You want to allow users to use an application on a mobile device, even if the device is not connected to a network.
Which configuration option supports this requirement?
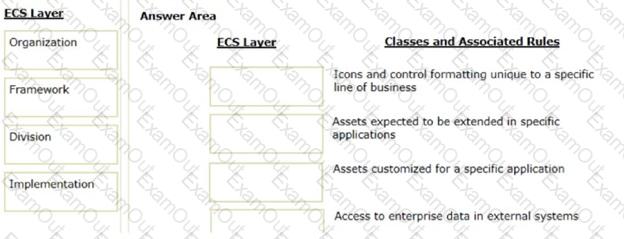
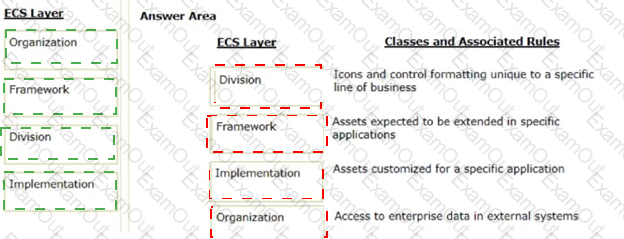
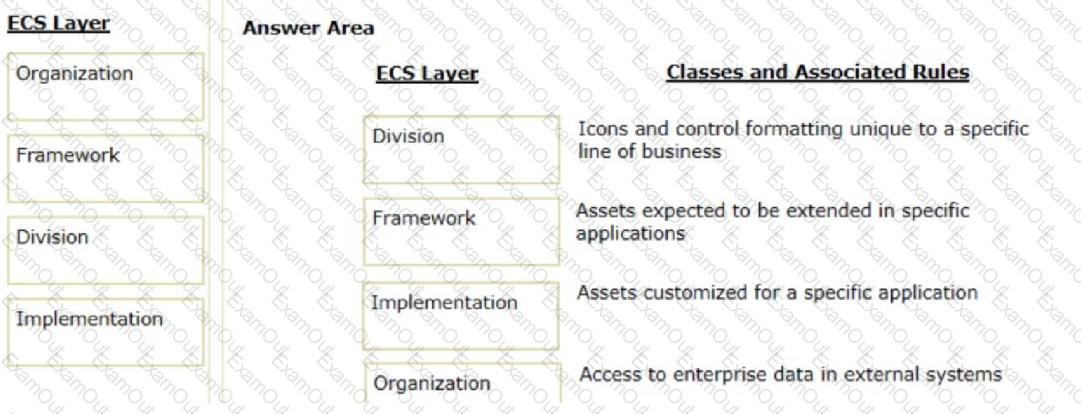
Organize the classes and associated rules in the appropriate Enterprise Class Structure (ECS) layer.
Which two configurations do you implement when using a Pega Web Mashup? (Choose Two)
An application contains a flow action with an Apply to: class of TRB-HRApps-Work-Feedback in a locked ruleset. When updating the application, you save the existing flow action into a new minor version of the ruleset this time applied to TRB'HRApps-Work so it can be used by more than one case type.
How do you prevent the application from using the rule in TRB-HRApps-Work-Feedback?
Which three mobile device features can you leverage by using Pega Mobile Client? (Choose Three)
How do you ensure that only a manager can run a specific flow action?
You are updating a system of record using a SOAP connector. If the system of record is unavailable, you want to retry after an hour. If it is still unavailable after an hour, a notification should be sent to a system administrator.
How do you implement this requirement?
As a best practice, in which situation do you use a keyed data page?
A view has a part number field that requires the first two characters are letters, and the last four are digits (for example, AB1234).
How do you ensure that the correct pattern is entered when the user exits the field?
Which three options do you consider when deciding to use post-processing actions on a flow action? (Choose Three)

 Graphical user interface, application
Description automatically generated
Graphical user interface, application
Description automatically generated