you are configuring authentication for a pega web mashup implementation.
how do you ensure the host system origin is trusted?
An application include two case types: expense report and purchase requests which two steps are required to enable support for both case type for offline user on a mobile device ?
An application allows users to manage Account cases. You need to configure security so that users are allowed to view and update account only if they are the primary or secondary owner
how do you implement this requirement?
when a customer submits a credit card dispute, the application connects to an external service to retrieve all transaction made by the customer. the external service returns transactions ordered by date of transaction, in a descending, chronological order when a case worker reviews the dispute the application displays the 10 most recent transactions.
if the case worker does not see the disputed transaction in the list, the case worker can search for additional transaction the caseworker can filter search results on transaction date the transaction amount or the merchant name the search results display the 10 most recent transactions that satisfy the filter criteria. the case worker cannot paginate through the results.
how do you configure the response data transform to satisfy all of the requirements in the scenario?
A case can be withdrawn using a local action. You want to restrict the ability to withdraw a
case to the user who created the case or any work group manager of the user. Select three
rule types used in combination to achieve this functionality. (choose three)
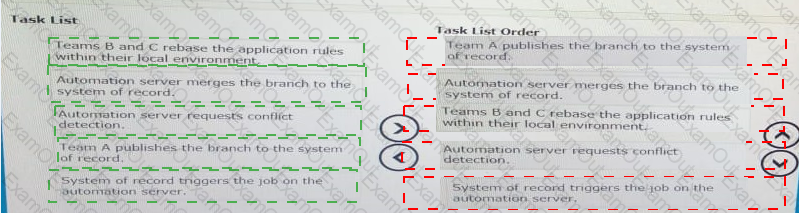
You are managing distributed, geographically dispersed, development teams A, B and C. Team A is ready to merge changes into their development environment to make available changes to Team B’s Team C’s.
To ensure all development teams are working with the latest version of shared rule base, select and move all of the following tasks to the tasks List Order column and place them in the correct order.

You oversee a medium-size development team. Some of the team members and new to Pega and are working on features in a separate branch.
What are two ways you can ensure that the rules the team creates adhere to best practices? (Choose Two)
You imported a rule-admin-product (RAP) file that contains new features into a user acceptance testing(UAT) environment. Select the option that ensures basic functionality behaves as expected before inviting users to start acceptance testing.
You manage a 30-person development team with members located across the globe.
Which Pega Cloud environment best supports the needs of your team?
Identify the two correct statements regarding Localization wizard capabilities. (Choose Two)