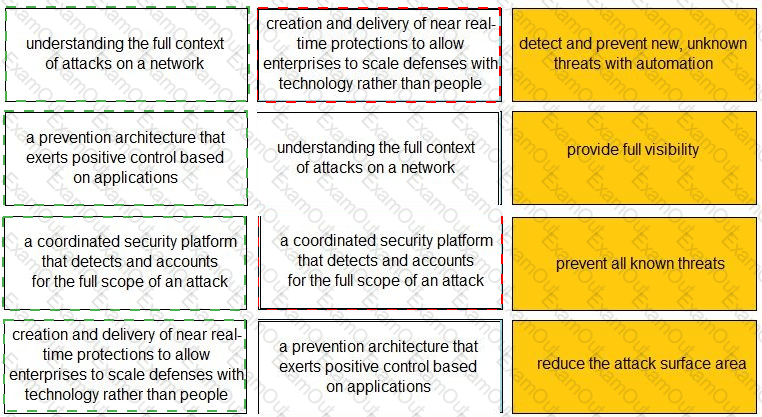
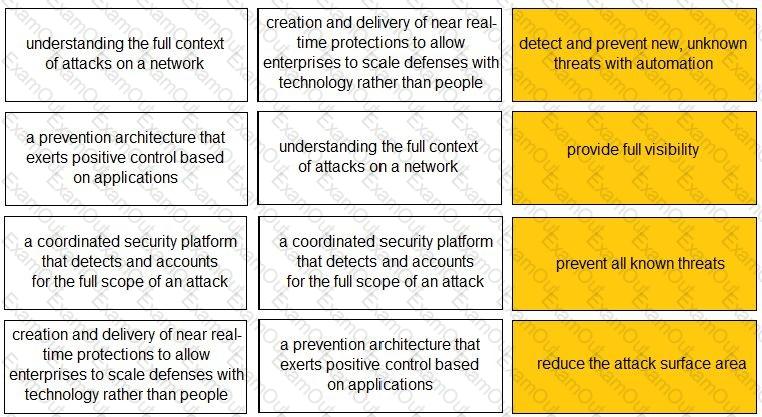
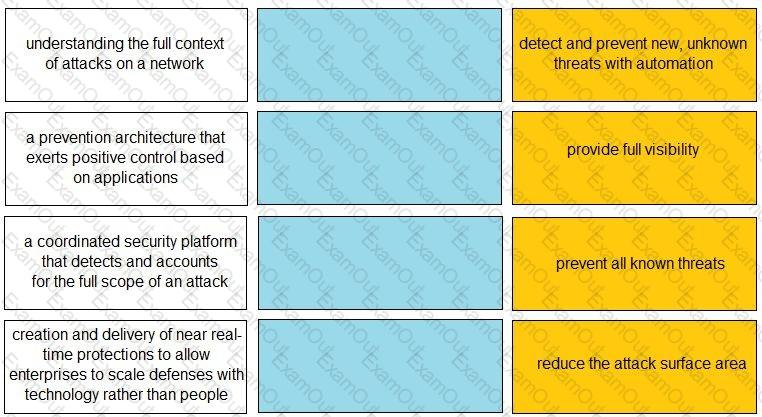
Match each description to a Security Operating Platform key capability.
At which layer of the OSI model are routing protocols defined?
Which Palo Alto subscription service identifies unknown malware, zero-day exploits, and advanced persistent threats (APTs) through static and dynamic analysis in a scalable, virtual environment?
Which model would a customer choose if they want full control over the operating system(s) running on their cloud computing platform?
What is the primary security focus after consolidating data center hypervisor hosts within trust levels?
During the OSI layer 3 step of the encapsulation process, what is the Protocol Data Unit (PDU) called when the IP stack adds source (sender) and destination (receiver) IP addresses?
Which IPsec feature allows device traffic to go directly to the Internet?
Which IoT connectivity technology is provided by satellites?
What are three benefits of the cloud native security platform? (Choose three.)
What is a key advantage and key risk in using a public cloud environment?