What information is identified during the input phase of the ingestion process?
For the following data, what would be the correct attribute/value oair to use to successfully extract the correct timestamp from all the events?
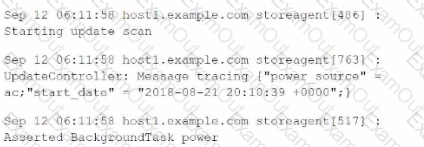
What Splunk command will allow an administrator to view the runtime configuration instructions for a monitored file in Inputs. cont on the forwarders?
What is the recommended method to test the onboarding of a new data source before putting it in production?
Which of the following is true when using Intermediate Forwarders?
Li was asked to create a Splunk configuration to monitor syslog files stored on Linux servers at their organization. This configuration will be pushed out to multiple systems via a Splunk app using the on-prem deployment server.
The system administrators have provided Li with a directory listing for the logging locations on three syslog hosts, which are representative of the file structure for all systems collecting this data. An example from each system is shown below:
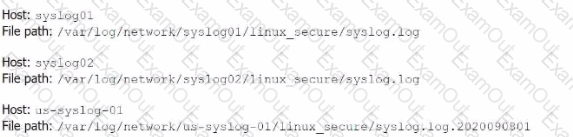
A)
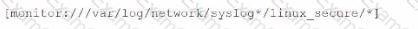
B)
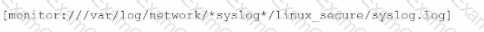
C)
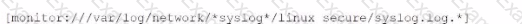
D)
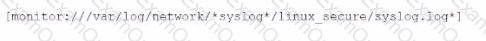
Consider the following configurations:
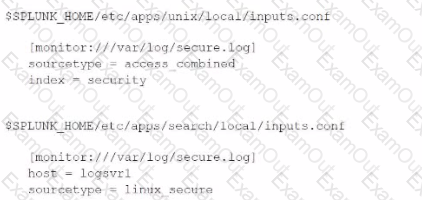
What is the value of the sourcetype property for this stanza based on Splunk's configuration file precedence?
Which of the following tasks is the responsibility of a Splunk Cloud administrator?
Which of the following files is used for both search-time and index-time configuration?
Which of the following tasks is not managed by the Splunk Cloud administrator?

