Which security profile should be used to classify malicious web content?
In which two Security Profiles can an action equal to the block IP feature be configured? (Choose two.)
Why should a company have a File Blocking profile that is attached to a Security policy?
Which license must an administrator acquire prior to downloading Antivirus updates for use with the firewall?
An administrator would like to protect against inbound threats such as buffer overflows and illegal code execution.
Which Security profile should be used?
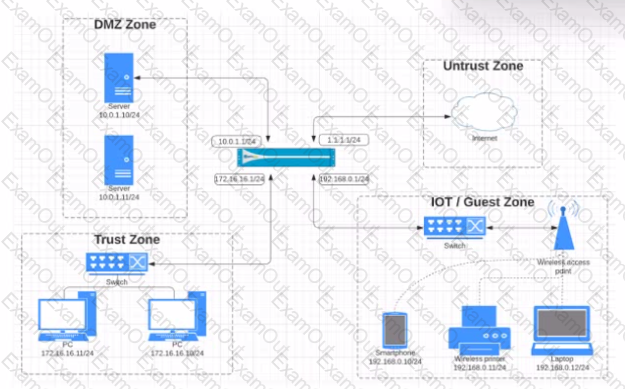
View the diagram. What is the most restrictive, yet fully functional rule, to allow general Internet and SSH traffic into both the DMZ and Untrust/lnternet zones from each of the lOT/Guest and Trust Zones?
A)

B)
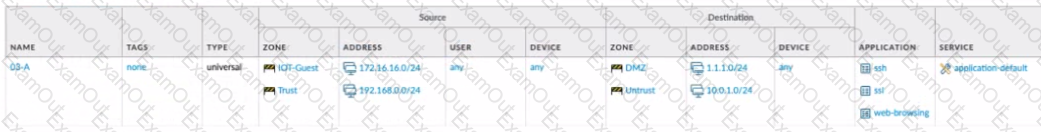
C)

D)

Which type of administrative role must you assign to a firewall administrator account, if the account must include a custom set of firewall permissions?
The CFO found a USB drive in the parking lot and decide to plug it into their corporate laptop. The USB drive had malware on it that loaded onto their computer and then contacted a known command and control (CnC) server, which ordered the infected machine to begin Exfiltrating data from the laptop.
Which security profile feature could have been used to prevent the communication with the CnC server?
Which three Ethernet interface types are configurable on the Palo Alto Networks firewall? (Choose three.)

