The following critical Availability Alert displays in prism Central:
The protection Policy PP-BCA-1HR includes a business critical application with a 1-hour snapshot frequency.
What is causing this issue?
Which two access protocols are supported by Files? (Choose two.)
An administrator needs to configure the cluster to ensure all VMs are capable of being restarted in the event of a host failure.
Which option provides this functionality?
An administrator is concerned that Prism will be inaccessible if Active Directory is unable to process logins. Which method should the administrator use to access the cluster in the event of this type of outage?
An administrator has two clusters: Site A and Site B.
Async DR is configured between the clusters as follows:
• Site A is the Primary Site
• Site B is the Secondary inactive Site, no VMs running
• Site A is fully in Production
• Site B used as Backup/Disaster Recovery
The customer wants to perform a planned failover between the sites.
How should the administrator accomplish this?
An administrator has Created a new windows VM and Given it to the user. The user states that only C drive mapping is visible within the windows OS.
What is causing this issue?
Refer to the exhibits.
An administrator has reported that a new VM is not performing well.
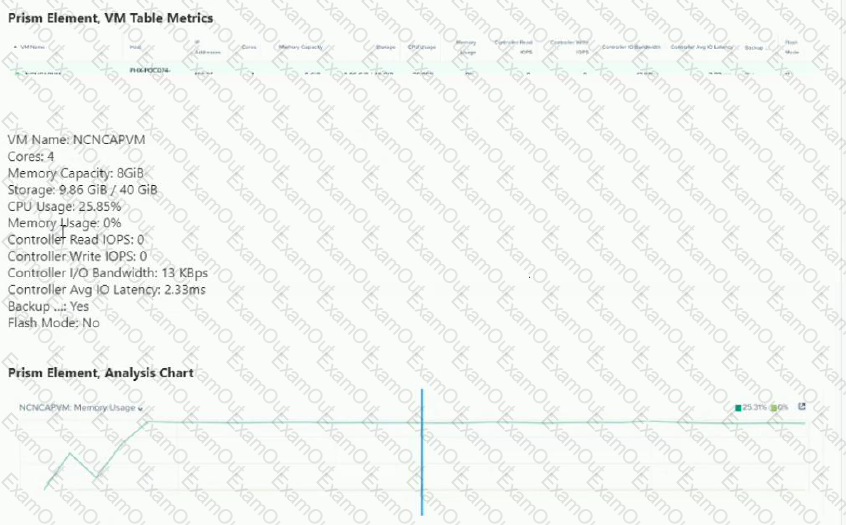
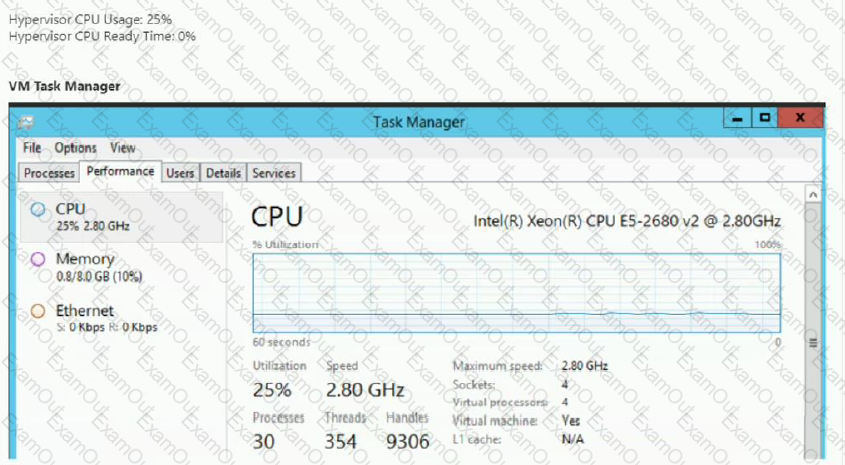
After analyzing the information presented in the exhibits, which option shows the best conclusion regarding this workload?
An administrator is deploying a new application to a Nutanix Enterprise Cloud. The application requires a security to prevent unauthorized access. The application also uses many non-standard ports that are unique to it. Security should not be changed for existing applications.
What should the administrator do to meet these requirement?
Which command should an administrator run from the CLI to view the uplink state of all AHV nodes in the cluster?


