Which two configurations are required when creating deployment profiles to migrate a perpetual VM-Series firewall to a flexible VM? (Choose two.)
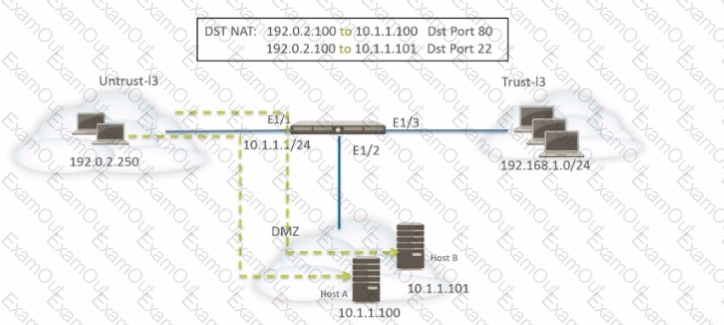
A network administrator is using DNAT to map two servers to one public IP address. Traffic will be directed to a specific server based on the application, where Host A (10.1.1.100) receives HTTP traffic and Host B (10.1.1.101) receives SSH traffic.
Which two sets of Security policy rules will accomplish this configuration? (Choose two.)
Which statement best demonstrates a fundamental difference between Content-ID and traditional network security methods?
Which feature is available in both Panorama and Strata Cloud Manager (SCM)?
Which two content updates can be pushed to next-generation firewalls from Panorama? (Choose two.)
What is the main security benefit of adding a CN-Series firewall to an existing VM-Series firewall deployment when the customer is using containers?
A firewall administrator wants to segment the network traffic and prevent noncritical assets from being able to access critical assets on the network.
Which action should the administrator take to ensure the critical assets are in a separate zone from the noncritical assets?
Which Cloud-Delivered Security Services (CDSS) solution is required to configure and enable Advanced DNS Security?
Which two SSH Proxy decryption profile configurations will reduce network attack surface? (Choose two.)
A network security engineer wants to forward Strata Logging Service data to tools used by the Security Operations Center (SOC) for further investigation.
In which best practice step of Palo Alto Networks Zero Trust does this fit?

