For a critical incident, Cortex XSIAM suggests several playbooks which should have been executed automatically.
Why were the playbooks not executed?
An analyst is responding to a critical incident involving a potential ransomware attack. The analyst immediately initiates full isolation on the compromised endpoint using Cortex XSIAM to prevent the malware from spreading across the network. However, the analyst now needs to collect additional forensic evidence from the isolated machine, including memory dumps and disk images without reconnecting it to the network. Which action will allow the analyst to collect the required forensic evidence while ensuring the endpoint remains fully isolated?
Which attribution evidence will have the lowest confidence level when evaluating assets to determine if they belong to an organization’s attack surface?
In which two locations can mapping be configured for indicators? (Choose two.)
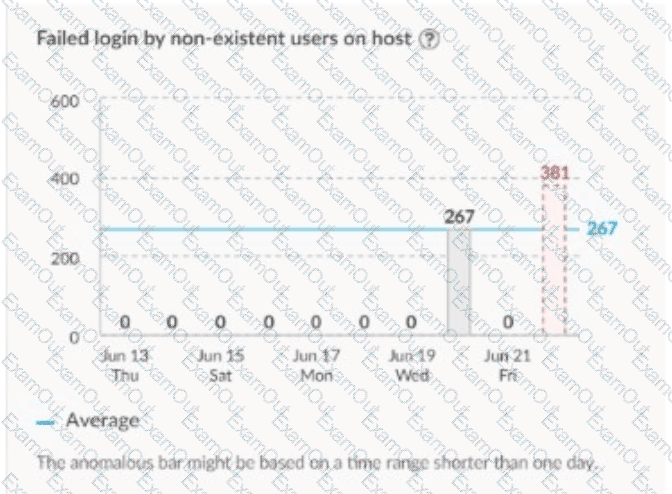
Which type of analytics will trigger the alert on the image shown?
A Cortex XSIAM analyst in a SOC is reviewing an incident involving a workstation showing signs of a potential breach. The incident includes an alert from Cortex XDR Analytics Alert source "Remote service command execution from an uncommon source." As part of the incident handling process, the analyst must apply response actions to contain the threat effectively.
Which initial Cortex XDR agent response action should be taken to reduce attacker mobility on the network?
Which pane in the User Risk View will identify the country from which a user regularly logs in, based on the past few weeks of data?
Why would an analyst schedule an XQL query?
While investigating an incident on the Incident Overview page, an analyst notices that the playbook encountered an error. Upon playbook work plan review, it is determined that the error was caused by a timeout. However, the analyst does not have the necessary permissions to fix or create a new playbook.
Given the critical nature of the incident, what can the analyst do to ensure the playbook continues executing the remaining steps?
In addition to defining the Rule Name and Severity Level, which step or set of steps accurately reflects how an analyst should configure an indicator prevention rule before reviewing and saving it?

