What are three requirements to automate service deployment of a VM-Series firewall from an NSX Manager? (Choose three.)
In which two ways can micro-segmentation save money for the enterprise? (Choose two.)
Which two options describe use cases of internal and external tags in Panorama? (Choose two.)
In a VMware deployment, in order for the customer to get maximum performance out of a VM-700 firewall in PAN-OS 8 x how many virtual CPU cores can be used?
Which are two use cases for HSCI ports on the SMC module on PA-7000 Series? (Choose two )
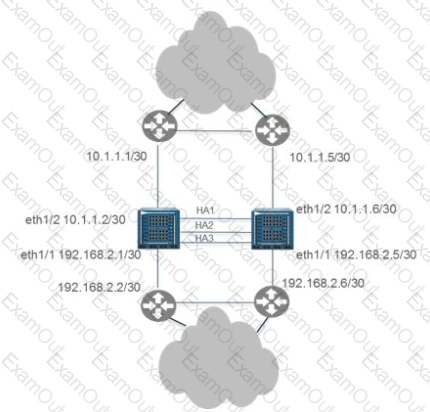
In the following scenario, Route-based firewall redundancy is deployed in a Data Center, which statement is true?
Why are containers uniquely suitable for whitelist-based runtime security?
When deploying VM series on NSX platform to support micro-segmentation, which statement is NOT correct?

