A system administrator is creating a user directory connector (UDC) for an Active Directory using SSL Which path should the administrator use to configure the UDC?
A security audit revealed problems with the newly installed multi-node environment The environment was deployed using the default settings for the central and nm nodes All possible services have been added to the rim node
The audit was based on the current IT security policy which states:
* All traffic between servers should be encrypted
* 2 56-bit encryption is required
* Traffic between client and server should be encrypted and trusted
* iOS devices must De supported
* Password length must be at least eight characters and include at least one number and one specie! character
What should the system administrator deploy to meet these requirements?
A system administrator must set up security that does NOT allow certain users to create objects in published apps. The users that should NOT be able to create objects are in an AD group called LimitedUsers.
Which security rule should the administrator use to meet this requirement?
A system administrator has a Qlik Sense environment with a central node and a scheduler node. One of the apps loads data from text files which are located in the FinanceData folder on the D drive on the central node
The system administrator creates a folder data connection and sets Name = Finance Data and Path = D :\FinanceData
When the reload task runs for lint firs! lime, it tails
What is the cause of the error?
A user needs to update a published app in the Finance stream. After the changes have been made, the needs to be moved to the Accounting stream. The user only has access to a laptop running windows 7(32-bit). The owner of all published apps is the sa_repository user.
Which steps should a system administrator take to efficiently complete this task?
A system administrator needs to set up a solution for mobile device users to access the Qlik Sense hub. The solution must meet several requirements.
* Support IOS devices
* Can be used in remote locations where users do NOT have laptop or desktop computers
* Ability to access Qlik Sense outside the office network without a compatible tunnel solution
* Ability to access Qlik Sense using a secure gateway
What should the system administrator do to meet these requirements?
Refer to the exhibit.
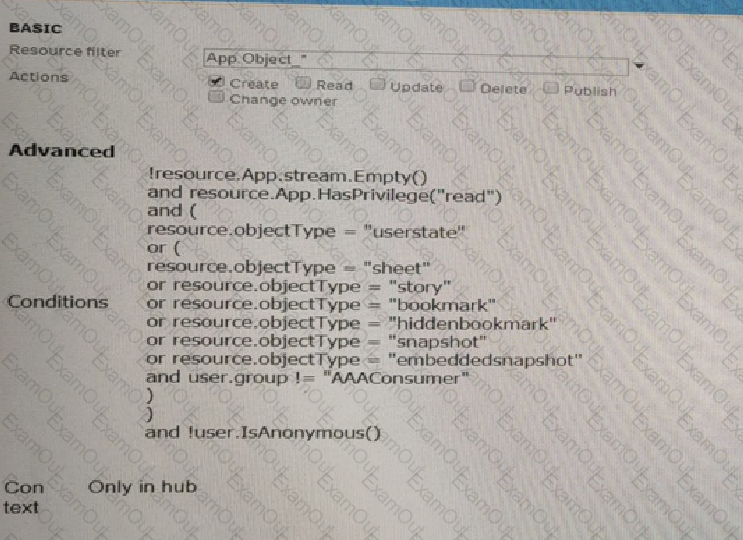
A system administrator creates the security rule shown No other custom security rules exist
What effect will the security rule have when applied to a user?
A Qlik Sense environment uses-based license types. A user, who can typically create new apps in personal Work, can no longer create new apps. The Personal Work area is NOT displayed for this user.
How should the system administrator resolve this issue?
A system administrator adds RIM B to a two node environment using the central node as the proxy. The system administrator is using the default virtual proxy for the central node to access the hub.
The system administrator sets up a load balancing rule to have all apps served on both RIM A and RIM B. the system administrator performs the following steps.
1. Disable the default load balancing rule, ResourcesOnNonCentralNodes’’
2. Create a new rule with the Resource filter ‘’App_*’’ and checks Load balancing
3. Sets the condition to ((node.name=RIM A’’ or node name=RIM B’’))
The rule is successfully verified. The system administrator has users log in to the hub and open apps to verify that they are opening on RIM B. However, after multiple users open the app, there still NO report of activity of activity on RIM B.
What is causing this issue?
Refer to the exhibit.
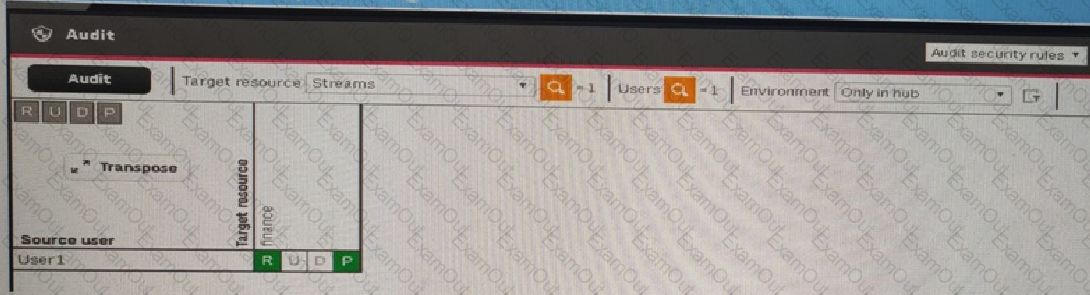
A system administrator creates this security rule to keep User1 out of the finance stream.
((user.name1 =User1''))
After conducting an audit on the finance stream, the system administrator notices that the security rule does NOT function as expected.
What is censing this issue?

