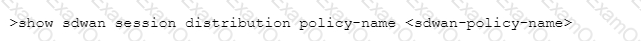In an HA pair running Active/Passive mode, over which interface do the dataplanes communicate?
Which two configuration elements can be used to prevent abuse of stolen credentials? (Choose two.)
Which three mechanisms are valid for enabling user mapping? (Choose three.)
What is the basis for purchasing Cortex XDR licensing?
What are two core values of the Palo Alto Network Security Operating Platform? (Choose two.}
What will a Palo Alto Networks next-generation firewall (NGFW) do when it is unable to retrieve a DNS verdict from the DNS cloud service in the configured lookup time?
Which three methods used to map users to IP addresses are supported in Palo Alto Networks firewalls? (Choose three.)
Which three platform components can identify and protect against malicious email links? (Choose three.)
Which three of the following actions must be taken to enable Credential Phishing Prevention? (Choose three.)
Which CLI command will allow you to view latency, jitter and packet loss on a virtual SD-WAN interface?
A)
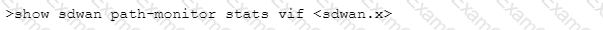
B)
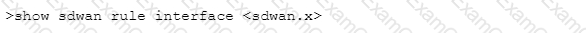
C)
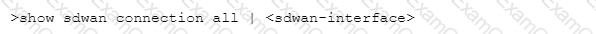
D)