Refer to the exhibit.
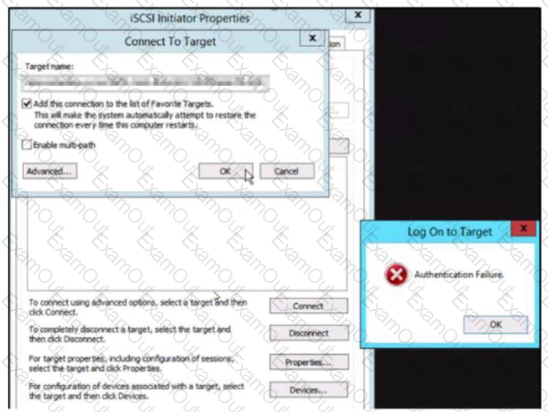
An administrator reports that a Volume Group (VG) is no longer accessible on their server.
Upon attempting to reconnect, an error is displayed , as shown in the exhibit.
Which condition would cause this error?
The Compliance department would like the administrator to have the ability to revert
documents to previous versions. How should the administrator facilitate this request?
An administrator is experiencing the following objects failure error message:
IAM service is not healthy
The object store domain entries appear grayed out in the user interface, as shown in the exhibit.
Which commands should the administrator execute to identify the failure source?
Which two statements are true about object counts in an object store?
An administrator installed a new Log Analyzer which collects data from physical endpoints
Data collected needs to be accessible and editable for three years after which the data must be
deleted to optimize storage consumption
Which setting should the administrator apply to meet these requirements?
An administrator manages a vSphere-based Nutanix cluster and has enabled Flash Mode for
extremely latency sensitive The administrator recently migrated several workloads from this
cluster to another cluster with higher CFU and migration, users complained about the VM
performance of the latency sensitive workloads.What must the administrator to resolve this issue?
Where can an administrator find the latency associated with a Files SMB Share?
A company uses a Nutanix 3-node cluster environment. In Prism Pro, the Capacity Runway
shows these capacity values:Max Capacity 6 TiB Effective Capacity 4 TiB
The company wants to upgrade the environment to use an RF3 container and also requires all
cluster nodes to be the same model.
What must the effective capacity of the Nutanix cluster be to support the new RF3 container?
During a recent audit the auditors discovered several shares that were unencrypted. To
remediate the audit item the administrator enabled Encrypt SMB3 Messages on the
accounting, finance, and facilities shares. After encryption was enabled several users have
reported that they are no longer able to access the shares
What is causing this issue?

