A customer has a requirement to terminate any Container from image topSecret:latest when a process named ransomWare is executed.
How should the administrator configure Prisma Cloud Compute to satisfy this requirement?
Review this admission control policy:
match[{"msg": msg}] { input.request.operation == "CREATE" input.request.kind.kind == "Pod" input.request.resource.resource == "pods"
input.request.object.spec.containers[_].securityContext.privileged msg := "Privileged"
}
Which response to this policy will be achieved when the effect is set to “block”?
Which Prisma Cloud policy type detects port scanning activities in a customer environment?
Which command should be used in the Prisma Cloud twistcli tool to scan the nginx:latest image for vulnerabilities and compliance issues?
A)
B)

C)
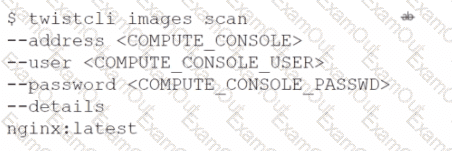
D)
Which two roles have access to view the Prisma Cloud policies? (Choose two.)
Who can access saved searches in a cloud account?
Which options show the steps required to upgrade Console when using projects?
Which of the below actions would indicate – “The timestamp on the compliance dashboard?
Which serverless cloud provider is covered by the "overly permissive service access" compliance check?
A customer has a requirement to restrict any container from resolving the name www.evil-url.com.
How should the administrator configure Prisma Cloud Compute to satisfy this requirement?

