A network engineer troubleshoots a VPN Phase 2 mismatch and decides that PFS (Perfect Forward Secrecy) needs to be enabled. What action should the engineer take?
After configuring an IPSec tunnel, how should a firewall administrator initiate the IKE phase 1 to see if it will come up?
A company requires that a specific set of ciphers be used when remotely managing their Palo Alto Networks appliances. Which profile should be configured in order to achieve this?
Users are intermittently being cut off from local resources whenever they connect to GlobalProtect. After researching, it is determined that this is caused by an incorrect setting on one of the NGFWs. Which action will resolve this issue?
A firewall engineer has determined that, in an application developed by the company's internal team, sessions often remain idle for hours before the client and server exchange any data. The application is also currently identified as unknown-tcp by the firewalls. It is determined that because of a high level of trust, the application does not require to be scanned for threats, but it needs to be properly identified in Traffic logs for reporting purposes.
Which solution will take the least time to implement and will ensure the App-ID engine is used to identify the application?
Which version of GlobalProtect supports split tunneling based on destination domain, client process, and HTTP/HTTPS video streaming application?
An administrator plans to deploy 15 firewalls to act as GlobalProtect gateways around the world. Panorama will manage the firewalls.
The firewalls will provide access to mobile users and act as edge locations to on-premises infrastructure. The administrator wants to scale the configuration out quickly and wants all of the firewalls to use the same template configuration.
Which two solutions can the administrator use to scale this configuration? (Choose two.)
Which two actions can the administrative role called "vsysadmin" perform? (Choose two)
An engineer reviews high availability (HA) settings to understand a recent HA failover event Review the screenshot below.
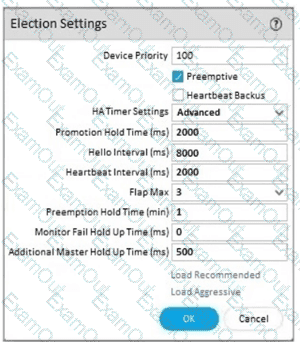
Which tuner determines how long the passive firewall will wart before taking over as the active firewall after losing communications with the HA peer?
An administrator has been asked to configure active/active HA for a pair of Palo Alto Networks NGFWs. The firewall use Layer 3 interfaces to send traffic to a single gateway IP for the pair.
Which configuration will enable this HA scenario?

