Question:
In order to deploy Nutanix Files, which two networks should be created? (Choose two.)
Question:
An administrator has been asked to lock a file indefinitely. The lock can be explicitly removed only by authorized users.
Which configuration matches the requirements of this task?
An administrator has configured a share in Nutanix Files to support clients using Windows and Linux. A user on an Ubuntu client is unable to create any files. Which share configuration option should be updated?
An administrator has been tasked with troubleshooting a storage performance problem for a large database VM with the following configuration:
16 vCPU
64 GB RAM
One 50 GB native AHV virtual disk hosting the guest OS
Six 500 GB virtual disks containing database files connecting via iSCSI to a Nutanix volume group
One NIC for client connectivity
One NIC for iSCSI connectivity
In the course of investigating the problem, the administrator determines that the issue is isolated to large block-size I/O operations. What step should the administrator take to improve performance for the VM?
Exhibit:
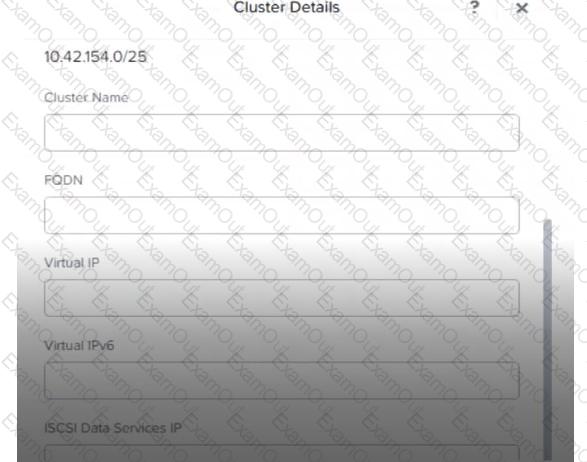
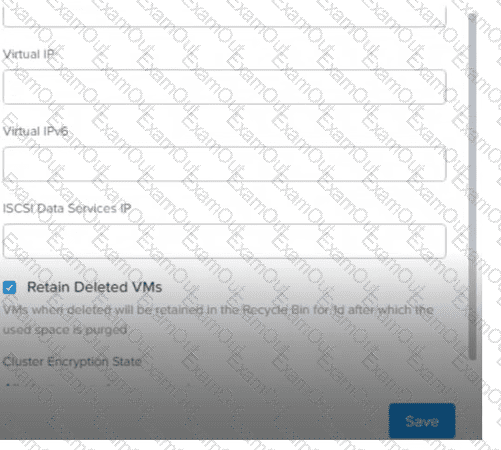
An administrator is enabling Nutanix Volumes for use with workloads within a Nutanix-based environment. Based on the exhibit, which field is required by Nutanix Volumes to be populated?
An administrator has been asked to protect a Nutanix Files instance between two sites supporting the following capabilities: 1-hour RPO, four recovery points, and cross-hypervisor capabilities. Which Nutanix feature matches the requirements?
An administrator needs to recover a previous version of a file or share.
Which Nutanix Files feature should the administrator enable to allow this?
Question:
What should be enabled for Windows clients when using the SMB protocol in a Nutanix Files deployment?
Question:
An administrator needs to allow replicatinguser data across file servers in different locations.
Which Nutanix Files feature should the administrator utilize?
An administrator wants to utilize File Analytics to send anomaly alerts and data to email recipients. Which statement describes when File Analytics will send the emails?

