In the context of CSP, what type of component is the Alliance Access? (Select the correct answer)
•Connectivity
•Generic
•Products Cloud
•Products OnPrem
•Security
A Messaging Interface
A Communication Interface
A SWIFT Connector
A Secure Server
The Answer Is:
AExplanation:
Alliance Access (SAA) is a SWIFT product used by financial institutions to manage the creation, processing, and transmission of SWIFT messages. In the context of the SWIFT Customer Security Programme (CSP), we need to classify its role within the SWIFT architecture:
•Option A: A Messaging Interface
This is correct. Alliance Access is classified as a messaging interface in SWIFT terminology. It allows users to create, validate, and send SWIFT messages (e.g., FIN MT messages like MT103 for payments) and receive incoming messages. It interfaces with the institution’s back-office systems and connects to the SWIFT network via a communication interface like Alliance Gateway (SAG). The CSCF categorizes components like Alliance Access as messaging interfaces, as they handle the business logic of message processing, and applies specific controls (e.g., "2.1 Internal Data Transmission Security") to secure these interfaces.
•Option B: A Communication Interface
This is incorrect. A communication interface in SWIFT terminology refers to components like Alliance Gateway (SAG), which manage the network-level connectivity to SWIFTNet via SwiftNet Link (SNL). Alliance Access does not handle network connectivity directly; it relies on SAG for this purpose. Alliance Access focuses on message creation and processing, not communication with the SWIFT network.
•Option C: A SWIFT Connector
This is incorrect. The term "SWIFT Connector" is not a standard classification in the CSP or SWIFT documentation. It might refer to integration tools like the SWIFT Integration Layer (SIL) used in cloud deployments, but Alliance Access does not fit this category. Alliance Access is a full-fledged messaging interface, not a connector.
•Option D: A Secure Server
This is incorrect. While Alliance Access operates on a server and must be secured as per CSCF controls (e.g., "2.3 System Hardening"), it is not classified as a "secure server." This term is too vague and does not reflect Alliance Access’s specific role as a messaging interface.
Summary of Correct Answer:
Alliance Access is a messaging interface (A), responsible for creating, processing, and managing SWIFT messages within the CSP framework.
References to SWIFT Customer Security Programme Documents:
•SWIFT Customer Security Controls Framework (CSCF) v2024: Classifies Alliance Access as a messaging interface (Control 2.1).
•SWIFT Alliance Access Documentation: Describes its role in message creation and processing.
•SWIFT Architecture Glossary: Distinguishes messaging interfaces (e.g., Alliance Access) from communication interfaces (e.g., Alliance Gateway).
========
Which encryption methods are used to secure the communications between the SNL host and HSM boxes?

NTLS and SSH
Telnet and SSL
NTLS and Telnet
MPLS and SSL
The Answer Is:
AExplanation:
This question focuses on the encryption methods securing communications between the SwiftNet Link (SNL) host and Hardware Security Module (HSM) boxes in the Swift environment.
Step 1: Understand SNL and HSM Communication
The SwiftNet Link (SNL) facilitates secure connectivity to the Swift network, while the HSM manages cryptographic keys. Secure communication between the SNL host and HSM is critical, as outlined inControl 2.5B: Cryptographic Key Managementof theCSCF v2024. These communications must use strong encryption protocols.
Step 2: Evaluate Each Option
A. NTLS and SSH
NTLS (Network Transport Layer Security): This is Swift’s proprietary protocol for securing communications over the SwiftNet network, including between SNL and HSM. It provides end-to-end encryption and is widely used in Swift infrastructure, as confirmed in theSwift Alliance Gateway Technical Documentation.
SSH (Secure Shell): SSH is used for secure management and administration of HSMs and SNL hosts, enabling encrypted remote access and configuration, as noted inSwift Security Best Practices.This combination aligns with Swift’s security requirements for protecting HSM communications.Conclusion: This is correct.
B. Telnet and SSL
Telnet: An unencrypted protocol, unsuitable for secure communications, and not used in Swift’s security framework perControl 2.6: Internet Accessibility Restriction.
SSL (Secure Sockets Layer): An older encryption protocol, largely replaced by TLS in modern systems. Swift does not specify SSL for SNL-HSM communications, favoring NTLS.Conclusion: This is incorrect.
C. NTLS and Telnet
NTLS: As above, this is valid for SwiftNet communications.
Telnet: As an unencrypted protocol, it is not acceptable for securing HSM communications, perControl 2.5B.Conclusion: This is incorrect.
D. MPLS and SSL
MPLS (Multiprotocol Label Switching): A networking technology for routing, not an encryption method, and not relevant to SNL-HSM security.
SSL: As above, not used in this context by Swift.Conclusion: This is incorrect.
Step 3: Conclusion and Verification
The correct answer isA, as NTLS secures the data communication and SSH provides secure management access between the SNL host and HSM, consistent withCSCF v2024and Swift technical documentation.
References
Swift Customer Security Controls Framework (CSCF) v2024, Control 2.5B: Cryptographic Key Management, Control 2.6: Internet Accessibility Restriction.
Swift Alliance Gateway Technical Documentation, Section: Network Security Protocols.
Swift Security Best Practices, Section: HSM and SNL Configuration.
In the illustration, identify the component type of each of the numbered components.

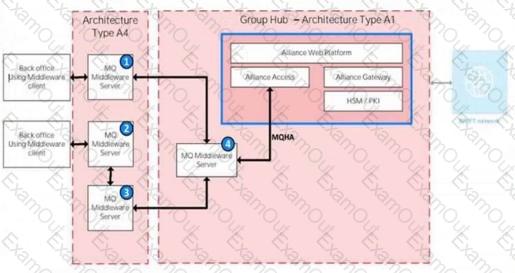
1. Customer Connector
2. Bridging Server (Middleware Server)
3. Customer Connector
4. Bridging Server (Middleware Server)
1. Customer Connector
2. Bridging Server (Middleware Server)
3. Customer Connector
4. Customer Connector
1. Bridging Server (Middleware Server)
2. Bridging Server (Middleware Server)
3. Bridging Server (Middleware Server)
4. Bridging Server (Middleware Server)
1. Customer Connector
2. Customer Connector
3. Customer Connector
4. Customer Connector
The Answer Is:
AExplanation:
This question requires identifying the component types of the numbered components (1, 2, 3, and 4) in the provided diagram, which illustrates a Swift infrastructure with Architecture Type A4 (user environment) and Architecture Type A1 (group hub). The classification is based on theSwift Customer Security Controls Framework (CSCF) v2024and related architecture definitions.
Step 1: Understand the Diagram and Component Types
The diagram shows two environments:
Architecture Type A4: The user’s local environment with back-office systems using middleware clients and servers.
Architecture Type A1: A group hub hosting Swift components like Alliance Access, Alliance Gateway, and HSM/PKI, connecting to the Swift network.
Component Types:
Customer Connector: A system or server that facilitates connectivity between the user’s environment and the Swift infrastructure (e.g., middleware servers interfacing with the group hub).
Bridging Server (Middleware Server): A server that bridges data flows between back-office systems and the Swift messaging environment, often handling message queuing or transformation.
Step 2: Analyze Each Numbered Component
Component 1 (Middleware Server connected to Back Office 1):This server is part of the A4 architecture, interfacing the back-office middleware client with the group hub (A1). It acts as a connector, facilitating data exchange to the MQHA (Message Queue High Availability) server in the group hub. Per theCSCF v2024andSwift Architecture Types Explained, this is aCustomer Connector.
Component 2 (MQHA Middleware Server in the Group Hub):This server is within the A1 group hub, bridging the user’s data (via the customer connector) tothe Alliance Access and Gateway. It handles message queuing and acts as aBridging Server (Middleware Server), as defined in theSwift Alliance Gateway Technical Documentation.
Component 3 (Middleware Server connected to Back Office 2):Similar to Component 1, this server connects the second back-office middleware client to the MQHA server in the group hub, functioning as aCustomer Connector.
Component 4 (MQ Middleware Server connected to MQHA):This server within the A1 group hub supports the MQHA, bridging data flows to the Swift messaging components (Alliance Access/Gateway). It is aBridging Server (Middleware Server), consistent with theCSCF v2024definitions.
Step 3: Match with Options
A. 1. Customer Connector, 2. Bridging Server (Middleware Server), 3. Customer Connector, 4. Bridging Server (Middleware Server): Matches the analysis above.
B. 1. Customer Connector, 2. Bridging Server (Middleware Server), 3. Customer Connector, 4. Customer Connector: Incorrect, as Component 4 is a bridging server, not a customer connector.
C. 1. Bridging Server (Middleware Server), 2. Bridging Server (Middleware Server), 3. Bridging Server (Middleware Server), 4. Bridging Server (Middleware Server): Incorrect, as Components 1 and 3 are customer connectors, not bridging servers.
D. 1. Customer Connector, 2. Customer Connector, 3. Customer Connector, 4. Customer Connector: Incorrect, as Components 2 and 4 are bridging servers.
Step 4: Conclusion and Verification
The correct answer isA, as it accurately identifies the component types based on their roles in the A4 and A1 architectures, consistent withCSCF v2024andSwift Architecture Types Explained.
References
Swift Customer Security Controls Framework (CSCF) v2024, Control 1.1: Swift Environment Protection.
Swift Architecture Types Explained, Section: Component Roles.
Swift Alliance Gateway Technical Documentation, Section: Middleware and Connectors.
The Internal Audit and an external assessment company are both involved in a SWIFT user’s assessment. Both have shared control assessments to cover the full scope (meaning two separate assessment teams). Who needs to provide a completion letter? (Select the correct answer)
•Swift Customer Security Controls Policy
•Swift Customer Security Controls Framework v2025
•Independent Assessment Framework
•Independent Assessment Process for Assessors Guidelines
•Independent Assessment Framework - High-Level Test Plan Guidelines
•Outsourcing Agents - Security Requirements Baseline v2025
•CSP Architecture Type - Decision tree
•CSP_controls_matrix_and_high_test_plan_2025
•Assessment template for Mandatory controls
•Assessment template for Advisory controls
•CSCF Assessment Completion Letter
•Swift_CSP_Assessment_Report_Template
The Internal audit lead assessor and the external company lead assessor
The Internal audit lead assessor only
The External company lead assessor only
None of them, it is not required when an internal department was involved in the assessment
The Answer Is:
CExplanation:
The "Independent Assessment Framework" and "Independent Assessment Process for Assessors Guidelines" require that the CSP assessment be conducted by an independent, certified assessor, with the resulting "CSCF Assessment Completion Letter" being a key deliverable. Let’s evaluate each option:
•Option A: The Internal audit lead assessor and the external company lead assessor
This is incorrect. The CSP prohibits reliance on internal audits for the completion letter due to the independence requirement. Only the external assessor’s letter is valid, as per the "Independent Assessment Framework."
•Option B: The Internal audit lead assessor only
This is incorrect. Internal audits lack the independence needed to issue the completion letter, which must come from an external assessor.
•Option C: The External company lead assessor only
This is correct. The "Independent Assessment Process for Assessors Guidelines" mandates that the completion letter be provided by the lead assessor from the external assessment company, as they are the independent entity conducting the assessment. The internal audit’s involvement is supplementary and cannot replace the external assessor’s responsibility.
•Option D: None of them, it is not required when an internal department was involved in the assessment
This is incorrect. A completion letter is always required, and internal involvement does not waive this requirement; it must be issued by the external assessor.
Summary of Correct Answer:
Only the external company lead assessor needs to provide the completion letter (C).
References to SWIFT Customer Security Programme Documents:
•Independent Assessment Framework: Requires an independent assessor’s completion letter.
•Independent Assessment Process for Assessors Guidelines: Specifies external assessor responsibility.
•CSCF Assessment Completion Letter: Issued by the external assessor.
========
Penetration testing must be performed at application level against the Swift-related components, such as the interfaces, Swift and customer connectors?

True, those are key components
False, only the components as defined in Swift Testing Policy
The Answer Is:
BExplanation:
This question addresses the scope of penetration testing for Swift-related components under theSwift Customer Security Programme (CSP).
Step 1: Understand Penetration Testing Requirements
TheCSCF v2024, underControl 4.1: Penetration Testing, mandates penetration testing to identify vulnerabilities in Swift-related systems. The scope is defined by theSwift Testing Policy, not arbitrarily applied to all components.
Step 2: Analyze the Statement
The statement suggests that penetration testing "must be performed at application level against the Swift-related components, such as the interfaces, Swift and customer connectors." We need to verify if this is a mandatory scope.
Step 3: Evaluate Against Swift Guidelines
Control 4.1: Penetration Testingrequires testing of in-scope components, but theSwift Testing Policy(referenced in theCSCF v2024andSecurity Best Practices) specifies which components (e.g., messaging interfaces, connectors) must be tested based on risk and architecture.
The policy does not mandate testing all listed components (e.g., interfaces, connectors) at the application level unless they are identified as high-risk or in-scope per the user’s assessment. For example, customer connectors might be excluded if managed by a Service Bureau, per theSwift Outsourcing Guidelines.
The statement’s assertion of a broad mandate is incorrect; the scope is limited to components defined in theSwift Testing Policy, which provides a tailored approach.
Step 4: Conclusion and Verification
The answer isB, as penetration testing must follow theSwift Testing Policy, which defines the specific components to test, rather than mandating all Swift-related components like interfaces and connectors.
References
Swift Customer Security Controls Framework (CSCF) v2024, Control 4.1: Penetration Testing.
Swift Testing Policy, Section: Scope Definition.
Swift Security Best Practices, Section: Penetration Testing.
The SwiftNet Link (SNL) software is always required for the Swift Alliance Gateway to operate.
SIL Connectivity
•Generic
•Products Cloud
•Products OnPrem
•Security
TRUE
FALSE
The Answer Is:
AExplanation:
SwiftNet Link (SNL) is a critical component of the SWIFT infrastructure, serving as the mandatory network interface for accessing SWIFTNet services. The Swift Alliance Gateway (SAG) is a communication interface that consolidates message flows from various applications and connects them to the SWIFT network. According to SWIFT documentation, SAG is a modular software package installed on top of SNL, meaning SNL is a foundational requirement for SAG to operate.
SNL provides essential functionalities such as transport, formatting, security, and service management, enabling secure and interoperable communication over the SWIFT Secure IP Network (SIPN). SAG uses SNL to establish this connectivity, as it does not have direct network access capabilities on its own. For example, SAG relies on SNL to handle SWIFT message types like FIN, InterAct, and FileAct, ensuring secure communication with the SWIFT network. This dependency is evident in architectures where SAG is deployed, such as in the Alliance Connect Virtual solutions, where SNL is always included alongside SAG to facilitate connectivity.
The mention of "SIL Connectivity" in the question refers to the SWIFT Integration Layer (SIL), which is often part of cloud-based deployments like Alliance Cloud. However, even in such setups, SNL remains a requirement for SAG to function, as SIL itself interacts with SAG/SNL to manage message flows. The categories "Generic," "Products Cloud," "Products OnPrem," and "Security" likely refer to the context of SWIFT services, but they do not alter the fundamental requirement of SNL for SAG operation.
There are no exceptions in SWIFT’s official documentation where SAG can operate without SNL. Even in cloud-based solutions like Alliance Cloud or Alliance Lite2, SNL is either embedded or provided as part of the connectivity stack. For instance, in Alliance Connect Virtual deployments, SAG and SNL are deployed together to ensure connectivity to SWIFTNet. Therefore, the statement is unequivocally true.
References to SWIFT Customer Security Programme Documents:
•SWIFT Customer Security Controls Framework (CSCF) v2024: The CSCF mandates secure connectivity components like SNL within the SWIFT secure zone (Control 1.1 SWIFT Environment Protection).
•SWIFT Alliance Gateway Documentation: SAG is described as requiring SNL for connectivity to SWIFTNet, as it acts as an interface on top of SNL.
•SWIFTNet Link Documentation: SNL is the mandatory network interface for all external SWIFTNet communications, including those facilitated by SAG.
What is expected regarding Token Management when (physical or software-based) tokens are used? (Choose all that apply.)

Similar to user accounts, individual assignment and ownership for accurate traceability and revocation in case of potential tampering, loss or in case of user role change
Have in place a strict token assignment process. This avoids the need to perform g a regular review of assigned tokens
Individuals must not share their tokens. Tokens must remain under the control and supervision of its owner
All tokens must be stored in a safe when not used
The Answer Is:
A, CExplanation:
This question relates to Control 5.2 – Token Management in the CSCF, which outlines requirements for managing physical or software-based tokens used for authentication or cryptographic operations in the SWIFT environment. Let’s evaluate each option:
A. Similar to user accounts, individual assignment and ownership for accurate traceability and revocation in case of potential tampering, loss or in case of user role change
CSCF Control 5.2 mandates that tokens (e.g., HSM tokens or software tokens) be uniquely assigned to individuals to ensure traceability and accountability. This allows for revocation in cases of tampering, loss, or role changes, mirroring user account management principles under Control 5.1 – Logical Access Control.
In a fully on-premises infrastructure, which security management profile is not involved? (Select the one correct answer)
•Connectivity
•Generic
•Products Cloud
•Products OnPrem
•Security
Alliance Security Officer (LSO/RSO)
HSM Administrator
swift.com Administrator
Customer Security Officer
The Answer Is:
CExplanation:
In a fully on-premises infrastructure, all SWIFT-related components (e.g., Alliance Gateway, SwiftNet Link, HSM) are hosted and managed locally by the customer. This setup contrasts with cloud-based deployments (e.g., Alliance Cloud), where some management is outsourced to SWIFT or third-party providers. The security management profiles refer to roles responsible for overseeing the security of the SWIFT environment. Let’s evaluate each option:
•Option A: Alliance Security Officer (LSO/RSO)
This is involved. The Local Security Officer (LSO) and Remote Security Officer (RSO) are roles defined by SWIFT for managing security settings within the Alliance suite (e.g., Alliance Gateway, Alliance Access). In an on-premises setup, the LSO/RSO is typically an internal staff member who configures security parameters, manages user access, and ensures compliance with CSCF controls like "6.1 Security Awareness." These roles are mandatory for on-premises deployments.
•Option B: HSM Administrator
This is involved. The HSM Administrator is responsible for managing the Hardware Security Module, which stores PKI certificates and performs cryptographic operations. In an on-premises environment, the customer maintains the HSM locally, and the HSM Administrator oversees its configuration and security, aligning with CSCF Control "1.3 Cryptographic Failover." This role is essential for on-premises security management.
•Option C: swift.com Administrator
This is not involved. The "swift.com Administrator" is not a standard SWIFT-defined role. It appears to be a misnomer or typo, possibly intended to refer to a SWIFT-hosted service administrator (e.g., someone managing swift.com-related cloud services). In a fully on-premises infrastructure, there is no reliance on SWIFT-hosted services or cloud management, as all components are locally controlled. SWIFT’s cloud offerings (e.g., Alliance Cloud) involve administrators managing SWIFT-hosted infrastructure, but this is irrelevant in an on-premises context. The CSCF does not reference a "swift.com Administrator" role for on-premises setups.
•Option D: Customer Security Officer
This is involved. The Customer Security Officer is a role mandated by the SWIFT CSP, responsible for overseeing the institution’s compliance with the CSCF. In an on-premises environment, this officer ensures that local security controls (e.g., physical security under Control "1.2") are implemented and audited, making this role essential.
Summary of Correct Answer:
In a fully on-premises infrastructure, the "swift.com Administrator" (Option C) is not involved, as it does not apply to locally managed environments and is likely a reference to a cloud-based role.
References to SWIFT Customer Security Programme Documents:
•SWIFT Customer Security Controls Framework (CSCF) v2024: Defines roles like LSO/RSO, HSM Administrator, and Customer Security Officer for on-premises security (Controls 1.1, 1.3, 6.1).
•SWIFT Alliance Documentation: Describes the LSO/RSO and HSM Administrator roles in on-premises deployments.
•SWIFT CSP Compliance Guidelines: Mandates the Customer Security Officer role for all SWIFT users, including on-premises setups.
========
Additional Notes
•Typing Corrections: Corrected "ijp" to "P" for consistency in category labels. Adjusted "c" to "C" and "0" to "D" in question options for proper formatting.
•Context of Categories: The categories ("Connectivity," "Generic," "Products Cloud," "Products OnPrem," "Security") likely indicate the scope of the certification test, with "Products OnPrem" being relevant to Questions 4 and 5.
•SWIFT CSP Alignment: Answers align with the CSP’s focus on security roles and infrastructure types, as documented in the CSCF and SWIFT operational guides.
As a Swift CSP Certified Assessor. Swift contacted me to provide evidence on an assessment I have performed. This is required to support their quality assurance validation process. Is it allowed?

Yes, one of the obligations of the certification programme is that quality assessment can be performed by Swift
No, it's confidential
The Answer Is:
AExplanation:
This question addresses the obligations of a Swift CSP Certified Assessor regarding the provision of evidence to Swift for quality assurance purposes.
Step 1: Understand the Role of a Swift CSP Certified Assessor
A Swift CSP Certified Assessor is an independent professional or entity authorized to conduct CSP assessments under theIndependent Assessment Framework. The certification program, managed by Swift, includes specific obligations to ensure the integrity and quality of assessments.
Step 2: Analyze the Request for Evidence
Swift has contacted the assessor to provide evidence from an assessment to support their quality assurance validation process. This request implies a review of the assessor’s work to ensure compliance with CSP standards.
TheSwift CSP Assessor Certification Program Guidelinesstate that certified assessors are obligated to cooperate with Swift’s quality assurance processes. This includes providingevidence (e.g., assessment reports, workpapers) upon request to verify the accuracy and adherence to methodology, as part of Swift’s oversight.
Confidentiality is a concern, but theCSCF v2024andAssessor Certification Programclarify that assessors must share evidence with Swift under a non-disclosure agreement (NDA) or similar confidentiality framework, ensuring data protection while allowing validation.
Step 3: Evaluate Each Option
A. Yes, one of the obligations of the certification programme is that quality assessment can be performed by SwiftTheSwift CSP Assessor Certification Program Guidelinesexplicitly outline that Swift may conduct quality assessments, and assessors must provide evidence to support this process. This is a contractual obligation of certification, aligning with Swift’s responsibility to maintain CSP integrity.Conclusion: This is correct.
B. No, it's confidentialWhile confidentiality is critical (protected underControl 2.3: System Access Controland Swift’s privacy policies), the certification program requires assessors to share evidence with Swift for quality assurance, subject to confidentiality agreements. Refusing to provide evidence would breach the assessor’s obligations.Conclusion: This is incorrect.
Step 4: Conclusion and Verification
The answer isA, as theSwift CSP Assessor Certification Programmandates that certified assessors must support Swift’s quality assurance validation by providing evidence, balancing confidentiality with compliance oversight.
References
Swift Customer Security Controls Framework (CSCF) v2024, Control 2.3: System Access Control.
Swift CSP Assessor Certification Program Guidelines, Section: Obligations and Quality Assurance.
Swift Independent Assessment Framework, Section: Assessor Responsibilities.
The SWIFT VPN boxes are located between the Messaging and Communication interface.
•Connectivity
•Generic
•Products Cloud
•Products OnPrem
•Security
TRUE
FALSE
The Answer Is:
BExplanation:
In the SWIFT architecture, VPN boxes (e.g., Alliance Connect boxes or virtual VPN appliances) are network devices that establish a secure connection to the SWIFT Secure IP Network (SIPN) using Virtual Private Network (VPN) technology. Let’s evaluate the statement:
•The "Messaging Interface" refers to components like Alliance Access (SAA), which create, process, and manage SWIFT messages (e.g., MT103). The "Communication Interface" refers to components like Alliance Gateway (SAG), which consolidate message flows and connect to the SWIFT network via SwiftNet Link (SNL).
•The SWIFT VPN boxes are located at the network boundary, connecting the customer’s internal SWIFT environment (including both messaging and communication interfaces) to the external SIPN. They are not positioned between the messaging interface and the communication interface; instead, they sit outside the SWIFT secure zone, linking the entire local infrastructure to SWIFTNet.
•In a typical deployment, the architecture flows as follows: Messaging Interface (e.g., Alliance Access) → Communication Interface (e.g., Alliance Gateway with SNL) → VPN Boxes → SWIFTNet. The VPN boxes are part of the external connectivity layer, not an intermediary between internal components. This is supported by CSCF Control "1.1 SWIFT Environment Protection," which defines the secure zone as including messaging and communication interfaces, with VPN boxes providing the external link.
•The statement’s implication that VPN boxes separate the messaging and communication interfaces is incorrect, as they are part of the broader connectivity infrastructure.
Summary of Correct Answer:
The SWIFT VPN boxes are not located between the Messaging and Communication interface; they connect the entire local SWIFT environment to the SIPN, making the statement false.
References to SWIFT Customer Security Programme Documents:
•SWIFT Customer Security Controls Framework (CSCF) v2024: Control 1.1 defines the secure zone and external connectivity via VPN boxes.
•SWIFT Alliance Gateway Documentation: Describes the placement of VPN boxes outside the communication interface.
•SWIFT Network Architecture Guide: Confirms VPN boxes as the external connection point to SIPN.

