Which data model populated the panels on the Risk Analysis dashboard?
Which of the following is part of tuning correlation searches for a new ES installation?
What is the first step when preparing to install ES?
Both “Recommended Actions” and “Adaptive Response Actions” use adaptive response. How do they differ?
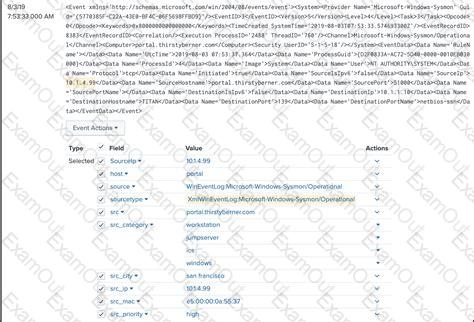
Which columns in the Assets lookup are used to identify an asset in an event?
How does ES know local customer domain names so it can detect internal vs. external emails?
Which tool Is used to update indexers In E5?
What is the main purpose of the Dashboard Requirements Matrix document?
Following the installation of ES, an admin configured users with the ess_user role the ability to close notable events.
How would the admin restrict these users from being able to change the status of Resolved notable events to Closed?

 Asset & Identity for Splunk Enterprise Security - Part 1 ...
Asset & Identity for Splunk Enterprise Security - Part 1 ... Detecting Typosquatting, Phishing, and Corporate Espionage ... - Splunk
Detecting Typosquatting, Phishing, and Corporate Espionage ... - Splunk