incorrect, despite the intended meaning.Conclusion: This statement is incorrect.
D. To verify the signature the SwiftNetLink uses the signing private key of the receiverSignature verification requires the sender’s public key, not the receiver’s private key. The SwiftNetLink (SNL) uses the public key to verify the signature, as perControl 2.5BandSwift Security Best Practices. The private key is used for signing, not verification.Conclusion: This statement is incorrect.
Step 3: Conclusion and Verification
The verified statements areAandB, as they accurately describe the HSM’s role in key storage and decryption, consistent with Swift CSP documentation.
References
Swift Customer Security Controls Framework (CSCF) v2024, Control 2.5B: Cryptographic Key Management.
Swift Security Best Practices, Section: HSM Usage.
Swift Alliance Gateway Technical Documentation, Section: Cryptographic Operations.
The messaging operator in Alliance Lite2… (Select the two correct answers that apply)
•Connectivity
•Generic
•Products Cloud
•Products OnPrem
•Security
Can create and modify messages
Can assign RBAC roles to RMA operators and messaging operators
Can approve the Customer Security Officer change requests
Can approve messages
The Answer Is:
A, DExplanation:
Alliance Lite2 is a cloud-based solution for smaller institutions, providing a lightweight interface to the SWIFT network. The messaging operator in Alliance Lite2 is a role responsible for managing message-related activities, typically through the Alliance Lite2 Business Application (L2BA) interface. Let’s evaluate each option:
•Option A: Can create and modify messages
This is correct. The primary role of a messaging operator in Alliance Lite2 is to create and modify SWIFT messages, such as payment instructions (e.g., MT103) or other FIN messages. This is a core function of the L2BA interface, which provides a browser-based platform for operators to input, edit, and send messages. SWIFT documentation for Alliance Lite2 confirms that messaging operators have the necessary permissions to perform these tasks, aligning with the operational workflows supported by the platform.
•Option B: Can assign RBAC roles to RMA operators and messaging operators
This is incorrect. Role-Based Access Control (RBAC) role assignment in Alliance Lite2 is typically managed by a security officer or administrator role, not the messaging operator. The messaging operator’s scope is limited to message-related activities, not user or role management. In Alliance Lite2, RBAC is managed through the Alliance Web Platform, where a security officer (e.g., LSO) assigns roles to operators, including RMA (Relationship Management Application) operators and messaging operators. The CSCF Control "6.1 Security Awareness" emphasizes the separation of duties, ensuring that operational roles like messaging operators do not overlap with administrative roles.
•Option C: Can approve the Customer Security Officer change requests
This is incorrect. Approving Customer Security Officer (CSO) change requests is a high-level administrative task that falls under the purview of SWIFT’s security and compliance processes, often involving SWIFT’s support team or a designated administrator within the institution. In Alliance Lite2, this responsibility does not lie with the messaging operator, whose role is focused on message handling. The CSCF mandates strict controls for CSO changes, typically requiring multi-party approval outside the messaging operator’s scope.
•Option D: Can approve messages
This is correct. In Alliance Lite2, messaging operators can approve messages as part of the workflow, depending on the institution’s configuration. For example, a message created by one operator may require approval by another operator (or the same operator if configured with dual roles) before it is sent to the SWIFT network. This approval process ensures accuracy and compliance with internal controls, a feature supported by the L2BA interface in Alliance Lite2. SWIFT documentation highlights this capability as part of the messaging workflow.
Summary of Correct Answers:
The messaging operator in Alliance Lite2 can create and modify messages (A) and can approve messages (D), consistent with their operational role.
References to SWIFT Customer Security Programme Documents:
•SWIFT Customer Security Controls Framework (CSCF) v2024: Control 6.1 emphasizes role separation, limiting messaging operators to message-related tasks.
•SWIFT Alliance Lite2 Documentation: Details the messaging operator’s role in creating, modifying, and approving messages via L2BA.
•SWIFT Security Guidelines: Highlights administrative roles for RBAC and CSO changes, excluding messaging operators.
To verify the applicability of a CSCF control to a specific component, several actions may be considered. Which one does not apply in this case?
•Swift Customer Security Controls Policy
•Swift Customer Security Controls Framework v2025
•Independent Assessment Framework
•Independent Assessment Process for Assessors Guidelines
•Independent Assessment Framework - High-Level Test Plan Guidelines
•Outsourcing Agents - Security Requirements Baseline v2025
•CSP Architecture Type - Decision tree
•CSP_controls_matrix_and_high_test_plan_2025
•Assessment template for Mandatory controls
•Assessment template for Advisory controls
•CSCF Assessment Completion Letter
•Swift_CSP_Assessment_Report_Template
Check in the CSP Policy document
Check appendix F of the CSCF
Check carefully the Introduction section of the CSCF
Open a case with SWIFT support via the case manager on swift.com if further information or solution cannot be found in the documentation
The Answer Is:
AExplanation:
Verifying the applicability of a CSCF control to a specific component involves consulting relevant SWIFT documentation and processes. The "Swift Customer Security Controls Framework v2025" and associated guidelines provide the framework for this determination. Let’s evaluate each option:
•Option A: Check in the CSP Policy document
This does not apply. The "Swift Customer Security Controls Policy" is a high-level document outlining the CSP’s objectives and requirements but does not provide detailed guidance on control applicability to specific components. Control applicability is determined by the CSCF itself (e.g., through appendices or the control matrix), not the policy document, which is more strategic than operational.
•Option B: Check appendix F of the CSCF
This applies. Appendix F of the CSCF (or a similar appendix in the v2025 version) typically includes guidance on control applicability, mapping controls to different architecture types and components. This is a standard action for assessors, as noted in the "Independent Assessment Process for Assessors Guidelines."
•Option C: Check carefully the Introduction section of the CSCF
This applies. The Introduction section of the CSCF provides an overview of the framework’s scope, objectives, and how controls apply to various components, making it a relevant resource for verification.
•Option D: Open a case with SWIFT support via the case manager on swift.com if further information or solution cannot be found in the documentation
This applies. If documentation does not resolve the applicability question, SWIFT support via the case manager on swift.com is a recognized escalation path, as outlined in the "Independent Assessment Framework" and SWIFT operational guidelines.
Summary of Correct Answer:
Checking the CSP Policy document (A) does not apply, as it is not the appropriate resource for verifying control applicability to specific components.
References to SWIFT Customer Security Programme Documents:
•Swift Customer Security Controls Framework v2025: Provides applicability guidance in appendices (e.g., Appendix F) and the Introduction.
•Independent Assessment Process for Assessors Guidelines: Recommends using CSCF appendices and support channels.
•CSP_controls_matrix_and_high_test_plan_2025: Supports control applicability analysis.
========
The Swift HSM boxes:

Are located at the network partner premises and managed by Swift
Are located at the Swift user premises and managed by Swift
Are located at the Swift user premises and managed by the Swift user
Are located at the network partner premises and managed by Swift the network partner
The Answer Is:
CExplanation:
This question concerns the location and management of Swift HSM boxes, which are critical for secure key management.
Step 1: Understand the Role of Swift HSM
The Hardware Security Module (HSM) in the Swift environment is used to store and manage cryptographic keys, as perControl 2.5B: Cryptographic Key Managementof theCSCF v2024. The HSM ensures the security of Swift transactions by protecting private keys.
Step 2: Evaluate Each Option
A. Are located at the network partner premises and managed by SwiftNetwork partners (e.g., service providers) may host connectivity infrastructure, but HSMs are typically located at the user’s premises for direct control, as perSwift Security Best Practices. Swift does not manage user HSMs; users are responsible for their operation.Conclusion: This is incorrect.
B. Are located at the Swift user premises and managed by SwiftWhile HSMs are located at the user’s premises, Swift does not manage them. Users are responsible for HSM management, as outlined inControl 2.5B, which requires users to secure and maintain their HSMs.Conclusion: This is incorrect.
C. Are located at the Swift user premises and managed by the Swift userTheCSCF v2024andSwift HSM Deployment Guidespecify that HSMs are deployed at the Swift user’s premises to ensure local control and security. Users are responsible for managing and maintaining the HSM, including key generation and backups, as part of their compliance obligations.Conclusion: This is correct.
D. Are located at the network partner premises and managed by Swift the network partnerHSMs are not managed by network partners or Swift. Users retain control, and network partners only facilitate connectivity, not HSM management.Conclusion: This is incorrect.
Step 3: Conclusion and Verification
The verified answer isC, as it accurately reflects the standard deployment and management model for Swift HSMs, consistent with Swift CSP documentation.
References
Swift Customer Security Controls Framework (CSCF) v2024, Control 2.5B: Cryptographic Key Management.
Swift HSM Deployment Guide, Section: Installation and Management.
Swift Security Best Practices, Section: HSM Location and Control.

